Channels lising page
All videos archived of LiveOverflow

BOLN_B0qnZk | 08 Apr 2025
I met Jonathan in 2018 at the CCC when he was just 18 years old. Back then he referenced my videos which had a little bit of impact on his life. Now a lot of time has passed and in this interview I want to get to know Jonathan better. How did he get into hacking, founding of the CTF team perfect blue, working as a vulnerability researcher and ultimately transitioning into a new career. From Zero to Zero Day (2018): https://www.youtube.com/watch?v=xp1YDOtWohw Jonathan on Twitter: https://x.com/j0nathanj 00:00:00 - How we met 00:02:16 - Jonathan's early life 00:04:24 - Going to college as a teenager 00:18:52 - Meeting like-minded people in CTF 00:27:29 - Getting first VR internship at Checkpoint 00:32:34 - Creating opportunities through networking 00:43:40 - Working at Microsoft Security Response Center (MSRC) 00:51:23 - Mandatory military service 00:58:33 - Moving from hacking to building teams 01:08:26 - Joining a startup 01:17:56 - From Computers to Humans 01:23:20 - Summary =[ ❤️ Support / Ads ]= → My courses: https://www.hextree.io/ → My font: https://shop.liveoverflow.com/ → Support per video: https://www.patreon.com/join/liveoverflow → Support per month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → LinkedIn: https://www.linkedin.com/in/liveoverflow → X / Twitter: https://x.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Streaming: https://twitch.tv/LiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Blog: https://liveoverflow.com/

f0C3RH7baEw | 14 Mar 2025
An amazing event for aspiring German hackers is happening right now. I went to the finals in 2024, share a few impressions and tell you about this year's event. Learn hacking: https://www.hextree.io/ (ad) CSCG 2025 runs from 1. March 2025 until 1. May 2025 Rules: https://play.cscg.live/rules Die Hacking Meisterschaft: https://hacking-meisterschaft.de/ NFITS: https://nfits.de/spenden/ European Cybersecurity Challenge: https://ecsc.eu/ 00:00 - Intro DHM 2024 00:52 - CTF Teams vs. CSCG Teams 01:48 - Sponsor Challenges 03:04 - My CSCG History 04:18 - NFITS 05:06 - Die Deutsche Hacking Meisterschaft (DHM) 07:00 - Take the Opportunity! 07:47 - Outro =[ ❤️ Support ]= → My courses: https://www.hextree.io/ → My font: https://shop.liveoverflow.com/ → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → LinkedIn: https://www.linkedin.com/in/liveoverflow → X / Twitter: https://x.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Streaming: https://twitch.tv/LiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Blog: https://liveoverflow.com/

wVknDjTgQoo | 28 Feb 2025
When auditing code it's crucial to know about common issues. In this video we explore a Go issue that I was not aware of. Learn hacking on https://www.hextree.io/ (ad) 38c3 CTF - Fajny Jagazyn Wartości Kluczy: https://2024.ctf.link/internal/challenge/fb03748d-7e94-4ca2-8998-a5e0ffcbd761/ Unintended solution: https://msanft.foo/blog/hxp-38c3-web-fajny-jagazyn/ Challenge author writeup: https://hxp.io/blog/114/hxp-38C3-CTF-Fajny-Jagazyn-Wartoci-Kluczy/ VSCode Go debugger client code: https://github.com/golang/vscode-go/blob/39786ea90f18ab98f75d091b9a04367d1b1df82c/extension/src/debugAdapter/goDebug.ts#L1557 00:00 - Intro 00:20 - Go gjson vs json behavior 01:33 - Overview CTF challenge "Fajny Jagazyn Wartości Kluczy" 04:33 - Weird server setup? 05:55 - Arbitrary file read 07:00 - /proc filesystem trick 08:01 - Unintended solution 09:14 - What was the intended solution? 12:58 - Exploiting Go race condition 13:58 - Outro =[ ❤️ Support ]= → My courses: https://www.hextree.io/ → My font: https://shop.liveoverflow.com/ → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → LinkedIn: https://www.linkedin.com/in/liveoverflow → X / Twitter: https://x.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Streaming: https://twitch.tv/LiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Blog: https://liveoverflow.com/

SyTy1uZgx8E | 16 Oct 2024
"There are not that many people that do Android research [...] There is no lack of targets. If people would actually look, there is lots to it. The scope is huge." - This is a conversation with Kristoffer Blasiak about Google's Mobile Vulnerability Rewards Program (VRP). Learn Android Hacking (ad): https://hextree.io/hextree-x-google Mobile VRP: https://bughunters.google.com/about/rules/android-friends/6618732618186752/google-mobile-vulnerability-reward-program-rules 00:00 - Introducing Kristoffer and Mobile VRP 01:38 - What happens when you submit a bug 05:07 - Android app bug bounty opportunities 08:38 - "There is no lack of targets" 13:06 - The side-loading threat model 17:00 - Bugs in Android app vs. web app 23:30 - Hextree sponsored by Google =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

_ACCK0AUQ8Q | 29 Sep 2024
Want to learn more about hacking? Checkout our courses on https://www.hextree.io (ad) I have spent many hours looking at the webp vulnerability used in the 0day attack against iPhones. In the past videos we have seen why fuzzers have a hard time finding the issue, so I wanted to understand how this was discovered. And I think I have a good theory! Part 1: Huffman Tables https://youtu.be/lAyhKaclsPM Part 2: Fuzzing libwebp https://youtu.be/PJLWlmp8CDM Sources: https://citizenlab.ca/2023/09/blastpass-nso-group-iphone-zero-click-zero-day-exploit-captured-in-the-wild/ https://googleprojectzero.blogspot.com/2019/08/the-fully-remote-attack-surface-of.html https://googleprojectzero.blogspot.com/2020/01/remote-iphone-exploitation-part-1.html https://googleprojectzero.blogspot.com/2021/01/a-look-at-imessage-in-ios-14.html https://github.com/seemoo-lab/frida-scripts/blob/main/scripts/libdispatch.js https://googleprojectzero.blogspot.com/2021/12/a-deep-dive-into-nso-zero-click.html https://citizenlab.ca/2023/04/nso-groups-pegasus-spyware-returns-in-2022/ https://googleprojectzero.blogspot.com/2021/12/a-deep-dive-into-nso-zero-click.html https://github.com/libjxl/libjxl/blob/4b9dbde293f7f282b6952a02340300abfca2b184/lib/jxl/huffman_table.cc#L51 https://github.com/webmproject/libwebp/blob/7861947813b7ea02198f5d0b46afa5d987b797ae/src/dec/vp8l_dec.c#L86C3-L86C76 https://github.com/Tencent/mars/blob/9ab46e19ed3d4fcafe9d0de4b36547321f5ead83/mars/comm/windows/zlib/inftrees.h#L41 https://github.com/google/brunsli/blob/master/c/enc/jpeg_huffman_decode.h#L20 00:00 - Intro 01:18 - The iPhone Remote Attack Surface 02:49 - Targeting iMessage 04:04 - Dangerous Parsing / BlastDoor 06:53 - Image I/O and libwebp 08:11 - A Pattern of Image Vulnerabilities 09:28 - Huffman Tables are Everywhere! 10:50 - My Theory: known issue with enough.c 13:50 - Outro =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tv/LiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

fPt6fJDjKKM | 03 Sep 2024
During DEF CON and Black Hat, Google invited me to give a talk about Android hacking to students as part of init.g at the University Nevada, Las Vegas. In this talk I share my "trick" how to get into Android hacking and reverse engineering, which can also be adapted to any other topic. Learn android hacking (ad): https://app.hextree.io/map/android Watch my Vegas Vlog: https://www.youtube.com/watch?v=bhQ6FF3fCdA Article about the init.g event: https://www.unlv.edu/announcement/academics/google-sponsors-initgvegas-student-event-unlv-during-defcon =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

bhQ6FF3fCdA | 20 Aug 2024
My second time in Las Vegas for DEF CON and Black Hat. Lots has changed since I have been here 6 years ago. This trip was quite emotional for me and I am so grateful for the experience. Hope to meet you all again. Learn hacking (ad): https://app.hextree.io/ Buy our Faultier (US): https://1bitsquared.com/collections/embedded-hardware/products/faultier Google x Hextree Android Courses: https://www.hextree.io/hextree-x-google Raspberry Pi Hacking Challenge: https://www.hextree.io/rp2350 Embedded System Village: https://embeddedvillage.org/ My previous DEF CON 26 (6 years ago) Vlog: - https://youtu.be/B8saYocsI-U - https://www.youtube.com/watch?v=RXgp4cDbiq4 =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

PJLWlmp8CDM | 22 Jan 2024
A guide on how to do fuzzing with AFL++ in an attempt to rediscover the libwebp vulnerability CVE-2023-4863 that was used to hack iPhones. Want to learn hacking? Signup to https://hextree.io (ad) Buy my shitty font: https://shop.liveoverflow.com/ (ad) Watch webp Part 1: https://www.youtube.com/watch?v=lAyhKaclsPM Sudo Vulnerability Series: https://www.youtube.com/playlist?list=PLhixgUqwRTjy0gMuT4C3bmjeZjuNQyqdx Docker Video: https://www.youtube.com/watch?v=-YnMr1lj4Z8 OSS-Fuzz: https://github.com/google/oss-fuzz OSS-Fuzz libwebp coverage: https://storage.googleapis.com/oss-fuzz-coverage/libwebp/reports/20230901/linux/src/libwebp/src/utils/report.html AFLplusplus: https://github.com/AFLplusplus/AFLplusplus/blob/stable/docs/fuzzing_in_depth.md vanhauser's blog: https://www.srlabs.de/blog-post/advanced-fuzzing-unmasks-elusive-vulnerabilities vanhauser/thc on twitter: https://twitter.com/hackerschoice AFLpluslus Persistent Mode: https://github.com/AFLplusplus/AFLplusplus/blob/0c054f520eda67b7bb15f95ca58c028e9b68131f/instrumentation/README.persistent_mode.md Grab the code: https://github.com/LiveOverflow/webp-CVE-2023-4863 =[ ❤️ Support ]= Find out how you can support LiveOverflow: https://liveoverflow.com/support/ =[ 🐕 Social ]= → 2nd Channel: https://www.youtube.com/LiveUnderflow → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ Chapters: 00:00 - Intro 00:36 - How to Learn About Fuzzing? 02:36 - Setting Up Fuzzing With AFL++ 04:53 - My Docker Workflow for Fuzzing 06:35 - AFL++ Different Coverage Strategies 09:50 - Start the libwebp Fuzzing Campaign 11:58 - Adjusting the Fuzzer 13:45 - Why Don't We Find a Crash? 15:49 - Fuzzing with AFL++ Persistent Mode 19:47 - Persistent Mode Fuzzing Results 20:46 - Finding the Vulnerability in 8s

lAyhKaclsPM | 21 Dec 2023
Citizenlab discovered BLASTPASS, a 0day being actively exploited in the image format WebP. Known as CVE-2023-4863 and CVE-2023-41064, an issue in webp's build huffman table function can lead to a heap buffer overflow. This vulnerability is very interesting and I'm excited to share with you what I learned. Want to learn hacking? Signup to https://hextree.io (ad) Buy my shitty font: https://shop.liveoverflow.com/ (ad) WebP Fix Commit: https://chromium.googlesource.com/webm/libwebp/+/902bc9190331343b2017211debcec8d2ab87e17a Citizenlab: https://citizenlab.ca/2023/09/blastpass-nso-group-iphone-zero-click-zero-day-exploit-captured-in-the-wild/ Ben Hawkes: https://blog.isosceles.com/the-webp-0day/ Software Updates Apple https://support.apple.com/en-gb/106361 Chrome https://chromereleases.googleblog.com/2023/09/stable-channel-update-for-desktop_11.html Firefox https://www.mozilla.org/en-US/security/advisories/mfsa2023-40/ Android https://www.mozilla.org/en-US/security/advisories/mfsa2023-40/ Whose CVE is it Anyway? https://adamcaudill.com/2023/09/14/whose-cve-is-it-anyway/ References: 2014 bug introduction https://github.com/webmproject/libwebp/commit/f75dfbf23d1df1be52350b1a6fc5cfa6c2194499 https://www.youtube.com/watch?v=JsTptu56GM8 https://www.youtube.com/watch?v=B3y0RsVCyrw https://www.youtube.com/watch?v=EFUYNoFRHQI https://www.youtube.com/watch?v=iEm1NRyEe5c https://stackoverflow.com/questions/13804629/huffman-code-with-lookup-table https://web.archive.org/web/20230204211844/https://commandlinefanatic.com/cgi-bin/showarticle.cgi?article=art007 enough.c https://github.com/madler/zlib/blob/develop/examples/enough.c Thanks to: https://twitter.com/mistymntncop https://twitter.com/benhawkes Chapters: 00:00 - Intro to CVE-2023-4863 01:32 - Most Valuable Vulnerability? 03:02 - Heap Overflow Related to Huffman Trees 03:58 - Learning about Huffman Codes 06:24 - What are Huffman Tables? 10:24 - Hardcoded Table Sizes (enough.c) 12:21 - Code Walkthrough - BuildHuffmanTable() 13:04 - The code_lengths[] and count[] Arrays 15:14 - Difference Between Compression and Decompression! 17:04 - Outro =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

LxUAnZY_08o | 20 Nov 2023
Follow me down the rabbit hole into the wonderful world of IT security. Buy my terrible font (ad): https://shop.liveoverflow.com Learn hacking (ad): https://hextree.io Related Videos: https://www.youtube.com/watch?v=866olNIzbrk https://www.youtube.com/watch?v=lKzsNp4AveY Tweets: https://twitter.com/LiveOverflow/status/1720734431659376995 https://twitter.com/LiveOverflow/status/1720799912181284864 https://twitter.com/LiveOverflow/status/1721493232310214910 Understanding the Risks of Stolen Credentials: https://static.googleusercontent.com/media/research.google.com/en//pubs/archive/46437.pdf Chapters: 00:00 - Intro 00:40 - Security Terminology 01:38 - Direct Database Access 03:40 - Introducing a Security Boundary 05:36 - Typical Web Security Vulnerabilities 07:03 - Clear-text Passwords in Database 09:28 - Security Weakness vs. Vulnerability 11:05 - Effective Mitigations 13:03 - Useless Mitigations 16:37 - Summary: Vulnerability vs. Weakness 19:00 - Outro =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

lr1KuL8OmJY | 17 Oct 2023
Not every security issues can be fixed. There exist (what I call) "unfixable" bugs, where you can always argue and shift the goal posts. The idea is to only report these kind of issues to create an endless stream of bug bounty money! Buy my terrible font (ad): https://shop.liveoverflow.com Learn hacking (ad): https://hextree.io What is a vulnerability? https://www.youtube.com/watch?v=866olNIzbrk hackerone reports: https://hackerone.com/reports/812754 https://hackerone.com/reports/6883 https://hackerone.com/reports/223337 https://hackerone.com/reports/819930 https://hackerone.com/reports/224460 https://hackerone.com/reports/160109 https://hackerone.com/reports/557154 OWASP: https://owasp.org/www-community/controls/Blocking_Brute_Force_Attacks Chapters: 00:00 - Intro 00:30 - Denial of Service with loooong passwords 03:18 - Invalid vs. Valid DoS Reports 05:11 - Deployment Differences 06:54 - Denial of Service vs. Bruteforce Protection 09:27 - IP Rate-Limiting "fix" 12:06 - Locking User Accounts? 13:59 - The Circle of Unfixable Security Issues 15:25 - Vulnerability vs. Weakness 16:49 - The Cybersecurity Industry 19:03 - Conclusion: Cybersecurity vs. Hacking 21:34 - Outro =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

3zShGLEqDn8 | 19 Sep 2023
Let me explain to you what you can learn from these tweets. Did you know the name trick? Buy my terrible font (ad): https://shop.liveoverflow.com Learn hacking (ad): https://hextree.io Quote Tweet: https://twitter.com/avlidienbrunn/status/1697869590569582932 Original Tweet: https://twitter.com/Rhynorater/status/1696862832841916679 Critical Thinking Podcast: https://www.criticalthinkingpodcast.io/ XSS Origin Series: https://www.youtube.com/playlist?list=PLhixgUqwRTjyakFK7puB3fHVfXMinqMSi Chapters: 00:00 - Intro 00:37 - Tweets About Tricky XSS 01:24 - XSS Testbed Setup with php 03:45 - Exploring the XSS Context 05:24 - The window Object 06:46 - Tweet 1: Justin's XSS Explained 08:22 - Tweet 2: Mathias's Variant With Object 09:52 - Tweet 2: Mathias's Variant Creating Class 10:30 - The window.name Trick 12:00 - Closing Script Tag XSS 12:28 - Outro =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

9EY_9KtxyPg | 29 Aug 2023
Let's explore the "most exciting" CPU vulnerability affecting Zen2 CPUs from AMD. Watch part 1 about fuzzing: https://www.youtube.com/watch?v=neWc0H1k2Lc buy my font (advertisement): https://shop.liveoverflow.com/ This video is sponsored by Google: https://security.googleblog.com/2023/08/downfall-and-zenbleed-googlers-helping.html Original Zenbleed Writeup: https://lock.cmpxchg8b.com/zenbleed.html Grab the code: https://github.com/google/security-research/tree/master/pocs/cpus/zenbleed cvtsi2ss: https://www.felixcloutier.com/x86/cvtsi2ss.html AMD Security Bulletin: https://www.amd.com/en/resources/product-security/bulletin/amd-sb-7008.html RIDL Video: https://www.youtube.com/watch?v=x_R1DeZxGc0 Tavis Ormandy: https://twitter.com/taviso Chapters: 00:00 - Intro 02:27 - zenleak.asm Patterns 03:56 - The C Exploit Code 05:20 - Assembly Generation with Compiler Preprocessor 07:40 - What are XMM and YMM Registers? 11:56 - Zenbleed: Trigger Merge Optimization 14:28 - Register File & Register Allocation Table 16:39 - Register Renaming 17:55 - Speculative Execution 18:55 - vzeroupper and SSE & AVX History 21:22 - Zenbleed Explanation 23:55 - How to fix Zenbleed? =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

neWc0H1k2Lc | 18 Aug 2023
How did Tavis Ormandy fuzz CPUs to discover Zenbleed? In this video we learn about the techniques to make this work! buy my font (advertisement): https://shop.liveoverflow.com/ This video is sponsored by Google: https://security.googleblog.com/2023/08/downfall-and-zenbleed-googlers-helping.html Original Zenbleed Writeup: https://lock.cmpxchg8b.com/zenbleed.html AMD Security Bulletin: https://www.amd.com/en/resources/product-security/bulletin/amd-sb-7008.html Tavis Ormandy: https://twitter.com/taviso Sudoedit Exploit Series: https://www.youtube.com/playlist?list=PLhixgUqwRTjy0gMuT4C3bmjeZjuNQyqdx Documented Intel Performance Counters: https://perfmon-events.intel.com/skylake_server.html RIDL Video: https://www.youtube.com/watch?v=x_R1DeZxGc0 Chapters: 00:00 - Intro 01:22 - Zenbleed Proof of Concept 03:06 - Tavis Ormandy 04:18 - How Fuzzing Works 06:31 - CPU Performance Counters 11:06 - Detect Bugs with "Oracle Serialization" 15:09 - Fuzzing and Discovering Zenbleed 18:46 - Outro =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

-X03UKo_obE | 01 Aug 2023
I attended droidcon Berlin 2023 and interviewed some developers about what they know about Android security. Thanks again to everybody who answered my questions, and thanks Egidijus for the dcbln23 ticket. Buy the terrible font (advertisement): https://shop.liveoverflow.com/ Watch my security conference vlog: https://www.youtube.com/watch?v=E9kz6RQu9Oc&list=PLhixgUqwRTjw6IUB0ozIglXYRH1dPbEkw&index=2 Egidijus on Twitter: https://twitter.com/AegisLil droidcon: https://www.droidcon.com/events/droidcon-berlin-2023/ Chapters: 00:00 - Intro 00:37 - Meet Egidijus 00:57 - The Plan for Today 02:00 - Developer Interviews 05:54 - How To Become a Security Researcher? 07:24 - Conclusion After Interviews 09:21 - My Conference Experience 10:55 - Conference Day 2 13:30 - Conference Day 3 16:34 - Some Final Thoughts =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

duLJUpptSik | 22 Jul 2023
Let's talk about a "security flaw in hospital software that allows full access to medical devices". This issue was disclosed on LinkedIn and included a full exploit code. Let's use this app as an example on how to find a macOS privilege escalation and learn how local root exploits can work. Print BINGO sheet: https://twitter.com/liveoverflow/status/1682650394227351552 Sources: Original LinkedIn Post: https://web.archive.org/web/20230424004137/https://www.linkedin.com/posts/jeanpereira00_sicherheitsl%C3%BCcke-in-krankenhaus-software-activity-7055185115584303104-2eZr The Exploit code: https://0day.today/exploit/38531 "The project has been deprecated for 2 years. Version 1.0.0-beta has been an EOL for at least 5 years" - developer statement: https://twitter.com/tehkapa/status/1650059269939552256 My references finding priv esc issues in macOS apps: https://github.com/cure53/Publications/blob/master/summary-report_tunnelbear.pdf https://github.com/cure53/Publications/blob/master/summary-report_tunnelbear_2018.pdf https://github.com/cure53/Publications/blob/master/summary-report_tunnelbear_2019.pdf https://github.com/cure53/Publications/blob/master/pentest-report_IVPN.pdf Help me pay for any legal trouble in case somebody wants to sue me (advertisement): https://shop.liveoverflow.com/ Chapters: 00:00 - Intro: Practice Research with Existing Issues 01:45 - HospitalRun Functionality 03:07 - What is a Local Root Exploit? 05:49 - Typical macOS Priviledge Escalation Issues 09:23 - Looking for Priviledged Helper in HospitalRun 10:10 - My Experience in finding Local Root Exploits on macOS 11:46 - Threat Modeling and Common Deployments 13:11 - Was this an April Fools Joke? 14:18 - Analysing and Cleaning Up The Exploit Code 17:51 - Reading Comments on LinkedIn 19:29 - BINGO! =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

nxlm7pIvMdg | 13 Jul 2023
Sergey Toshin tells us the story of how he became a top Android bug hunter and how he finds critical vulnerabilities. He also shows us a really cool vulnerability found in the Google Android Snapseed app. I didn't know this crazy attack vector exists! Start Android Bug Hunting Here! Google App Scan Results: https://bughunters.google.com/report/targets/290590452 Google Mobile VRP: https://bughunters.google.com/about/rules/6618732618186752/google-mobile-vulnerability-reward-program-rules Oversecured Blog: https://blog.oversecured.com/ Verify the output of tools: https://bughunters.google.com/learn/improving-your-reports/avoiding-mistakes/5981856648134656/verify-the-output-of-the-tools More Bug Bounty Videos: https://www.youtube.com/playlist?list=PLhixgUqwRTjxKYsPTegCyL5adZaq5eILt More Mobile Security: https://www.youtube.com/playlist?list=PLhixgUqwRTjxHFDl0OykeqZ-VvnClfDpT Chapters: 00:00 - Intro 00:57 - Meet Sergey Toshin (Oversecured) 02:51 - How Oversecured Started 04:42 - Verify The Output of Tools! 07:17 - First Look at Vulnerability 09:58 - 1. Explained: Android Intents 11:25 - 2. Explained: Content Providers 12:51 - 3. Explained: App Permissions 13:34 - Exploit Walkthrough 16:17 - Proof of Concept and Report 17:15 - Android VRP Rewards 18:32 - Start Hunting for Bugs in Google Apps! =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

HUtkW2gjC8Q | 03 Jul 2023
I stumbled over a weird HTML behavior on Twitter and started to investigate it. Did I just stumble over a generic HTML Sanitizer bypass? Get my handwritten font https://shop.liveoverflow.com (advertisement) Checkout our courses on https://hextree.io (advertisement) The Tweet: https://twitter.com/MRCodedBrain/status/1662701541680136195 Google XSS: https://www.youtube.com/watch?v=lG7U3fuNw3A HTML Spec: https://html.spec.whatwg.org/multipage/parsing.html#parse-error-invalid-first-character-of-tag-name Chapters: 00:00 - Intro 01:09 - Sanitizing vs. Encoding 02:32 - Developing HTML Sanitizer Bypass 05:03 - Attacking DOMPurify 07:08 - Attacking Server-side Sanitizer 08:31 - HTML Parse Error Specification 10:08 - Potential Impact 11:55 - hextree.io =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

uOvizKc1WZY | 22 Jun 2023
Every year Google celebrates the best security issues found in Google Cloud. This year we take a look at the 7 winners to see if we could have found these issues too. Will I regret not having hacked Google last year? This video is sponsored by Google VRP: Follow GoogleVRP Twitter: https://twitter.com/GoogleVRP The GCP Prize Winners of 2022: https://security.googleblog.com/2023/06/google-cloud-awards-313337-in-2022-vrp.html 1. Prize - $133,337: Yuval Avrahami https://unit42.paloaltonetworks.com/gke-autopilot-vulnerabilities/ 2. Prize - $73,331: Sivanesh Ashok and Sreeram KL https://blog.stazot.com/ssh-key-injection-google-cloud/ 3. Prize - $31,337: Sivanesh Ashok and Sreeram KL https://blog.stazot.com/auth-bypass-in-google-cloud-workstations/ 4. Prize - $31,311: Sreeram KL and Sivanesh Ashok https://blog.geekycat.in/client-side-ssrf-to-google-cloud-project-takeover/ 5. Prize - $17,311: Yuval Avrahami and Shaul Ben Hai https://www.paloaltonetworks.com/resources/whitepapers/kubernetes-privilege-escalation-excessive-permissions-in-popular-platforms Talk: https://www.youtube.com/watch?v=PGsJ4QTlKlQ 6. Prize - $13,373: Obmi https://obmiblog.blogspot.com/2022/12/gcp-2022-few-bugs-in-google-cloud-shell.html 7. Prize - $13,337: Bugra Eskici https://bugra.ninja/posts/cloudshell-command-injection/ Previous Winners: GPC Prize 2019: https://www.youtube.com/watch?v=J2icGMocQds GPC Prize 2020: https://www.youtube.com/watch?v=g-JgA1hvJzA GPC Prize 2021: https://www.youtube.com/watch?v=GvO2Xtx8p9w Chapters: 00:00 - Intro 01:28 - Python Command Injection (Prize 7) 03:01 - XSS, CSRF and NEL Backdoor (Prize 6) 07:04 - Excessive Permissions in k8s DaemonSets (Prize 5) 09:13 - SSRF auth Authorization Token (Prize 4) 10:46 - OAuth Issue (Prize 3) 12:07 - SSH authorized_key Injection (Prize 2) 14:45 - Kubernetes Engine Privilege Escalation (Prize 1) 18:11 - Discussing the Winner 19:25 - What did I learn from the GCP 2022? 20:51 - Outro =[ ❤️ Support ]= Get my handwritten font https://shop.liveoverflow.com (advertisement) Checkout our courses on https://hextree.io (advertisement) Support these videos: https://liveoverflow.com/support/ → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

lLjgskJgaRU | 11 Jun 2023
I stumbled over some WordPress code involving caching. Immediately I had this idea about MD5 collision and how this could affect the implemented logic. I started going down a rabbit hole exploring the feasibility and eventually setting up a PHP debug environment. Only to realize that the idea was flawed from the start. So while this ends up being failed security research, we still learn a lot along the process. Get my handwritten font https://shop.liveoverflow.com (advertisement) Checkout our courses on https://hextree.io (advertisement) Support these videos: https://liveoverflow.com/support/ --- get_page_by_path: https://developer.wordpress.org/reference/functions/get_page_by_path/ Hash Collision Overview: https://github.com/corkami/collisions#fastcoll-md5 MD5 Collision Demo: https://www.mscs.dal.ca/~selinger/md5collision/ Is there an ASCII only MD5 hash collision? https://twitter.com/LiveOverflow/status/1664280653519810563 Wordpress docker image with xdebug: https://github.com/wpdiaries/wordpress-xdebug Debugging wordpress with xdebug: https://www.wpdiaries.com/wordpress-with-xdebug-for-docker/ What is a Server? https://www.youtube.com/watch?v=VXmvM2QtuMU --- Chapters: 00:00 - Intro 00:36 - Finding the Research Topic 03:03 - Dumb Ideas Are NOT a Problem 03:40 - "What happens with a MD5 Hash Collision?" 04:38 - MD5 Hash Collision Feasibility 09:25 - WordPress Development Environment 11:18 - Debugging PHP 12:57 - Configuring xdebug 14:42 - Realizing the Research Idea was Flawed 15:58 - What we learned from the failed research 17:10 - hextree.io 17:47 - Outro =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

2vAr9K5chII | 31 May 2023
Lots of #bugbountytips get posted on twitter, but some of them are ... weird. Let's explore the technical details of one tweet to understand where this tip came from, why this tip was wrong, and eventually learn about the real underlaying vulnerability. This is a surprising turn of events! advertisement: Get my handwritten font https://shop.liveoverflow.com Checkout our courses on https://hextree.io Authentication Bypass Due to Empty Where Clause and SQL Injection in CodeIgniter https://liveoverflow.com/authentication-bypassing-in-codeigniter-due-to-empty-where-clause/ Thank you Eslam for sharing the details with us! Follow Eslam on Twitter: https://twitter.com/eslam3kll The #bugbountytips tweet: https://twitter.com/beginnbounty/status/1526795822687346688 Eslam's old post: https://infosecwriteups.com/authentication-bypass-using-root-array-4a179242b9f7 Eslam's new blog: https://eslam3kl.gitbook.io/blog/bug-hunting-findings/authentication-bypass-using-empty-parameters. Day[0] Podcast: https://dayzerosec.com/vulns/2022/03/28/an-odd-authentication-bypass.html Chapters: 00:00 - Intro 00:41 - The bugbountytips Tweet 01:21 - The Original Blog 02:43 - Talking to Eslam about the Happy Accident 04:36 - Digging Deeper 05:39 - Researching Login Code with Codeigniter 06:54 - Example Vulnerable Login Code 08:08 - Improving the Writeup 09:18 - Surprise SQL Injection! 11:37 - Conclusion 12:31 - hextree =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

nDiXoeeAMWM | 22 May 2023
Follow us on: https://twitter.com/hextreeio https://www.hextree.io/ Get my bad font (advertisement): https://shop.liveoverflow.com/ Financials 2019: https://www.youtube.com/watch?v=kLixcdwHrFM Chapters: 00:00 - Intro 01:41 - Total Revenue 2022 03:37 - Total Expenses 2022 04:49 - Lost -$4000? 06:05 - Financials Summary 07:42 - Top Patreon Supporters 08:59 - I Don't Want To Be An Influencer 09:56 - Change LiveOverflow Videos? 12:08 - More Sponsored Videos? 14:50 - My Alternative To YouTube! 17:28 - I Should Close The LiveOverflow Business 20:11 - My Problem With Selling Courses 24:08 - How To Sell Courses? 25:47 - My Last Attempt: hextree.io 20:59 - Hextree Roadmap 32:37 - Conclusion and Summary =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

VbNPZ1n6_vY | 11 May 2023
After we explored attacking LLMs, in this video we finally talk about defending against prompt injections. Is it even possible? Buy my shitty font (advertisement): shop.liveoverflow.com Watch the complete AI series: https://www.youtube.com/playlist?list=PLhixgUqwRTjzerY4bJgwpxCLyfqNYwDVB Language Models are Few-Shot Learners: https://arxiv.org/pdf/2005.14165.pdf A Holistic Approach to Undesired Content Detection in the Real World: https://arxiv.org/pdf/2208.03274.pdf Chapters: 00:00 - Intro 00:43 - AI Threat Model? 01:51 - Inherently Vulnerable to Prompt Injections 03:00 - It's not a Bug, it's a Feature! 04:49 - Don't Trust User Input 06:29 - Change the Prompt Design 08:07 - User Isolation 09:45 - Focus LLM on a Task 10:42 - Few-Shot Prompt 11:45 - Fine-Tuning Model 13:07 - Restrict Input Length 13:31 - Temperature 0 14:35 - Redundancy in Critical Systems 15:29 - Conclusion 16:21 - Checkout LiveOverfont Hip Hop Rap Instrumental (Crying Over You) by christophermorrow https://soundcloud.com/chris-morrow-3 CC BY 3.0 Free Download / Stream: http://bit.ly/2AHA5G9 Music promoted by Audio Library https://youtu.be/hiYs5z4xdBU =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

h74oXb4Kk8k | 27 Apr 2023
In this video we explore various prompt tricks to manipulate the AI to respond in ways we want, even when the system instructions want something else. This can help us better understand the limitations of LLMs. Get my font (advertisement): https://shop.liveoverflow.com Video Part 1: https://www.youtube.com/watch?v=Sv5OLj2nVAQ The OpenAI API cost is pretty high, thus if you want to play the game, use the OpenAI Playground with your own account: https://platform.openai.com/playground?mode=chat Chapters: 00:00 - Intro 00:39 - Content Moderation Experiment with Chat API 02:19 - Learning to Attack LLMs 03:06 - Attack 1: Single Symbol Differences 03:51 - Attack 2: Context Switch to Write Stories 05:20 - Attack 3: Large Attacker Inputs 06:31 - Attack 4: TLDR Backdoor 08:27 - "This is just a game" 08:56 - Attack 5: Different Languages 09:19 - Attack 6: Translate Text 10:30 - Quote about LLM Based Games 11:11 - advertisement shop.liveoverflow.com =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

Sv5OLj2nVAQ | 14 Apr 2023
How will the easy access to powerful APIs like GPT-4 affect the future of IT security? Keep in mind LLMs are new to this world and things will change fast. But I don't want to fall behind, so let's start exploring some thoughts on the security of LLMs. Get my font (advertisement): https://shop.liveoverflow.com Building the Everything API: https://www.youtube.com/watch?v=M2uH6HnodlM Injections Explained with Burgers: https://www.youtube.com/watch?v=WWJTsKaJT_g Chapters: 00:00 - Intro 00:41 - The OpenAI API 01:20 - Injection Attacks 02:09 - Prevent Injections with Escaping 03:14 - How do Injections Affect LLMs? 06:02 - How LLMs like ChatGPT work 10:24 - Looking Inside LLMs 11:25 - Prevent Injections in LLMs? 12:43 - LiveOverfont ad =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

GbMHAaB0uI0 | 01 Apr 2023
Copilot, ChatGPT and other AI models become a threat to hackers. We rely on insecure code, but when all developers moved over to code generated by AI, we will lose our job. We need to act fast! Join the https://rAIsistance.com now! Here is the three step plan to secure our future: 1. Find coding tutorials or code on GitHub 2. Modify the code and introduce bugs 3. Add comments and text stating that the code is secure Once the next generation AI was trained on this tainted dataset, developers will start to write more insecure code and our jobs are safe. Get my font (advertisement): https://shop.liveoverflow.com This video is satire and a joke (1. April) Chapters: 00:00 - The rAistance! 00:32 - AI is a Threat to Hacking 01:26 - The Mission 02:50 - Opt-In AI Regulations 03:14 - START NOW! 03:50 - Outro =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

jUZjQlcAV94 | 29 Mar 2023
CSCG: https://cscg.de/ Donate to NFITS: https://nfits.de/spenden/ ECSC: https://ecsc.eu/ Intro Rev Video: https://www.youtube.com/watch?v=28JHPOUZvDw Intro Pwn Video: https://www.youtube.com/watch?v=hhu7vhmuISY Get started with hacking https://liveoverflow.com/faq/get-started-with-hacking/ =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

nyg2W5KUNVQ | 20 Mar 2023
In the news, cybercrime is often mentioned in connection to "hacking". Also when accounts get stolen, people say "my account got hacked". But is this really hacking? How does cybercrime actually look like? LiveOverfont (advertisement): https://shop.liveoverflow.com Protect yourself from phishing: https://www.youtube.com/watch?v=NWtm4X6L_Cs Checkout some hacking videos: Total beginner: https://www.youtube.com/watch?v=2TofunAI6fU Boomer Gamers: https://www.youtube.com/watch?v=p8OBktd42GI Zoomer Gamers: https://www.youtube.com/watch?v=Ekcseve-mOg Developers: https://www.youtube.com/watch?v=-YnMr1lj4Z8 Bughunters: https://www.youtube.com/watch?v=eQFbG6CwwdI Hackers: https://www.youtube.com/watch?v=yrCXamnX9No Haxx0rs: https://www.youtube.com/watch?v=qA8KB6KndrE Chapters: 00:00 - Intro 00:34 - Site Walkthrough 01:58 - Cybercrime Organization 02:41 - The Cybercrime Recruitment Funnel 03:44 - Website Builder Services 04:45 - How the Money Flows 05:45 - Cybercrime is like a Business! 07:37 - Hacking vs. Cybercrime 09:00 - How to Learn Hacking 09:39 - Report Phishing Sites 10:02 - shop.liveoverflow.com advertisement =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

DFAdG9o0sTw | 11 Mar 2023
While auditing a VSCode Extension + Language Server I noticed something interesting. This turned into the research question "can we attack the extension from the browser?". After a bit of preliminary research I decided to do it again on stream, and eventually made this video. This is how security research can look like. What is a Server? https://www.youtube.com/watch?v=VXmvM2QtuMU What is a Protocol? https://www.youtube.com/watch?v=d-zn-wv4Di8 GitLab 11.4.7 RCE https://www.youtube.com/watch?v=LrLJuyAdoAg Live Stream: https://www.youtube.com/watch?v=jc7S6TtLK_c My Font (advertisement): https://shop.liveoverflow.com/ Chapters: 00:00 - Why Security Research? 01:23 - What is a Language Server? 02:53 - Setup Example Code 04:00 - RCE in VSCode Extension? 05:25 - The Language Server Code 06:29 - Researching Communication 11:13 - Can a Browser Attack the VSCode Extension? 13:54 - Research Results 15:40 - Ad n' Outro =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

3HSnDsfkJT8 | 03 Mar 2023
There exists a pretty cool teleport hack that I couldn't discover myself. So I decided to steal it and share it with you all! Minecraft:HACKED Playlist https://www.youtube.com/playlist?list=PLhixgUqwRTjwvBI-hmbZ2rpkAl4lutnJG Purchase LiveOverfont (advertisement): https://shop.liveoverflow.com Paper Source Code: https://github.com/PaperMC/Paper/tree/1.19.2 Community Showcase: Jorian, EnderKill98, Shrecknt Chapters: 00:00 - La Casa De Papel 00:53 - Reach Hack Recap 01:59 - The Vault Challenge 03:43 - Code Review of handleMovePlayer() 05:45 - Logging Packets from Cheaters 07:03 - Reverse Engineering the Teleport Hack 09:01 - Debugging the Movement Code 11:58 - Self-reflection: Why did I not find this? 13:40 - The End of Minecraft:HACKED 15:06 - Community Showcase: Jorian, EnderKill98, Shrecknt =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

32KKwgF67Ho | 17 Feb 2023
What is a secure "tunnel"? When I started to learn about computers the name confused me. I couldn't imagine how it works on a technical level. In this video we build upon knowledge from the previous videos, to develop an intuition for what a tunnel, VPN or proxy is. LiveOverfont (advertisement): https://shop.liveoverflow.com 1. Server Explained: https://www.youtube.com/watch?v=VXmvM2QtuMU 2. Protocol Explained: https://www.youtube.com/watch?v=d-zn-wv4Di8 3. Computer Networking: https://www.youtube.com/watch?v=6G14NrjekLQ Grab the forwarder.py code: https://gist.github.com/LiveOverflow/8325c58ecf5b385a2028f3174ee47c18 Chapters: 00:00 - Intro and Background 00:53 - Networking as a Blackbox 01:24 - forwarder.py: Forward Data via Networking 02:43 - Using forwarder.py as a Proxy 04:31 - xor_forwarder.py: Forward "XOR Encrypted" Data via Networking 06:58 - The VPN Blackbox 08:10 - VPNs Forward Entire Packets 10:01 - Virtual Network Cards with TUN/TAP 12:34 - Outro =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

Wz1EI7NnUTo | 31 Jan 2023
In this video we investigate the comments' claims that there exists an arbitrary velocity exploit in minecraft. We look into the code and see if that is true. LiveOverfont (advertisement): shop.liveoverflow.com Watch the full Minecraft:HACKED playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjwvBI-hmbZ2rpkAl4lutnJG The Duper Trooper: Minecraft Insta-Kill Hack!! https://www.youtube.com/watch?v=itFLgGPkN8U Community Showcase: TudbuT's SeedOverlay Episode 20: 00:00 - Intro 00:24 - Snowball Challenge 01:56 - Minecraft Velocity Research 04:00 - deltaMovement Usage 04:50 - jumpFromGround() on vanilla 05:55 - BowBomb Implementation 06:42 - jumpFromGround() on paper 07:19 - Low TPS Exploit 08:41 - Community Showcase: TudbuT SeedOverlay 10:35 - SeedOverlay Code 13:41 - Outro =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

6G14NrjekLQ | 01 Jan 2023
LiveOverfont (advertisement): http://shop.liveoverflow.com/ In this video I try to explain computer networking with pieces of paper. This hopefully explains why in some universities the OSi layer model is taught. While I find the OSI model kinda useless, "thinking in layers" is extremely important. Blackboxes of layers allow us to focus on what matters, and ignore anything else. HTTP Desync Attack Explained With Paper: https://www.youtube.com/watch?v=dnyL7EKbRRk HTTP Request Smuggling - False Positives: https://www.youtube.com/watch?v=7wq2e2nxa38 Chapters: 00:00 - Intro 00:42 - Send Data Between Computers (Physical Layer) 01:31 - Find The Correct Computers (IP Layer) 04:24 - Identify The Target Program (TCP Layer) 06:40 - Think in Blackboxes! 07:24 - TCP Layer Blackbox 08:32 - Linux Kernel Implementing The Layers 09:54 - netcat Example 10:30 - Looking at Packet with Wireshark 11:04 - Layers are Everywhere (Phone Call) 11:49 - Hacking with Blackboxes 13:11 - Outro 13:28 - LiveOverfont Ad =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Streaming: https://twitch.tvLiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

TAUrzkOYLUk | 23 Dec 2022
LiveOverfont (advertisement): shop.liveoverflow.com Everybody told me the cat coordinate exploit/leak was already known. However this does not seem to be true, I tested it by logging packets. Cat Coordinate Exploit 1.19.2: https://www.youtube.com/watch?v=Gi2PPBCEHuM Watch the full playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjwvBI-hmbZ2rpkAl4lutnJG After I made the video I realized I should have showcased this project: Minecraft Packet Monitor: https://github.com/Heath123/pakkit Community Showcase: TudbuT - https://youtu.be/ipTqARwCmEE 7H3, MonkeySaint Episode 19: 00:00 - Intro 00:38 - 2b2t Tamed Animal Coordinate Leak 01:20 - Experiment Setup 02:32 - Packet Logging Experiment 04:55 - Experiment Conclusion 06:15 - Fixing the Coordinate Leak 06:58 - Community Showcase =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → LiveStreams: https://twitch.tv/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

d-zn-wv4Di8 | 13 Dec 2022
The term "protocol" can be really confusing. In this video I try to explain to my former self what it means to have a protocol. Chapters: 00:00 - Intro and Motivation 00:28 - "Protocol" Word Definition 01:48 - The HTTP Protocol 02:42 - RFC 9112 HTTP/1.1 06:35 - Web APIs are Protocols 07:50 - RFC 9293 TCP 11:02 - What Is a TCP Port? 12:30 - Why Is TCP Working This Way? 13:45 - Hardware Protocol UART 16:16 - Protocol: Rules for Communication 17:20 - Protocols for Hackers 17:52 - Outro =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → TikTok: https://www.tiktok.com/@liveoverflow_ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

ukKfAV4Ap6o | 04 Dec 2022
I tried to use OpenAI's ChatGPT on stream to create a minecraft hack. Let's see how it goes. Watch the Minecraft:HACKED Playlist here: https://www.youtube.com/playlist?list=PLhixgUqwRTjwvBI-hmbZ2rpkAl4lutnJG Chapters: 00:00 - Intro 00:59 - How To Create a Minecraft Mod? 08:22 - Can You Write a FlyHack? 09:35 - Testing the FlyHack 10:33 - How to Bypass The Anti-Fly Check? 15:03 - The AI Explains Mixins 20:06 - Helping the AI to find Anti-Fly Bypass 26:45 - Implementing AI's Anti-Fly Bypass 33:43 - AI Suggests to Intercept Packets 41:10 - Arguing with AI about Server's isFloating Check 47:29 - Anti-Human Bypass Plugin 52:09 - Ask AI about Different Minecraft Exploits 54:47 - Outro =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join 2nd Channel: https://www.youtube.com/LiveUnderflow =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → LiveStreams: https://twitch.tvLiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

qPsxbFdCO8k | 28 Nov 2022
Let's talk about how we can implement a reach hack in minecraft. After knowing how it works, it seems so obvious. But it took me over 14h to figure out myself :D Minecraft Protocol: https://wiki.vg/Protocol#Set_Player_Position Community Showcase: EnderKill98 Watch the full playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjwvBI-hmbZ2rpkAl4lutnJG Episode 18: 00:00 - Intro TPAura / InfAura 00:51 - Basic Reach Hack 01:59 - Other Player's PoV 02:42 - Extended Reach Attack 04:03 - Basic Implementation Walkthrough 05:04 - Why Stupid Names for Hacks?! 05:21 - Teleport Challenge: The Vault 07:23 - EnderKill98 -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

Gi2PPBCEHuM | 20 Nov 2022
I tried to hide a new base far away, but players quickly found it. Let me tell you how they did it. Shoutout to TP-Overflow: P1x3lPro (found cat exploit), Overlord2036, Enderkill98, 7H3, MonkeySaint, 19MisterX98, CrimsonGale Community Showcase: DarkMetalMouse Watch the full playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjwvBI-hmbZ2rpkAl4lutnJG Episode 17: -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

VXmvM2QtuMU | 10 Nov 2022
With this video I explain my ~17y/o self what a "Server" is. We look at server software and servers in datacenters to understand how the word is used. Chapters: 00:00 - Intro to "What is a Server?" 00:47 - Wikipedia Server Definition 01:42 - Game Servers 02:50 - Client and Server Communication 04:30 - Web Servers 05:10 - A Server is just a Program 06:38 - A Server is just a Computer 08:30 - Server Hardware 10:10 - What is Server Software? 11:54 - Servers are Everywhere 14:00 - Related Terms and Thought Experiment 17:04 - Outro =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

V4_5x4QtHVg | 31 Oct 2022
I was bullied and kicked out. So I traveled very very far away to establish a new base. In the process I moved the world from 1.18.2 to 1.19.2, forcing everybody to upgrade their hacks and find the new IP. But can you also find my new base? Episode 9 Seedcracking: https://www.youtube.com/watch?v=gSxcDYCK_lY&list=PLhixgUqwRTjwvBI-hmbZ2rpkAl4lutnJG&index=11 Watch the full playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjwvBI-hmbZ2rpkAl4lutnJG Showcase: LeBogo, Philipp_DE, Nocturne, AliFurkan and Cheesburger - https://github.com/homelyseven250/rusty-pinger/blob/main/src/main.rs Episode 14: ... -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

MS7WRuzNYDc | 21 Oct 2022
How bad is it to leak your IP address? VPN providers want us to believe it is dangerous, but I wanted to share my thoughts on the matter. Minecraft:HACKED https://www.youtube.com/playlist?list=PLhixgUqwRTjwvBI-hmbZ2rpkAl4lutnJG OALabs about VPNs: https://www.youtube.com/watch?v=hR5YOV__gGk -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

RDkWagIW6gw | 12 Oct 2022
Telling the story how code review lead to the discovery of a common mistake plugin developers make. It also affects worldguard. However is it really worth fixing? Maizuma Games: https://www.youtube.com/c/MaizumaGames/videos WorldGuard: https://github.com/EngineHub/WorldGuard HackForums: https://hackforums.net/showthread.php?tid=5495770 Episode 15: 00:00 - Intro 01:03 - State of Griefing on the Server 04:00 - Research Motivation 05:26 - Building Club Mate Bottle Challenge 06:08 - Challenge Bypasses 08:24 - WorldGuard Region Entry Protection 09:24 - Code Review of Movement Packets 10:49 - Building the Club Mate Fountain Ruin 11:38 - WorldGuard Bypass Showcase 12:11 - Minecraft 1.9 AntiCheat Bypass 12:55 - Should this be fixed? 14:30 - Community Showcase: DarkReaper Credits/Comments from DarkReaper: Hack based on: https://github.com/BleachDev/BleachHack Special thanks to wagyourtail for optimizing EventlessFly: https://github.com/wagyourtail https://github.com/GreenScripter/sign-restorer Episode 16 Teaser: https://www.youtube.com/watch?v=RlKGdMwwRJg -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

mKAWpFdVcPY | 03 Oct 2022
Why is it called "XSS"? Where does it come from and who influenced this type of website vulnerability? Full Playlist "The History of XSS": https://www.youtube.com/playlist?list=PLhixgUqwRTjyakFK7puB3fHVfXMinqMSi Hotmail "Attackments": https://web.archive.org/web/19981205221020/http://because-we-can.com/attackments/default.htm Which freemail services are safe: https://web.archive.org/web/19981207041804/http://because-we-can.com:80/all/compare.htm Article about XSS: https://web.archive.org/web/19990117001239/http://www.news.com/News/Item/0,4,25792,00.html ; https://web.archive.org/web/19990117001239/http://www.news.com/News/Item/0,4,25792,00.html Microsoft Press Release: https://web.archive.org/web/19990117001239/http://www.news.com/News/Item/0,4,25792,00.html Microsoft XSS FAQ: https://web.archive.org/web/19990117001239/http://www.news.com/News/Item/0,4,25792,00.html CA-2000-02: https://web.archive.org/web/19990117001239/http://www.news.com/News/Item/0,4,25792,00.html Chapters: 00:00 - Intro and Recap 01:35 - XSS's 10th Birthday 02:51 - Talking to David Ross 03:47 - Cross-frame Security Issues 04:43 - Hotmail ATTACKMENTS 06:40 - Breeding Ground for XSS 08:05 - Microsoft in 1999 09:48 - "Cross-Site Scripting" Name Origin 11:56 - CERT Advisory CA-2000-2 13:30 - Do you remember XSS? =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

gVblb-QhZa4 | 23 Sep 2022
In August 1996, Internet Explorer joined the JavaScript security scene after they added JScript. During this era from around 1996-2000, tons of bugs were found what we would call today "Universal Cross-site Scripting". I find this word confusing, but looking back at the history, we can try to make sense of it. Jabadoo Security Hole in Explorer 4.0: https://seclists.org/bugtraq/1997/Oct/85 Aleph One on Jabadoo: https://seclists.org/bugtraq/1997/Oct/87 Georgi Guninski "IE can read local files": https://seclists.org/bugtraq/1998/Sep/47 Georgi's Resume (HIRE HIM!): https://j.ludost.net/resumegg.pdf "Cross-frame security policy": https://seclists.org/bugtraq/2000/Jan/93 Episode 01 - First JS Bug: https://www.youtube.com/watch?v=bSJm8-zJTzQ Episode 02 - Three JS Security Researcher: https://www.youtube.com/watch?v=VtcA58555lY Episode 03: 00:00 - Intro to the "Age of Universal XSS" 01:16 - JavaScript Security in Netscape 1996 01:52 - JScript Vulnerability in Internet Explorer 03:38 - Georgi Guninski: IE can read local files (1998) 05:12 - Who is Georgi Guninski? 06:36 - Georgi Guninski: IE 5 circumventing cross-frame security policy 09:41 - David Ross from Microsoft about Georgi 10:16 - "Cross-Frame" Browser Bugs 11:17 - Universal Cross-Site Scripting 12:15 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

WEMOCFe4EFE | 13 Sep 2022
Hackers keep finding my server and ruin everything. Maybe it's time to end it. Watch full series: https://www.youtube.com/playlist?list=PLhixgUqwRTjwvBI-hmbZ2rpkAl4lutnJG Chunkbase Seed Map: https://www.chunkbase.com/apps/seed-map#LiveOverflow61374546 Enjoys Building Spawn House Time-lapse: https://www.youtube.com/watch?v=dfPeM2siWOY The random dev setup video I used: https://www.youtube.com/watch?v=YOBt2SABHlM Cubiomes: https://github.com/Cubitect/cubiomes Episode 14: 00:00 - Intro 00:46 - Let's Play: The Item Sorter 02:23 - Let's Play: Exploring Spawn Area 04:05 - Thoughts on the Server Community 04:54 - Let's Play: Plans for the End 05:53 - How I got the LiveOverflow server Seed 06:56 - Tutorial: Defeat The Final Minecraft Level 08:02 - Anti-human Plugin Development 10:09 - How Server Plugins Work 12:41 - Teaser: Jungle Secrets =[ ❤️ Support ]= → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join =[ 🐕 Social ]= → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

VtcA58555lY | 04 Sep 2022
In this video we talk about the first JavaScript vulnerabilities in 1997, and how the field was dominated by three "XSS" legends. Bugtraq 1997 - LoVerso: https://seclists.org/bugtraq/1997/Jun/88 LoVerso Website: https://web.archive.org/web/19970607122219/http://www.osf.org/~loverso/javascript/ LoVerso dir.html PoC: https://web.archive.org/web/19970607185809/http://www.osf.org/~loverso/javascript/dir.html Tasty Bits from the Technology Front: https://web.archive.org/web/19970803213858/http://www.tbtf.com/archive/02-27-96.html TBTF about Netscae 2.0b3: https://web.archive.org/web/19970803220511/http://www.tbtf.com/archive/12-02-95.html Scott Weston on TBTF: https://web.archive.org/web/19970803220702/http://www.tbtf.com/resource/b2-privacy-bug.html Bugtraq about Bug Bounty 1995: https://seclists.org/bugtraq/1995/Oct/12 Episode 01: https://www.youtube.com/watch?v=bSJm8-zJTzQ Episode 02: 00:00 - Intro 00:45 - First JavaScript Vulnerability 02:00 - John Robert LoVerso 03:19 - First Directory Browse Vulnerability 04:16 - Comparison to My Exploit 05:13 - John Tennyson 05:44 - Tasty Bits from the Technology 06:16 - Netscape's Bug Bounty 06:48 - Scott Weston history stealing 08:12 - The Three Legends of JavaScript Security 08:59 - The Year 1996 09:31 - JavaScript can't claim to be secure 10:25 - ECMAScript: JavaScript Specification 11:13 - Next Episode Teaser -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

3_e4t3l8fgY | 25 Aug 2022
We investigate how Herobrine got OP on my server and we look back at the network protocol vulnerability I reported in march. vktec: https://www.youtube.com/c/vktec/videos Minecraft Protocol Vulnerability: https://www.youtube.com/watch?v=i-2UgCDdhpM Minecraft:HACKED Playlist: https://www.youtube.com/watch?v=Ekcseve-mOg&list=PLhixgUqwRTjwvBI-hmbZ2rpkAl4lutnJG Episode 13: 00:00 - Let's Play: State of Server 03:56 - Let's Play: Massive Roller Coaster! 06:06 - Brainstorming Force-OP Methods 07:39 - Discovering XSS Payload 09:50 - Debugging Root Cause in JavaScript 11:59 - Scanning for XSS Issues 13:39 - Let's Play: Spawn Griefing Mystery 14:23 - Another Minecraft Protocol 0day! 18:05 - AES/CFB8 Self-Synchronizing 20:26 - Security Research Conclusion -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

x_R1DeZxGc0 | 11 Aug 2022
In this video we explore the basic ideas behind CPU vulnerabilities and have a closer look at RIDL. This video is sponsored by Intel and their Project Circuit Breaker: https://www.projectcircuitbreaker.com/ How to Benchmark Code Execution Times: https://www.intel.com/content/dam/www/public/us/en/documents/white-papers/ia-32-ia-64-benchmark-code-execution-paper.pdf Anders Fogh: https://cyber.wtf/2017/07/28/negative-result-reading-kernel-memory-from-user-mode/ Speculose: https://arxiv.org/abs/1801.04084 RIDL Paper: https://mdsattacks.com/files/ridl.pdf Foreshadow PoC: https://github.com/gregvish/l1tf-poc/blob/master/doit.c Sebastian Österlund: https://osterlund.xyz/ Chapters: 00:00 - Intro & Motivation 00:57 - Concept #1: CPU Caches 01:57 - Measure Cache Access Time with rdtscp 05:00 - Concept #2: Out-of-order Execution 06:11 - CPU Pipelining 07:13 - Out-of-order Execution Example 09:19 - CPU Caching + Out-of-order Execution = Attack Idea!! 10:33 - Negative Result: Reading Kernel Memory From User Mode 13:45 - Pandoras Box 14:23 - Interview with Sebastian Österlund 17:24 - Accidental RIDL Discovery 19:31 - NULL Pointer Bug 21:50 - Investigating Root Cause 23:28 - Conclusion 24:24 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

e0X8xPl4YDk | 07 Aug 2022
Maybe you are wondering how people can figure out crazy stuff in Minecraft. Generally there are two techniques: dynamic testing or reading code. So which method is better? 2No2Name (original finder) Zombie AI: https://www.youtube.com/watch?v=0HvXMFwaYss docm77: https://www.youtube.com/watch?v=BoVMWNeVLf4&t=2148s Episode 10: 00:00 - Let's Play: Building Timelapse 01:16 - Code Review vs. Dynamic Testing 02:29 - Example #1: Creeper Farm Code Review 04:10 - Example #2: Fall Damage Dynamic Testing 05:45 - docm77 Zombie Prank on Hermitcraft 06:55 - How to Find The Zombie AI Bug 10:03 - Does it Affect Other Mobs? 11:16 - Other Players on the Server 12:00 - Let's Play: Bee Farm Timelapse -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

gPsYkV7-yJk | 31 Jul 2022
There exist some awesome tools nowadays to accelerate your self-education for reverse engineering. godbolt and dogbolt are amazing to quickly learn basic assembly and reversing. Compiler Explorer: https://godbolt.org/ Decompiler Explorer: https://dogbolt.org/ C code example: https://github.com/LiveOverflow/liveoverflow_youtube/blob/master/0x05_simple_crackme_intro_assembler/license_1.c Introducing Decompiler Explorer - https://binary.ninja/2022/07/13/introducing-decompiler-explorer.html 00:00 - Intro 00:23 - Motivation 01:00 - How to c? 02:11 - godbolt Basic Usage 03:40 - Function Call on x64 04:30 - Intel vs ARM assembly 05:22 - godbolt Compiler Options 05:50 - Enable gdb -O3 Compiler Optimization 06:35 - Decompiler Explorer dogbolt 07:16 - Comparing Decompiled main() 08:25 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

bSJm8-zJTzQ | 23 Jul 2022
In 1995 Netscape invented JavaScript (LiveScript) and it marked the start of client-side web security issues. In this video we explore this history and learn about the same origin policy (SOP). Cookies Explained: https://web.archive.org/web/19970605224124/http://help.netscape.com/kb/client/970226-2.html Netscape 2.0b1 LiveScript: https://web.archive.org/web/20021212124306/http://wp.netscape.com:80/eng/mozilla/2.0/relnotes/windows-2.0b1.html Netscape 2.0b2 JavaScript: https://web.archive.org/web/20041211182909/http://wp.netscape.com/eng/mozilla/2.0/relnotes/windows-2.0b2.html JavaScript Documentation: https://web.archive.org/web/19970613234917/http://home.netscape.com/eng/mozilla/2.0/handbook/javascript/index.html Netscape 2.02 Security Fixes: https://web.archive.org/web/20030711134218/http://wp.netscape.com/eng/mozilla/2.02/relnotes/windows-2.02Gold.html#Security2 Netscape 3: https://web.archive.org/web/20020808153106/http://wp.netscape.com:80/eng/mozilla/3.0/handbook/javascript/advtopic.htm#1009533 Bugtraq Java Applet RCE: https://seclists.org/bugtraq/1996/Jun/27 Donate to Web Archive: https://archive.org/donate/ Chapters: 00:00 - Intro and Motivation 00:43 - How the Internet Works 01:43 - Online Services in 1994/95 03:08 - JavaScript Released in 1995 04:40 - HTML frames and framesets 05:16 - Cross-Domain Attack Example 06:54 - Fixing the Attack 08:00 - The First Web Exploit? 08:37 - The Same Origin Policy (SOP) 09:35 - Historical Context: Crashes, Java Applets, ... 11:06 - Outro and Shoutout -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

gSxcDYCK_lY | 13 Jul 2022
Some players found my server and imprisoned me... SeedcrackerX: https://github.com/19MisterX98/SeedcrackerX Texture Rotation: https://github.com/19MisterX98/TextureRotations Mathew Bolan Seedcracking: https://www.youtube.com/watch?v=8CKh4x4iK38&list=PLke4P_1UHlmB8sB1oGdcea4SeBH0yZy5B Episode 09: 00:00 - Intro 00:27 - Reviewing Server Logs 01:53 - Leaking Server IP 03:16 - Other Server Scanning Projects 03:54 - Getting Imprisoned! 05:17 - Escaping the Maze 07:40 - PIN Code Door 08:29 - Jumping Puzzle 09:37 - Failing Final Quiz 10:41 - The Well of Death 12:07 - Seedcracking with SeedcrackerX 13:27 - Attacking Blurry Seed 15:56 - Manual Seedcracking with 19MisterX98 16:37 - Step 1: Copy an Area From Video 18:30 - What is a "Random Seed" 16:37 - Step 2: Finding Coordinates Through Texture Rotation 24:58 - Step 3: Cracking Seed Through Tree Leaves 26:13 - How a Minecraft Tree Generates 26:33 - World Seed, Population Seed, Chunk Seed, ... 32:15 - Text Seed vs. Number Seed -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

Q5kIdpPIVuY | 03 Jul 2022
A deeper look into the german hacking laws to see what kind of actions are illegal. There are some surprising edge cases and lots of room for debates. Obviously this video is not legal advice. I forgot about StGB 263a "Computer Fraud" in this video. It's also interesting to speculate about interpretations, however it focuses on financial losses and your intention to enrich yourself. So as security researchers it's less applicable, because we don't look for financial gains. Useful links: Translated German Criminal Law: https://www.gesetze-im-internet.de/englisch_stgb/ Der Hahn erklärt Cyber-Strafrecht: https://www.youtube.com/watch?v=EDqOCxdJSPE 00:00 - Intro and Motivation 01:15 - German Criminal Law 02:57 - StGB 202b - Phishing/MITM 03:55 - StGB 202c - Collecting Credentials 04:33 - StGB 202a - Hacking 04:59 - Example #1: Basic IDOR 06:20 - Example #2: Path Traversal 07:01 - OPTAIN ACCESS to Data 08:25 - Example #3: Minecraft log4shell Scanning 09:30 - Example #4: Technical Limitations? 10:44 - "Vulnerability" or "Exploit" not part of the Law 11:38 - Hacking Attempt is NOT Punishable 12:41 - StGB 202c - Hacking Tools 13:50 - Interpretation by German Federal Court 15:49 - StGB 303a - Data Manipulation 16:50 - StGB 303b = Computer Sabotage 17:13 - Example #5: Hacking a Bank! 18:41 - Hacking with Permissions? 19:50 - Conclusion -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

QradKmQ27JY | 24 Jun 2022
Let's explore how Minecraft can be customized. The knowledge we gain from that is very useful to identify interesting attack surface. Timber Forge: https://www.youtube.com/channel/UC606Jh3yjNj40dcVuMwtUCw McMakistein: https://www.youtube.com/user/McMakistein Information leak in Minecraft 1.8: https://blog.punkeel.com/2018/09/12/minecraft-18-info-leak/ Fuzzing Java: https://www.youtube.com/watch?v=kvREvOvSWt4 Chapters: 00:00 - Intro 00:44 - Herobrine's Bunker 03:06 - Researching Creepers 05:16 - SUPER FAST BUILD MODE 06:43 - How Custom Models Work 11:33 - Attack Surface Overview 12:44 - Resource Pack Security Research 20:46 - Open Server Experiment -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

QhNmb42nF-I | 12 Jun 2022
Laws are complicated and internet wide scanning is a bit of a grey area. So I wonder, what is ethical? Did I cross a line? What do you think? Log4shell explained: https://www.youtube.com/watch?v=w2F67LbEtnk Log4j in Minecraft by John Hammond: https://www.youtube.com/watch?v=7qoPDq41xhQ limited ldap server by leonjza: https://github.com/leonjza/log4jpwn/blob/master/pwn.py Docker Minecraft Server: https://github.com/itzg/docker-minecraft-server Episode 07: 00:00 - Intro 01:37 - Let's Play: 05:24 - Building Spider XP Farm 06:05 - Ethical Internet Scanning? 12:20 - Minecraft Hosting Business 19:35 - Log4shell Scan Results 25:45 - Conclusion -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

GvO2Xtx8p9w | 03 Jun 2022
Google announced the Google Cloud Platform (GCP) Prize 2021 - 133.337$ for the best bug bounty report for the Google Cloud Platform. Reading writeups is important to stay up to date and learn about different attacks. In this video I go over the 6 winners and share my thoughts. This video is sponsored by Google. The announcement: https://security.googleblog.com/2022/06/announcing-winners-of-2021-gcp-vrp-prize.html Winning submissions: #1 https://www.seblu.de/2021/12/iap-bypass.html ($133,337) #2 https://github.com/irsl/gcp-dhcp-takeover-code-exec ($73,331) #3 https://mbrancato.github.io/2021/12/28/rce-dataflow.html ($73,331) #4 https://irsl.medium.com/the-speckle-umbrella-story-part-2-fcc0193614ea ($31,337) #5 https://lf.lc/vrp/203177829 ($1001) #6 https://docs.google.com/document/d/1-TTCS6fS6kvFUkoJmX4Udr-czQ79lSUVXiWsiAED_bs ($1000) GCP Prize 2020: https://www.youtube.com/watch?v=g-JgA1hvJzA GCP Prize 2019: https://www.youtube.com/watch?v=J2icGMocQds Google Paid Me to Talk About a Security Issue! https://www.youtube.com/watch?v=E-P9USG6kLs Fuzzing Java to Find Log4j Vulnerability - CVE-2021-45046 https://www.youtube.com/watch?v=kvREvOvSWt4 ---- 00:00 - Intro GCP Prize 2021 01:05 - 6. "Command Injection in Google Cloud Shell" by Ademar Nowasky Junior 03:36 - 5. "Remote code execution in Managed Anthos Service Mesh control plane" by Anthony Weems 08:31 - 4. "The Speckle Umbrella story — part 2" by Imre Rad 11:33 - 3. "Remote Code Execution in Google Cloud Dataflow" by Mike Brancato 15:47 - 2. "Google Compute Engine VM takeover via DHCP flood" by Imre Rad 20:12 - 1. "Bypassing Identity-Aware Proxy" by Sebastian Lutz 22:42 - Summary and Conclusion 23:58 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

VIy_YbfAKqo | 19 May 2022
I want to show you another Minecraft related project of mine. I tried to scan the whole internet for servers. For what? Well.... you will see. Did 2b2t Griefers Just Do The Impossible? https://www.youtube.com/watch?v=fvbVnT-RW-U Griefing Jeb's Private Server w/ Babbaj, orsond, Zetrax, and _Aaron_ https://www.youtube.com/watch?v=vrjf33A2Vkc Maybe jeb_ server grief was fake? https://www.youtube.com/watch?v=lk70_G32jvg Hermitcraft 9 Episode 4: The Base Is DONE! https://www.youtube.com/watch?v=6coT21RT7HQ masscan: https://github.com/robertdavidgraham/masscan Mongo Express: https://github.com/mongo-express/mongo-express dramatiq: https://dramatiq.io/guide.html Episode 06: 00:00 - Let's Play: Building 04:21 - Some Thoughts on Griefing 09:42 - Griefing vs. Reporting Vulnerabilities 11:05 - Building a Minecraft Server Scanner 17:48 - Exploring the Data 19:44 - Griefing Random Servers 24:36 - Let's Play: Iron and Sugarcane Farm 26:18 - Outro Copyright Music: C418 - Minecraft Soundtrack -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

i-2UgCDdhpM | 08 May 2022
In this video I show off my new XRay mod, we go mining, almost die in the Nether and discover a vulnerability in the Minecraft Protocol. Just another normal Minecraft:HACKED episode! Checkout ilmango: https://www.youtube.com/c/ilmango SciCraft: https://twitter.com/scicraft_ XRay Mod Inspriation: https://github.com/ate47/Xray Minecraft Protocol: https://wiki.vg/Protocol_Encryption AES CFB: https://en.wikipedia.org/wiki/Block_cipher_mode_of_operation#Cipher_feedback_(CFB) The Bug Report MC-249235: https://bugs.mojang.com/browse/MC-249235 Episode 05: 00:00 - Intro: ilmango/SciCraft shoutout 01:16 - XRay Mod 02:12 - Let's Play: Mining & Enchantments 05:16 - Mojang to Microsoft Account Migration 11:15 - Let's Play: The Nether 13:42 - Auditing Minecraft Encryption Protocol 16:14 - Attacker Observes Traffic 16:51 - Attacker Controls Malicious Server 21:07 - Auditing AES/CFB8 Encryption 24:00 - Proof of Concept Attack 26:00 - Reporting to Mojang 27:19 - Let's Play: Herobrine Copyright Music: C418 - Minecraft Soundtrack -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

jJuDP7Rz2hE | 01 May 2022
In this episode we start by exploring the basic AFK fishing farm. While building a potato farm we learn about the scientific method and how we can apply it to Minecraft to find a new fishing farm design for 1.19. Unfortunately we are still on 1.18.2, so we have to develop our own autofish mod. From the newly found programming experience we then are able to develop our own fly hack and bypass the server flying detection! Simple AFK Treasure Fish Farm Concept for 1.19 Sculk Sensor: https://www.youtube.com/watch?v=L-g9ml6wzgM Easy Carrot & Potato Crop Farm Tutorial | Simply Minecraft (Java Edition 1.17/1.18) https://www.youtube.com/watch?v=A8DQYpk5944 MrTroot/autofish https://github.com/MrTroot/autofish Trolling 2b2t Players with a "Magic Carpet" https://www.youtube.com/watch?v=Ze9a-I-kFt4 Episode 04: 00:00 - Intro 01:23 - AFK Fishing Farm Explained 05:30 - Let's Play: Villager Breeder & Potato Farm 07:00 - The Scientific Method 10:27 - Inventing a 1.19 AFK Fish Farm 12:25 - Developing AutoFish Mod 18:14 - Bypassing Server Flying Detection 23:32 - Flying without Elytra! 24:52 - Outro Music: C418 - Minecraft Soundtrack -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

Hmmr1oLt-V8 | 20 Apr 2022
In this episode of Minecraft Hacked we are going to look into client mods and talk about cheating in general. Fabric Example Mod: https://github.com/FabricMC/fabric-example-mod Mixin Examples: https://fabricmc.net/wiki/tutorial:mixin_examples Mixin Wiki: https://github.com/SpongePowered/Mixin/wiki Shulker Dupe mod by 0x3C50: https://github.com/Coderx-Gamer/shulker-dupe FredOverflow: https://www.youtube.com/watch?v=WPDV3LgUL2E Episode 03: 00:00 - Let's Play: Enderpearl Glitch 02:10 - Let's Play: Caving 04:07 - What is Cheating? 14:00 - How to Code Client Mods 14:00 - Hacks: Java Bytecode Modification 21:15 - Let's Play: Return to Surface Music: C418 - Sweden -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

E9kz6RQu9Oc | 16 Apr 2022
I attended Nullcon berlin 2022 in Berlin. Finally met a lot of people I haven't seen in a long time, and also met lots of new people. Nullcon: https://nullcon.net/berlin-2022 Card game: https://thecodeck.com/ Magic Word Writeup: https://ctftime.org/writeup/33233 advertisement: This video is labeled as an ad, but this video was not sponsored by nullcon. I just do it to make sure German regulators cannot complain. -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

OXdFckukh2I | 10 Apr 2022
In this episode we learn how Minecraft servers are implemented by looking at PaperMC and tracing the dependencies. Turns out the custom Minecraft servers rely on decompiling the server source code! It's insane what this Minecraft community has created. Paper Server: https://github.com/PaperMC/Paper Minecraft EULA: https://www.minecraft.net/en-us/eula Fabric Intermediary Mappings: https://github.com/FabricMC/intermediary Fabric Yarn Mappings: https://github.com/FabricMC/yarn/tree/1.18.2-pre3/mappings/net/minecraft Grab the files: https://github.com/LiveOverflow/minecraft-hacked Minecraft:HACKED Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjwvBI-hmbZ2rpkAl4lutnJG Episode 02: 00:00 - Let's Play: Map Exploration 02:47 - How Does Minecraft Help With Hacking? 06:06 - Introduction to Minecraft Servers 09:13 - Minecraft Reverse Engineering 17:03 - Let's Play: The Return to Base Music: C418 - Minecraft Soundtrack -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

BW9ybETXAM8 | 03 Apr 2022
Having a bit of fun on the official Minecraft server from Emmanuel Macron (French President). Disclaimer: This is not an ad, I'm not French, I have no stake in this election, I just love Minecraft. The Minecraft:HACKED Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjwvBI-hmbZ2rpkAl4lutnJG Grab the files: https://github.com/LiveOverflow/minecraft-hacked -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

Ekcseve-mOg | 01 Apr 2022
I got addicted to Minecraft, so I decided to hack it. I know this is a weird video for this channel, but it was really fun to combine Minecraft storytelling with technical tutorials. The result is a very unique hacking tutorial that hopefully can reach lots of new people. I hope you enjoy it! Game Hacking Pwn Adventure Series: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG Devlog Hacking Game: https://www.youtube.com/playlist?list=PLhixgUqwRTjwrqAY_YDWllMw4e5E89E3x Quarry: https://github.com/barneygale/quarry The Minecraft:HACKED Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjwvBI-hmbZ2rpkAl4lutnJG Grab the files: https://github.com/LiveOverflow/minecraft-hacked Episode 01: 00:00 - Let's Play: The Spawn 02:24 - About This Project 06:33 - Let's Play: First Adventure 08:20 - Motivation to Research the Protocol 10:21 - Setup Local Server 13:17 - Network Protocol Analysis Copyright Music: C418 - Sweden -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

BFMmSJ3PRZM | 24 Mar 2022
Celebrating my 10 years of hacking and my 7 years on YouTube! In 2012 I came across my first hacking CTF. Stripe organized a Capture the Flag competition with 6 levels to learn about different vulnerabilities. This is what it all started for me. Cyber Security Challenge Germany: https://cscg.live NFITS donations: https://nfits.de/spenden/ Stripe CTF Announcement https://stripe.com/blog/capture-the-flag CTF Wrap Up https://web.archive.org/web/20120531152105/https://stripe.com/blog/capture-the-flag-wrap-up Files/Sources: https://github.com/stripe-ctf/stripe-ctf io.smashthestack: https://io.netgarage.org/ ey! Look for patterns https://www.youtube.com/watch?v=Jpaq0QkepgA Sudo Exploit Walkthrough https://www.youtube.com/watch?v=TLa2VqcGGEQ&list=PLhixgUqwRTjy0gMuT4C3bmjeZjuNQyqdx GitLab 11.4.7 Remote Code Execution - Real World CTF 2018 https://www.youtube.com/watch?v=LrLJuyAdoAg -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

064yDG7Rz80 | 16 Mar 2022
In this video we talk about various HTTP headers that can improve or weaken the security of a site. And we discuss how serious they are in the context of Google's bug bounty program. Find the full playlist with videos for Google here: https://www.youtube.com/playlist?list=PLY-vqlMAnJ9bGoI82H1BB8BE4A8H2OCA- Chapters: 00:00 - Background Info 03:11 - Intro 03:53 - HTTP Security Header Overview 04:38 - Example #1: X-Frame-Options 06:43 - Example #2: Content-Security-Policy (CSP) 08:16 - Example #3: Strict-Transport-Security (HSTS) 10:44 - Example #4: Cross-Origin Resource Sharing (CORS) 13:12 - Example #5: Cookie Security Flags (HttpOnly) 14:25 - Summary 15:23 - Outro *advertisement because the video was originally produced for Google: https://bughunters.google.com/learn/videos/5956774821363712/bug-hunter-university-videos -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

yrCXamnX9No | 07 Mar 2022
In this video we perform a code audit of Api6 and discover a default configuration that can be escalated to remote code execution. CVE-2022-24112: https://seclists.org/oss-sec/2022/q1/133 GitLab: https://liveoverflow.com/gitlab-11-4-7-remote-code-execution-real-world-ctf-2018/ Challenge files: https://github.com/chaitin/Real-World-CTF-4th-Challenge-Attachments/tree/master/API6 Chapters: 00:00 - Intro 01:09 - Initial Application Overview 02:15 - Discussing Approaches 03:56 - Reading Documentation 04:57 - Initial Attack Idea 06:15 - Identifying Attack Surface 08:46 - Discovering Batch Requests 09:18 - Bypassing X-Real-IP Header 10:15 - Testing the Exploit 11:11 - Reporting the Issue 12:16 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

qA8KB6KndrE | 24 Feb 2022
This was a hard web CTF challenge involving a JSP file upload with very restricted character sets. We had to use the Expression Language (EL) to construct useful primitives and upload an ascii-only .jar file. Alternative writeups: https://github.com/voidfyoo/rwctf-4th-desperate-cat/tree/main/writeup Fuzzing log4j with Jazzer: https://www.youtube.com/watch?v=kvREvOvSWt4 -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

ZDVxFk_T9vU | 12 Feb 2022
This is the end. We finally develop a working sudoedit exploit for Ubuntu 20.04. Grab the files: https://github.com/LiveOverflow/pwnedit Grab the iso: https://old-releases.ubuntu.com/releases/20.04/ Full Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjy0gMuT4C3bmjeZjuNQyqdx Second Channel: https://www.youtube.com/c/LiveUnderflow Twitch: https://www.twitch.tv/liveoverflow Episode 17: 00:00 - Intro 00:42 - Ubuntu VM Setup 02:09 - Fuzzing sudoedit 02:51 - Revisiting an Old Issue 04:11 - Exploring _tsearch Crashes 06:49 - Creating PoC Exploit 08:22 - Minimize and Testing Exploit 09:06 - Fuzzing Statistics 10:48 - Conclusion 11:52 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

kvREvOvSWt4 | 01 Feb 2022
After the log4shell (CVE-2021-44228) vulnerability was patched with version 2.15, another CVE was filed. Apparently log4j was still vulnerable in some cases to a denial of service. However it turned out that on some systems, the issue can still lead to a remote code execution. In this video we use the Java fuzzer Jazzer to find a bypass. Jazzer Java Fuzzer: https://github.com/CodeIntelligenceTesting/jazzer Anthony Weems: https://twitter.com/amlweems 00:00 - Intro 00:54 - Chapter #1: The New CVE 03:38 - Chapter #2: Disable Lookups 05:43 - Chapter #3: Vulnerable log4j Configs 07:52 - Chapter #4: The Remote Code Execution 10:53 - Chapter #5: Parser Differential 12:57 - Chapter #6: Differential Fuzzing 16:07 - Chapter #7: macOS Only 18:15 - Chapter #8: Increase Impact 19:03 - Summary 19:58 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

IEyK1VayvM4 | 18 Jan 2022
Our exploit doesn't work as the user. So now we need to investigate and figure out how we can make it work. We explore three options and implement additional code, but nothing seems to work. Grab the files: https://github.com/LiveOverflow/pwnedit Episode 16: 00:00 - Intro 00:23 - How To Debug The Failing Exploit? 00:49 - Core Dumps 01:49 - Wait in Execution Wrapper to Attach gdb 02:28 - Difference Running sudoedit as root vs. user? 03:00 - Option 1: Bruteforce Offsets Perfectly 03:38 - Option 2: Fengshui as user 04:18 - Option 3: Analyze Our Failing Crash 04:48 - Comparing Option 1 vs. 2 05:45 - Implementing Option 1 07:56 - Implementing Option 2 09:16 - Running Option 2 10:03 - It Doesn't Work in Docker 11:11 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

UsteKcPiGbA | 11 Jan 2022
WE CREATED OUR FIRST EXPLOIT! In this video we were able to control the loading of a malicious library. This can be used to execute our own code as root! But it only works when executing it as root; Executing it as a regular user doesn't work... Grab the files: https://github.com/LiveOverflow/pwnedit dlopen man page: https://man7.org/linux/man-pages/man3/dlopen.3.html Complete playlist: https://studio.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/playlists Episode 15: 00:00 - Intro 00:27 - Recap of Library Loading Exploit Idea 01:45 - Debug a Different Crash 02:28 - Can We Reach dlopen? 03:37 - Using Patterns to find Offsets 05:05 - Writing NULL bytes 05:54 - Create Execution Wrapper sudoenv 07:52 - Debugging the Debug Script 09:00 - Controlling The ni Struct 10:18 - Single Step Exploit Code 11:33 - Create Attack Shared Library 12:17 - First Successful Exploit? 12:58 - Doesn't Work for User 13:16 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

0ti-YgB2iR4 | 03 Jan 2022
To understand a crash in nss_load_function() better, we have to look at the libc source code. While doing this we find a very interesting exploit strategy using dlopen. Grab the files: https://github.com/LiveOverflow/pwnedit Read libc Code: https://elixir.bootlin.com/glibc/glibc-2.31/source Episode 14: 00:00 - Intro 00:22 - Select Testcases For Crash Analysis 01:19 - Debug Crash in gdb 02:02 - Code Examples from grep.app 02:53 - Reading libc Source Code 04:43 - Learning about nss 05:29 - Reaching nss_lookup 06:00 - The service_user Struct ni 07:55 - nss_lookup_function 08:57 - The Crash Reason 09:58 - Exploit Brainstorming 10:57 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

iI9Dz3zN4d8 | 24 Dec 2021
In this video we dig a layer deeper into Log4j. We get a quick overview how Log4j is parsing lookup strings and find the functions used in WAF bypasses. Then we bridge the gap to format string vulnerabilities and figure out why the noLookups mitigation has flaws. Part 1 - Hackers vs. Developers // CVE-2021-44228 Log4Shell: https://www.youtube.com/watch?v=w2F67LbEtnk My lamest GitHub repo ever: https://github.com/LiveOverflow/log4shell -- 00:00 - Intro 00:38 - Chapter #1: Log4j Lookups in Depth Debugging 03:50 - Log Layout Formatters 06:56 - Chapter #2: Secure Software Design 09:21 - Chapter #3: Format String Vulnerabilities 13:58 - Chapter #4: noLookups Mitigation 15:15 - Final Worlds 15:42 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

w2F67LbEtnk | 17 Dec 2021
Let's try to make sense of the Log4j vulnerability. First we look at the Log4j features and JNDI, and then we explore the history of the recent log4shell vulnerability. This is part 1 of a two part series into log4j. Log4j Issues: 2013: https://issues.apache.org/jira/browse/LOG4J2-313 2014: https://issues.apache.org/jira/browse/LOG4J2-905 2017: https://issues.apache.org/jira/browse/LOG4J2-2109 Log4j 2 Security: https://logging.apache.org/log4j/2.x/security.html German Government Warning: https://www.bsi.bund.de/SharedDocs/Cybersicherheitswarnungen/DE/2021/2021-549032-10F2.pdf?__blob=publicationFile&v=3 Cloudflare: https://blog.cloudflare.com/exploitation-of-cve-2021-44228-before-public-disclosure-and-evolution-of-waf-evasion-patterns/ A JOURNEY FROM JNDI/LDAP MANIPULATION TO REMOTE CODE EXECUTION DREAM LAND: https://www.blackhat.com/docs/us-16/materials/us-16-Munoz-A-Journey-From-JNDI-LDAP-Manipulation-To-RCE.pdf whitepaper: https://www.blackhat.com/docs/us-16/materials/us-16-Munoz-A-Journey-From-JNDI-LDAP-Manipulation-To-RCE-wp.pdf --- 00:00 - Intro 01:05 - BugBounty Public Service Announcement 02:23 - Chapter #1: Log4j 2 03:38 - Log4j Lookups 04:15 - Chapter #2: JNDI 06:01 - JNDI vs. Log4j 06:35 - Chapter #3: Log4Shell Timeline 07:33 - Developer Experiences Unexpected Lookups 09:51 - The Discovery of Log4Shell in 2021 11:08 - Chapter #4: The 2016 JNDI Security Research 11:56 - Java Serialized Object Features 13:27 - Why Was The Security Research Ignored? 14:44 - Chapter #5: Security Research vs. Software Engineering 16:49 - Final Words and Outlook to Part 2 17:23 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

Y8qljlUjEEM | 14 Dec 2021
We are still looking for an exploit strategy for the sudo heap overflow. In this episode we look at a few crashes and decide to look into one particular case more deeply. Complete Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjy0gMuT4C3bmjeZjuNQyqdx Grab the files: https://github.com/LiveOverflow/pwnedit (sorry, repo is a bit behind the videos) Homework libc source code: https://elixir.bootlin.com/glibc/glibc-2.31/source Episode 13: 00:00 - Intro 00:36 - Recap of Episode 12 01:16 - Interpret Fuzzing Results | fengshui3 03:05 - Reproduction Script poc.py 04:16 - Heap Object Information not Useful 05:10 - Collect More Data on Crashes | fengshui4 05:32 - Looking at Crashes 06:35 - Intersting Crash in nss_lookup_function 07:00 - Homework -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

hmJKUQlcGAc | 02 Dec 2021
Authorization and Authentication can be confusing. In this video we look at their differences, and then focus on valid and invalid authorization bugs. advertisement: this video was commissioned by the Google Vulnerablity Rewards Program for their site https://bughunters.google.com watch all BHU videos here: https://www.youtube.com/playlist?list=PLY-vqlMAnJ9bGoI82H1BB8BE4A8H2OCA- 00:00 - Intro 00:33 - Authentication vs. Authentication 02:04 - Complex Systems with Permissions and Roles 02:42 - Example #1: Permission Complexity 04:16 - "Fixes" for Authorization Bugs 04:48 - Roles vs. Permissions 05:53 - What are Authorization Bugs? 06:52 - Example #2: Confusing Invalid Auth "Bugs" 08:22 - Summary -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

tzUrYsQRHfs | 18 Nov 2021
We aren't getting anywhere... So we write a new tool to analyse the heap objects located after our overflowing buffer. Complete Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjy0gMuT4C3bmjeZjuNQyqdx Grab the files: https://github.com/LiveOverflow/pwnedit (sorry, repo is a bit behind the videos) gef for gdb: https://github.com/hugsy/gef Episode 12: 00:00 - Intro 00:12 - How to Find Controllable Heap Allocations? 00:50 - Tracing free()! 01:21 - Finding Recognizable Strings on the Heap 01:58 - More Environment Variables 03:26 - fengshui2.py Script Changes 04:19 - Wrong Rabbit Hole... 05:20 - Some Other Research Attempts 06:47 - (gdb) gef Extension - Analyse the Heap Objects 09:03 - Heap Tracing Results 09:51 - Developing fengshui3.py 10:52 - First Peak at Script Results -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

8C7ouESJyfM | 04 Nov 2021
Have you ever heard the sentence that every device can be hacked? I have talked to several security researchers who have experience in hacking Browsers, iPhones and more, to figure out if this is true. And if it's true, should you be worried? You should worry more about Phishing: https://www.youtube.com/watch?v=NWtm4X6L_Cs @steventseeley: https://twitter.com/steventseeley @s1guza: https://twitter.com/s1guza @itszn13: https://twitter.com/itszn13 @xerub: https://twitter.com/xerub @gf_256: https://twitter.com/gf_256 / https://www.youtube.com/channel/UCmYAXMxue6UdEPfAPxA0E8w --- 00:00 - Can Every Device Get Hacked? 00:53 - Collaboration 02:24 - Law of Security: The More Complexity, The More Insecure 03:20 - Proof #1: Zerodium 04:55 - Proof #2: Phone Vendor Security Updates 05:33 - Proof #3: Hacking Competitions 06:28 - "Can You Find The Vulnerabilities Alone?" 09:27 - "Weaponized" (or Operationalized) Exploits 10:35 - The Original Question Is Useless 11:18 - Risk Of Your Device Getting Hacked? 12:32 - The Economics Of The Attacker 14:30 - Who Should Be Worried About 0days? 15:11 - Attack On Security Researchers 16:06 - What Can You Do Against Hackers? 18:15 - Trick Against Smartphone Hacking 19:22 - Summary and Conclusion 21:21 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

v784VBx9w8g | 26 Oct 2021
In this video we are exploring a theoretical security product that automagically encrypts user data securely. But it has a fundamental design flaw which can be exploited. Challenge Files: https://github.com/LiveOverflow/ctf-cryptowaf Walkthrough: https://www.youtube.com/watch?v=ZKrABs-N9wA BugBountyReportsExplained: https://www.youtube.com/c/BugBountyReportsExplained 00:00 - Intro 01:33 - Background Story 02:55 - What is CryptoWAF? 04:16 - Implementing Encryption 05:06 - Encryption Challenges 06:59 - Implementing Decryption 07:02 - Design Flaw 08:26 - Exploiting the Design Flaw 09:06 - Leaking Database 10:04 - WAF Bypass 11:04 - Conclusion 12:07 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

CYWoJ6EYo84 | 17 Oct 2021
After we found some function pointers we could use for exploitation, we instructed sudo to find their heap locations. And then we are developing a script to find a heap layout usable for exploitation. Complete Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjy0gMuT4C3bmjeZjuNQyqdx Grab the files: https://github.com/LiveOverflow/pwnedit Episode 11: 00:00 - Intro 00:40 - The Research Plan 02:09 - Collecting Heap Information 02:40 - Testing the "Instrumentation" - First Problem 04:00 - Understanding Heap Information Output 04:34 - Heap Fragemntation Explained 05:10 - Which Inputs to Control? 05:35 - Writing the Fuzzing Heap Layouts Sripts 07:37 - Development Challenges 08:28 - The Script Results! 09:30 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

mDAwSrH4fqU | 06 Oct 2021
I wrote an article about the state of the YouTube Hacker Scene for Phrack. I hope you enjoy this reading. The article can be read here: http://phrack.org/issues/70/15.html#article --=[ Missing parts: 1. Remember the hacking videos without audio using notepad to communicate? That's definitely a part of the history that should have been included in this article. --=[ References: How SUDO on Linux was HACKED! // CVE-2021-3156 https://youtu.be/TLa2VqcGGEQ?list=PLhixgUqwRTjy0gMuT4C3bmjeZjuNQyqdx XSS on Google Search - Sanitizing HTML in The Client? https://www.youtube.com/watch?v=lG7U3fuNw3A Identify Bootloader main() and find Button Press Handler https://youtu.be/yJbnsMKkRUs?list=PLhixgUqwRTjyLgF4x-ZLVFL-CRTCrUo03 [0] Lenas Reversing for Newbies (2006) https://web.archive.org/web/20070524043123/http://www.tuts4you.com/download.php?list.17 [1] thebroken by Kevin Rose https://archive.org/details/thebroken_xvid [2] Hak5 - Episode #1 https://www.youtube.com/watch?v=SUEXCCWMfXg [3] Notacon 2007 Part 1 https://www.youtube.com/watch?v=HXSZ4PRLUDU [4] CSAW CTF challenge 2.exe, 3.exe and 4.exe flag retrieval https://www.youtube.com/watch?v=_Ld1cD9d7tI [5] Beginner Challenge #1... https://www.youtube.com/watch?v=tdqJ8NEcJUM [6] Phrack issue #69 - International scenes [7] https://reddit.com/r/WatchPeopleCode [8] livectf REDEMPTION by geohot 7/27/2014 https://www.youtube.com/watch?v=td1KEUhlSuk [9] Let's Hack Livestream - exploit-exercises.com (2015) https://www.youtube.com/watch?v=HBnPY77JtqY [10] The Heap: dlmalloc unlink() exploit - bin 0x18 https://www.youtube.com/watch?v=HWhzH--89UQ [11] Hacking Livestream #1: ReRe and EZPZP https://www.youtube.com/watch?v=XWozhb1ZOyM [12] Life of an Exploit: Fuzzing PDFCrack with AFL for 0days https://www.youtube.com/watch?v=8VLNPIIgKbQ [13] HackTheBox - Popcorn https://www.youtube.com/watch?v=NMGsnPSm8iw [14] Live CTF v2: ... https://www.youtube.com/watch?v=D7uXE_lEzxI [15] SMT in reverse engineering, for dummies https://youtu.be/b92CW-NZ3l0 [16] GoogleCTF - XSS "Pasteurize" https://youtu.be/voO6wu_58Ew [17] Hacking into Google's Network for $133337 https://youtu.be/g-JgA1hvJzA [18] https://support.google.com/youtube/answer/2801964?hl=en [19] Data breaches, phishing, or malware? Understanding the risks of stolen credentials https://dl.acm.org/doi/abs/10.1145/3133956.3134067 [20] Zero to Hero Pentesting https://youtu.be/qlK174d_uu8?list=PLLKT__MCUeiwBa7d7F_vN1GUwz_2TmVQj [21] How the Apple AirTags were hacked https://youtu.be/_E0PWQvW-14 [22] FuzzOS: Day 1, starting the OS https://youtu.be/2YAgDJTs9So [23] How We Hacked a TP-Link Router and Took Home $55,000 in Pwn2Own https://www.youtube.com/watch?v=zjafMP7EgEA [24] https://www.tiktok.com/@malwaretech --=[ Chapters: 00:00 - Intro 00:21 - 0. About the Author 00:50 - 1. Preamble 02:00 - 2. Before 2014 04:40 - 3. My Start in 2015 08:50 - 4. Today's Scene 15:50 - 5. Final Words 16:39 - Some Thoughts 20:06 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Blog: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

gVGHaiB9qo4 | 26 Sep 2021
This video was created in collaboration with @PwnFunction and was comissioned by Google VRP. Checkout @PwnFunction excellent YouTube channel! Read the article here: https://bughunters.google.com/learn/improving-your-reports/avoiding-mistakes/6082745027264512 -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

UFyTksTXFTA | 19 Sep 2021
We develop a helper script to find function pointers we could maybe overwrite with our heap overflow. This is another episode in the sudo series. Complete playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjy0gMuT4C3bmjeZjuNQyqdx 00:00 - Intro 00:46 - Research Idea 01:29 - Collecting Data 02:20 - Developing Python Script 03:34 - Finding Potential Function Pointers 04:01 - Verify if pointers are usable 05:07 - Function Pointer Candidate #1 05:58 - Function Pointer Candidate #2 06:47 - Evaluate the Research Methodology 08:00 - What's Next? -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

P8LXLoTUJ5g | 12 Sep 2021
In this video you can see me working over 10h on hacking an Ethereum smart contract. The attack was done on a private chain, so no actual Ethereum users have been affected. This was a challenge called `Montagy` from the Real World CTF 2019 competition. Even though this was part of a competition, the methodology and technologies used are the tools used in real-life Ethereum hacking as well. More Ethereum hacking: - Ethereum Smart Contract Hacking #1 - Real World CTF 2018: https://www.youtube.com/watch?v=ozqOlUVKL1s - Jump Oriented Programming: Ethereum Smart Contract #2 - Real World CTF 2018: https://www.youtube.com/watch?v=RfL3FcnVbJg - Ethereum Smart Contract Backdoored Using Malicious Constructor: https://www.youtube.com/watch?v=WP-EnGhIYEc 00:00:00 - Backstory 00:03:58 - Smart Contract Challenge Overview 00:20:17 - Blockchain Transaction Investigation 00:22:13 - Rough Plan & Research Setup 00:34:27 - Looking more into the Contracts 00:41:18 - Debugging with remix 01:08:43 - What we learned so far 01:09:31 - Researching custom hash 01:34:26 - Breaking hash algorithm with z3 02:02:37 - Realizing winning condition is different... 02:03:20 - Developing exploit pwn.js 02:15:10 - Exploit doesn't work... debugging. 02:31:30 - Exploit finally works 02:33:55 - Sending Exploit to the Team in China 02:35:05 - The Flag 02:36:10 - Opinion and Conclusion -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

c2Qi7traPls | 04 Sep 2021
We have a heap buffer overflow, but how can we exploit this now? Let's discuss some of the possible strategies. Grab the files: https://github.com/LiveOverflow/pwnedit We made the thumbnail together on stream: https://www.youtube.com/watch?v=71h-AqXut7A -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

glDod0AjXBs | 28 Aug 2021
I'm officially a thought leader now. My keynote for https://bsides.berlin/ 00:00 - Welcome 02:41 - Online/Offline conference 07:59 - LiveOverflow 10:03 - Security conferences are bad 13:18 - YouTube fanboy 17:22 - #cisotips 20:18 - Poll about pentesting 22:03 - Lack of certificate pinning (SSL) 25:26 - Remote code execution (RCE) 28:22 - Cross-site scripting (XSS) 30:05 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

461Y7-SHga4 | 26 Aug 2021
I looked at some old footage playing Real World CTF in 2019 and found this emotional moment. finally the z3 script worked. #shorts -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

FCjMoPpOPYI | 19 Aug 2021
I made a web hacking challenge for the Cyber Security Challenge Germany (cscg) 2021. Grab the files: https://github.com/LiveOverflow/ctf-screenshotter Cyber Security Challenge Germany: https://www.cscg.de/ 00:00 - Introduction to screenshotter app 00:58 - Setup the challenge 01:38 - First overview of functionality 03:07 - Review application architecture 03:51 - The chrome service 04:19 - The main app service 05:07 - Chrome service IP leak 06:22 - The app secret 06:54 - Methodology: go for complex features 09:22 - The flagger/admin service 11:30 - First attack idea: XSS 11:55 - Reviewing flask templates 13:09 - Useless self-XSS? 13:38 - Bypass demo restriction 15:45 - Using the Chrome SSRF? 17:00 - Leak websites of other users 18:31 - THE EXPLOIT! 22:04 - Outro -=[ ❤️ Support ]=- → Support: https://liveoverflow.com/support → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

RZiGBjrOLY8 | 11 Aug 2021
A bit more code review of sudo to understand why it's vulnerable and what the conditions are to get there. Full Playlist: https://www.youtube.com/watch?v=TLa2VqcGGEQ&list=PLhixgUqwRTjy0gMuT4C3bmjeZjuNQyqdx Grab the files: https://github.com/LiveOverflow/pwnedit Episode 08: 00:00 - Intro 00:18 - The Heap Overflow 02:27 - Identifying the Conditions to Reach the Vulnerable Code 03:00 - The sudo Modes 03:40 - Sudo is Escaping The Arguments! 04:25 - How to Skip the Escaping? 05:16 - The Curious Case of "sudoedit" 06:15 - Exploring Alternative sudo modes 07:05 - Outro 07:35 - #ads -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

KHwVjzWei1c | 31 Jul 2021
... and use alert(document.domain) or alert(window.origin) instead. Blog post: https://liveoverflow.com/do-not-use-alert-1-in-xss/ Bug Hunter University: https://bughunters.google.com/learn/invalid-reports/web-platform/xss/5108550411747328 00:00 - Intro 00:47 - Why Do We Use Alert(1) for XSS? 02:25 - alert(1) Popup is NOT Proof of a Vulnerability! 03:07 - Invalid XSS Example 1 on Blogger 04:43 - Sandbox Subdomains 06:27 - Sandboxed iframes 08:29 - Invalid XSS Example 2 on Google Sites 09:50 - Why Should You Care About Invalid XSS Issues? 10:55 - Summary 11:55 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

zdzcTh9kUrc | 24 Jul 2021
We debug the line that causes the heap overflow. And it's a great opportunity to understand pointers in C. The full playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjy0gMuT4C3bmjeZjuNQyqdx Grab the files: https://github.com/LiveOverflow/pwnedit The original disclosure: https://blog.qualys.com/vulnerabilities-research/2021/01/26/cve-2021-3156-heap-based-buffer-overflow-in-sudo-baron-samedit Episode 07: 00:00 - Intro & Motivation 00:46 - Create Debug Build 01:02 - The Crashing Location 01:43 - Scary Pointer Magic 02:10 - *to++ = *from 02:56 - Explaining: from++ 04:03 - Explaining: *from 04:56 - Explaining: to++ 05:23 - Explaining: *to = *from 05:54 - The Copy While Loop 06:26 - Explaining: from[0] vs *from 07:14 - The Bug! 08:35 - Wrong Allocation Size Calculated 09:30 - Unescape Logic 10:15 - Why though? -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

NWtm4X6L_Cs | 17 Jul 2021
This is a phishing security awareness video where I am showing you how to identify a trustworthy site. Spoiler alert: the browser address bar is the only trustworthy security indicator Phishing Quiz: https://phishingquiz.withgoogle.com/ -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

StQ_6juJlZY | 10 Jul 2021
It's surprisingly easy to do security research on Firefox trying to find sandbox escapes. You should give it a try! The Original Article: https://blog.mozilla.org/attack-and-defense/2021/04/27/examining-javascript-inter-process-communication-in-firefox/ Fuzzing IPC: https://blog.mozilla.org/attack-and-defense/2021/01/27/effectively-fuzzing-the-ipc-layer-in-firefox/ Mozilla Bug Bounty: https://www.mozilla.org/en-US/security/client-bug-bounty/ 00:00 - Intro 01:44 - What is a Process Sandbox? 03:04 - How to Implement a Sandbox? 03:43 - Introducing Inter Process Communication (IPC) 05:17 - Why Browsers Need a Complex Sandbox Architecture 07:19 - Browser Exploitation requires Sandbox Escape 08:42 - Strategy 1: OS Sandbox Implementation Bypass 08:59 - Strategy 2: Attacking the IPC Implementation Layer 09:48 - Strategy 3: IPC Logic Bugs 10:10 - HTML/JS Components in Firefox 11:21 - IPC Messages Implemented in JavaScript 11:58 - Setting Up Firefox Nightly For Debugging 13:20 - alert() IPC Message Handler 14:04 - IPC Message Sender 15:21 - Send Malicious IPC Messages 16:12 - CVE-2019-11708 Prompt:Open Sandbox Escape 17:13 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

_W3D_0erZ00 | 02 Jul 2021
Now that we found a crash and got a minimal testcase last episode, we can now try to find the true location of the overflow. ASan is an invaluable tool for that. Fuzzing Project: https://fuzzing-project.org/tutorial2.html Grab the files: https://github.com/LiveOverflow/pwnedit Full Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjy0gMuT4C3bmjeZjuNQyqdx Episode 6: 00:00 - Intro 00:47 - Create sudo ASan build 01:47 - Investigating weird issue 04:14 - Accidentally solving the problem 05:10 - Improve AddressSanitizer Debug Output 06:49 - Interpreting AddressSanitizer Output 07:23 - Triaging More Unique Crashes 08:25 - Plan For Next Steps -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

YeEGDfPqR0E | 25 Jun 2021
One fuzzer found a crash. Now we need to investigate if it's a 0day or if we found the known bug. To do that we first minimize the testcase, and then perform various tests and sanity checks. Grab the files: https://github.com/LiveOverflow/pwnedit/tree/main/episode05 The whole playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjy0gMuT4C3bmjeZjuNQyqdx Article version: https://liveoverflow.com/minimizing-afl-testcases-sudo5/ gef for gdb: https://github.com/hugsy/gef 00:00 - Recap of Fuzzing Experiment: afl vs afl++ 00:44 - We found a crash! 01:45 - First Look at the Crash Testcase 02:57 - Looking at Crash in GDB 04:06 - Is it a 0day or the Known Bug? 05:28 - Minimizing AFL Testcase 07:16 - Looking at Minimized Testcase 08:23 - Next Steps -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

lKzsNp4AveY | 18 Jun 2021
What is the difference between a security vulnerability and a security risk? What is a Vulnerability: https://www.youtube.com/watch?v=866olNIzbrk Securing Linux Servers: https://www.youtube.com/watch?v=fKuqYQdqRIs Top 25 Open Redirects: https://corneacristian.medium.com/top-25-open-redirect-bug-bounty-reports-5ffe11788794 Get 100$ Credit for Linode* [affiliate]: https://liveoverflow.com/linode1 00:00 - Intro 01:42 - Example 1: SSH Password Authentication 02:58 - Absolutist Security Opinion 03:41 - When a Risk Becomes a Vulnerability 05:32 - Risk vs. Vulnerability 06:15 - Example 2: Open Redirects 08:16 - Open Redirects Relation to Vulnerabilities 10:02 - A Open Redirect Is Not a Vulnerability 10:43 - Conclusion -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ All links with "*" are affiliate links.

Do1Ri8TCF0Q | 11 Jun 2021
AFL helped us to find a buffer overflow. Did we find a real crash in sudo? Let's investigate it. Linode 100$ free Credit [*affiliate]: https://liveoverflow.com/linode3 Files on GitHub: https://github.com/LiveOverflow/pwnedit/tree/main/episode04 Blog Post: https://liveoverflow.com/finding-buffer-overflow-with-fuzzing/ Previous video and episode playlist: https://www.youtube.com/watch?v=W2kZnmchJhI&list=PLhixgUqwRTjy0gMuT4C3bmjeZjuNQyqdx&index=3&t=335s Episode 4: 00:00 - Intro 00:28 - Looking at AFL crashes 01:25 - Investigate Crashes with gdb 03:35 - Debug Crash in AFL argv[] wrapper 04:27 - Fixing Buffer Overflow in AFL argv[] wrapper 05:19 - Setup Fuzzing Experiment with AFL++ 07:11 - AFL UI Output Information -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links.

ErgIWeP6dXQ | 04 Jun 2021
Is hacking a meritocracy? Who is not good enough? Successful people are the most skilled? Am I just jealous? The Hacker Mind Podcast EP 22: Hacking Social Media https://podcasts.google.com/feed/aHR0cHM6Ly9mZWVkLnBvZGJlYW4uY29tL3RoZWhhY2tlcm1pbmQvZmVlZC54bWw/episode/dGhlaGFja2VybWluZC5wb2RiZWFuLmNvbS9lNmE1NWNmZS05ODY5LTM3YzYtYTU1YS1lZTY4ZmMxODgxOWQ 00:00 - Meritocracy Intro 01:16 - Chapter I: My Feelings & My Background 03:05 - Increase my own Merit 05:08 - Judging Others 06:13 - Chapter II: The Job Market 07:04 - Skills are not that important 08:44 - Minimum requirement of skill 09:28 - Cognitive Dissonance 11:02 - Chapter III: Social Media 13:14 - Conclusion -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/liveoverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

W2kZnmchJhI | 22 May 2021
We are using afl to fuzz the sudo binary, but we run into a lot more issues. In this video we are troubleshooting some issues and come up with solutions. Article version: https://liveoverflow.com/troubleshooting-afl-fuzzing-problems/ Linode 100$ free credit* [affiliate]: http://liveoverflow.com/linode3 Correction: afl can fuzz setuid process, I was just dumb. More details in this video: https://youtu.be/TLa2VqcGGEQ?t=323 Part 3: 00:00 - Intro 00:30 - afl: No more free CPU cores 01:10 - Patching execs in target binary 01:47 - afl: Unable to create file. No space left on device 03:06 - afl Trick: Find non-memory corruption issues 04:22 - Fuzzing setuid sudo as root 06:38 - Next fuzz attempt -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links.

sXThugPk_zA | 15 May 2021
What is the difference between Pentesting and Pentesting? There are different jobs that can be described as "pentesting" and I want to talk a bit about it. This should also help you to better organize your own learning, as you better understand your goal. Blog: https://liveoverflow.com/pentesting-vs-pentesting-vs-bug-bounty/ 00:00 - Intro 00:32 - Pentesting: What most people think 01:19 - Pentesting: What I actually do 01:53 - Pentesting vs. "Pentesting" 03:49 - Better name: Application Security 04:14 - CTFs are Useless/Awesome! 05:21 - Opposite Side of Pentesting and AppSec 06:27 - I prefer being a Developer than Pentester 06:51 - Bug Bounty vs Pentesting 08:36 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

COHUWuLTbdk | 08 May 2021
Let's investigate some issues we have fuzzing sudo with afl. And also explain how AFL works. After improving our fuzzing setup even more, we are finally read to start fuzzing sudo for real. Can we find the vulnerability now? https://liveoverflow.com/support Grab the files: https://github.com/LiveOverflow/pwnedit/ milek7's blog: https://milek7.pl/howlongsudofuzz/ Sudo Research Episode 02: 00:00 - Recap 00:39 - Fixing AFL Crash Using LLVM mode 03:32 - Testing the AFL Instrumented Sudo Binary 04:11 - How Fuzzing with AFL works! 06:44 - Can AFL find the crash? 08:06 - Detour: busybox and argv[0] 09:48 - How could we discover "sudoedit"? 10:47 - Can AFL find "sudoedit" through magic? 11:25 - Include argv[0] in the testcases 13:06 - Parallel Fuzzing Setup -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

uj1FTiczJSE | 29 Apr 2021
Recently a serious vulnerability in sudo was announced. But how can people even find these kind of bugs? Let's talk about why we would want to look for vulnerabilities in sudo, and how we could do that. We then try to setup afl, but fail... well... this will take a while https://liveoverflow.com/support Play around with Linux and get 100$ Credit for Linode*: https://liveoverflow.com/linode3 Text Version: https://liveoverflow.com/why-pick-sudo-research-target-part-1/ GitHub: https://github.com/LiveOverflow/pwnedit/tree/main/episode01 Full Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjy0gMuT4C3bmjeZjuNQyqdx 00:00 - Intro 01:48 - Prepare the System 03:57 - How to Pick a Research Target? 05:57 - Choose the Strategy: Fuzzing 09:27 - Fuzzing argv[] With AFL 13:00 - Running Into the Next AFL Problem 14:51 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links.

TLa2VqcGGEQ | 22 Apr 2021
The most comprehensive video covering the sudo vulnerability CVE-2021-3156 Baron Samedit. I spent two weeks on rediscovering, analysing and exploitation of the sudoedit heap overflow. We will talk about fuzzing, code review, exploit strategies, heap feng shui and developing the exploit. https://liveoverflow.com/support Article: https://liveoverflow.com/critical-sudo-vulnerability-walkthrough-cve-2021-3156/ Binary Exploitation Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjxglIswKp9mpkfPNfHkzyeN PwnFunction's Binary Exploitation Playlist: https://www.youtube.com/playlist?list=PLI_rLWXMqpSkAYfar0HRA7lykydwmRY_2 Full CVE-2021-3156 Advisory: https://packetstormsecurity.com/files/161160/Sudo-Heap-Based-Buffer-Overflow.html Qualys Blog: https://blog.qualys.com/vulnerabilities-research/2021/01/26/cve-2021-3156-heap-based-buffer-overflow-in-sudo-baron-samedit milek7's blog on fuzzing sudo: https://milek7.pl/howlongsudofuzz/ 00:00 - Intro and Motivation 01:33 - afl: Fuzzing argv[] 03:22 - afl: sudo vs. sudoedit 04:27 - afl: Fuzzing setuid Process 06:49 - Fuzzing Conclusion 07:11 - Code Review: Identify Risky Code Through Isolation 09:39 - Code Review: Bypass Safe Conditions 11:15 - Exploit Strategy: Modern Mitigations 12:25 - The service_user Object Overwrite Technique 13:48 - Heap Feng Shui via Environment Variables 14:57 - Bruteforce Script to Find Exploitable Conditions 15:39 - Find and Analyse Useful Crashes 16:31 - Exploitability Analysis Conclusion 17:13 - Qualys Researchers Knew nss From Stack Clash 17:47 - Sudoedit Exploitable on macOs? 18:32 - Research Conclusion 19:27 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

fKuqYQdqRIs | 15 Apr 2021
Do you have a linux server and do you know how to prevent getting hacked? In this video we will critically discuss a few best practices. The video can be summarized as: "a lot of fluff, not much use". Play around with Linux and get 100$ Credit for Linode*: https://liveoverflow.com/linode1 Prefer to read? Blog article version: https://liveoverflow.com/protect-linux-server-from-hackers/ Very scientific analysis: https://docs.google.com/spreadsheets/d/1cKaO7qH3EZbrEJR7F5Df0ObvJOhw3RdOMCERuroWrBc Other Opinions: - Enable unattended updates: https://blog.filippo.io/psa-enable-automatic-updates-please/ Chapters: 00:00 - Intro and Motivation 01:47 - 1. Disable SSH Password Login 03:47 - Detour: Password Login for Websites (https) 04:39 - Password Recommendations 05:33 - 2. Disable Direct root SSH Login 07:07 - Creating user and add to sudo 08:47 - 3. Change Default SSH Port 10:42 - 4. Disable IPv6 for SSH 13:40 - 5. Setup a Basic Firewall 15:43 - 6. Unattended Server Auto Upgrade 19:04 - Conclusion -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links.

LMFY3NvNITY | 07 Apr 2021
I made every video I ever wanted to make... At least that's how I feel. I feel like "Everything I know I have shared in my over 300 videos". I recently celebrated 6 years on YouTube, and it made me think about the state of the channel and the struggle of finding new video ideas. Website: https://liveoverflow.com/ All Playlists: https://www.youtube.com/c/LiveOverflowCTF/playlists?view=1&sort=dd&shelf_id=0 Chapters: 00:00 - 300+ Videos and 6 Years on YouTube 02:35 - Binary Exploitation and Memory Corruption 03:22 - Hardware Security Research 03:42 - Game Hacking with Pwn Adventure 3 04:13 - Unity Game Development & Hacking 04:32 - Browser Exploitation 04:58 - Web Hacking Introduction 05:33 - AngularJS Research 05:45 - Advanced Web Hacking 06:33 - Capture The Flag Walkthroughs 08:08 - Embedded Hardware CTF - rhme2 08:43 - sudoedit Vulnerability Research Walkthrough 09:02 - Mobile Security 09:28 - My Career 09:41 - Standalone Videos Not Part Of Playlists 10:16 - I Covered "Everything"... 11:42 - I'm Proud Of My Videos! 12:26 - Website LiveOverflow.com 13:47 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

EEZ2T5UodVY | 05 Apr 2021
We are in the 2nd month of the Cyber Security Challenge Germany 2021. Checkout the new challenges, including `screenshotter` which I made: https://cscg.de Screenshotter Challenge: https://earth.cscg.live/tasks/screenshotter German 14-21 y/o: https://junior.cscg.live/ German 22-26 y/o: https://senior.cscg.live/ International Players: https://earth.cscg.live/ Discord: https://discord.gg/s9By2UBt Donate to non-profit: https://nfits.de/spenden/ ECSC: https://europeancybersecuritychallenge.eu/ -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

GSraDuD4ziQ | 01 Apr 2021
I don't even know what this video is about. 🛑 Put these chan̴̜̱̾̈̋̚̕nels on yo̸̺̐ur b̷̗͋͂loc̶͓̆kl̴̢̯̈i̵̢̼̽̽ŝ̶̢͌͜ṯ̸̔ͅ!̶̠̞͝ 🛑 Codingo: https://www.youtube.com/channel/UCUfO02gdMDXgOJWdv_jiLMg PinkDraconian: https://youtube.com/c/PinkDraconian JohnHammond: https://www.youtube.com/user/RootOfTheNull CryptoCat: https://www.youtube.com/c/CryptoCat23 Hacksplained: https://youtube.com/hacksplained Farah: https://www.youtube.com/channel/UCq9IyPMXiwD8yBFHkxmN8zg DC CyberSec: https://www.youtube.com/dccybersec ZetaTwo: https://youtube.com/ZetaTwo XSSRat: https://www.youtube.com/channel/UCjBhClJ59W4hfUly51i11hg 247CTF/Neut: https://www.youtube.com/channel/UCtGLeKomT06x3xZ2SZp2l9Q Insiderphd: https://www.youtube.com/user/RapidBug Lupin: https://www.youtube.com/channel/UCh3ecxx3c6qZDlccBjjiDyQ Rana Khalil: https://www.youtube.com/c/RanaKhalil101 Superhero1:https://youtube.com/superhero1 Tib3rius: https://www.youtube.com/channel/UCs6dtu4e0JL-N4hVszsFpBw Meg: https://www.youtube.com/channel/UCQiE6iIQr9bNSFaYcFgFYGw PwnFunction: https://www.youtube.com/channel/UCW6MNdOsqv2E9AjQkv9we7A stacksmashing: https://www.youtube.com/channel/UC3S8vxwRfqLBdIhgRlDRVzw More channels to block (except LiveOverflow): https://securitycreators.video/

g-JgA1hvJzA | 17 Mar 2021
In this video we hear the story how Ezequiel Pereira found a critical vulnerability in Google Cloud and was awarded $164,674 in total. This is a crazy bug, because it requires so much knowledge about Google internals. We will learn about Google's Global Software Load Balancer, BNS addresses and other Google secret tricks! This video was sponsored by the Google Vulnerability Rewards Program: https://security.googleblog.com/2021/03/announcing-winners-of-2020-gcp-vrp-prize.html Ezequiel's own Writeup: https://www.ezequiel.tech/2020/05/rce-in-cloud-dm.html SRE Book: https://sre.google/books/ GCP Prize 2020: https://www.youtube.com/watch?v=J2icGMocQds 00:00 - Intro 00:33 - Meet Ezequiel Pereira 00:58 - The Impact Of The Bug 02:41 - Winning The $133,337 Prize! 04:03 - How To Find a Product To Research? 06:05 - How To Approach Google Products? 07:16 - The BEST Tip For Bug Hunters! 08:08 - What Does Deployment Manager Do? 09:00 - Type Providers: First Research Into Deployment Manager 11:03 - Using Type Providers for SSRF? 13:00 - Going Deeper - Finding A Hidden Version 15:01 - The Google Dogfood Version 15:52 - Discovering Internal Google Options - GSLB 17:34 - The Google SRE Book - Explaining Googles Software Load Balancer 19:34 - Exploiting GSLB? 21:58 - Failing to Exploit GSLB 22:28 - Abusing Protobuf To Find Hidden Enums 25:34 - Google API GRPC/Protobuf Tricks 29:11 - SUCCESS! Attacking Google's Network via GSLB SSRF! 30:34 - Summary -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

VJRcFMU_xZY | 03 Mar 2021
The CSCG 2021 is starting now! https://cscg.de German 14-21 y/o: https://junior.cscg.live/ German 22-26 y/o: https://senior.cscg.live/ International Players: https://earth.cscg.live/ Discord: https://discord.gg/s9By2UBt Donate to non-profit: https://nfits.de/spenden/ ECSC: https://europeancybersecuritychallenge.eu/ Last year's CSCG 2020 announcement: https://www.youtube.com/watch?v=kLZdnvvQRKY A few years ago I participated twice in the Cyber Security Challenge Germany, and I think it was an awesome experience connecting with other young people interested in IT security. So I’m super excited to announce that the Cyber Security Challenge Germany 2021 just started! It’s a three month long hacking CTF competition, and the best players can qualify for the national team to compete at the European Cybersecurity challenge. So it is aimed primarily at german students between the age of 14 to 26. But of course anybody can play it. So if you are interested in hacking and IT Security, go check it out at cscg.de. Btw, this event is organized by our non-profit organisation “Nachwuchsförderung IT-Sicherheit e.V.”, and we are always looking for any for of support and donations. #shorts

F6UerHkVdLA | 25 Feb 2021
Helping somebody with a simple format string exploit via twitter. Getting stuck with problems is one of the most frustrating but best ways to learn. That's why I like to help people figure out their own issues, rather than just telling them. https://exploit.education/protostar/ Binary Exploitation Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjxglIswKp9mpkfPNfHkzyeN Voice Actor John Hammond: https://www.youtube.com/channel/UCVeW9qkBjo3zosnqUbG7CFw 00:00 Intro 00:59 Question via Twitter DM 02:16 My Initial Thoughts and Analysis 03:20 Format String Recap 04:30 Analyzing The Broken Script 05:39 "Where is the flag?" What is the challenge goal? 06:20 Question 1: What does %s do? 07:16 Question 2: What is the difference between %x and %s? 08:07 GO WATCH MY OLD VIDEOS! 08:28 Question 3: Does %s print strings from the stack? 09:09 Binary Exploitation Episode 0x1E & Google Solutions 10:45 Question 4 Going Back to Basics! 12:05 Question 5: How to print actual stack values? 13:05 Miscommunication via Text Messages 13:45 Wrong Challenge Assumptions 14:33 Miscommunication Again 15:35 Testing %x 15:56 Recognizing ASCII in hexdump 17:10 Typical Format String Exploit Issues 17:59 Running Into More Weird Bugs 20:23 Debugging The Script 21:45 Almost Solved It! 22:45 Found the Flag! 23:20 Ooops! They Had Solved It Earlier 23:34 Conclusion: Helping People Takes Time 24:15 Is This a Good Video? 24:39 Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

1hpqiWKFGQs | 14 Feb 2021
When I looked at another SerenityOS exploit, I learned something new! The hack is very creative and directly interacts with hardware. I never really understood how modern CPUs interact with peripherals, so this was very interesting to me. Previous SerenityOS videos: https://www.youtube.com/watch?v=qUh507Na9nk https://www.youtube.com/watch?v=oIAP1_NrSbY Linus' wisdom2 exploit: https://github.com/allesctf/writeups/blob/master/2020/hxpctf/wisdom2/writeup.md SerenityOS hacking: https://www.youtube.com/watch?v=DhVZ7vO69DI&list=PLMOpZvQB55bcRA5-KjvW7dVyGUarcqZuL Vulnerable SerenityOS version: https://github.com/SerenityOS/serenity/tree/5505159a94c226d0c8a5e82a163a6d37a9404c57 Binary Exploitation Playlist: https://www.youtube.com/watch?v=iyAyN3GFM7A&list=PLhixgUqwRTjxglIswKp9mpkfPNfHkzyeN Hardware Wallet Research: https://www.youtube.com/watch?v=nNBktKw9Is4&list=PLhixgUqwRTjyLgF4x-ZLVFL-CRTCrUo03 00:00 - Intro 00:47 - Accumulating Knowledge Over Years 01:14 - The Plan For This Video 02:00 - Computers are Simple! 02:40 - Computers are Hard! 03:39 - What I Already Know About Kernels 04:58 - Missing Link Between Hardware and Software 06:00 - Andreas Summarizes Another SerenityOS Exploit 08:18 - What Are CPU EFLAGS? 11:02 - What Are IO Ports? 12:03 - Playing With EFLAGS 13:06 - Talking To Hardware via IO Ports 13:45 - Arduino Hardware Example - OUT Instruction 14:45 - Access Harddisk Controller With Ports 15:15 - Detecting Keybord Key Press 15:43 - EUREKA! 16:46 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

wv2YhT89LDU | 05 Feb 2021
When I saw how easy it is for Andreas to find bugs in his own code, and even write exploits for it, I thought about the relationship between hacking and coding skills. And it's not surprising that decades of programming experience can easily transferred to hacking skills! LiveOverflow Playlists: https://www.youtube.com/c/LiveOverflowCTF/playlists Andreas Kling: https://www.youtube.com/channel/UC3ts8coMP645hZw9JSD3pqQ 00:00 Introduction 00:26 SerenityOS Videos & Andreas Kling 01:12 Andreas Kling Skills & Career 02:09 Exploitation Requires Coding! 02:36 What about Web Hacking? 03:42 System Exploitation vs. Web Hacking 05:14 Coding Useless for Web Hacking?! 05:43 Programming in Different IT Security Jobs? 06:49 IT Security as Entry-level Position? 07:07 What's your Programming Experience? -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

oIAP1_NrSbY | 22 Jan 2021
Last video we looked at a kernel exploit against SerenityOS Kernel. This video we dig deep into the sources to find out why the vulnerability exists. After that we even attempt to find our own exploit. Part 1 - The Kernel Exploit: https://www.youtube.com/watch?v=qUh507Na9nk 00:00 - Intro 00:27 - Part 1 - Linux vs. Serenity 01:17 - Finding ptrace() in Linux 01:31 - Finding ptrace() in Serenity 02:12 - Comparing Linux and Serenity ptrace() Code 04:07 - Architecture Specific Code in Linux 04:45 - Continue Comparing Linux vs. Serenity ptrace() Code 05:08 - Conclusion of Part 1 05:57 - Part 2 - hxp wisdom2 Exploit Analysis 06:44 - Reading ptrace() again 07:26 - Reading execve() code 08:46 - The Critical execve() code 09:30 - Do You Notice The Vulnerability? 10:17 - Race Condition Exploit Strategy 11:48 - Part 3 - Doing Own Research 13:15 - Doing an Experiment 15:44 - Kernel Changes for Experiment 16:00 - Failed Experiment 16:26 - Asking Andreas Kling About Scheduler Code 17:45 - Conclusion - Read More Code 18:38 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

qUh507Na9nk | 10 Jan 2021
Let's have a look at a recent kernel local privilege escalation exploit! Exploit Source: https://hxp.io/blog/79/hxp-CTF-2020-wisdom2/ Kernel Developer Walkthrough: https://www.youtube.com/watch?v=LORxdO1XUjY Syscalls, Kernel vs. User Mode and Linux Kernel Source Code: https://www.youtube.com/watch?v=fLS99zJDHOc How Do Linux Kernel Drivers Work? https://www.youtube.com/watch?v=juGNPLdjLH4 00:00 - Introduction 00:15 - Exploit PoC 00:39 - main() 00:52 - prepare_shellcode() 02:39 - mmap() shared memory to signal "ready" state 03:07 - fork() into [child] and [parent] 03:44 - [parent] wait for the child 04:00 - [child] unveil() loop 05:03 - [parent] ptrace ATTACH and POKE child 05:58 - [child] execve("passwd") 06:38 - [parent] PEEK entrypoint of child in loop 07:34 - [parent] child entrypoint changes! 07:49 - Exploit Walkthrough 09:20 - Root Shell via Shellcode 10:10 - Vulnerability Summary 10:37 - Which UNIX-like Kernel is this? 12:44 - The importance for Security Research 13:59 - Next Video and Resources 14:22 - Patreon and YT Members -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

Oc8QQxyzjjQ | 24 Dec 2020
How can I get a job as a pentester? Should I go to university or self-study? Do I need certifications? My Life in Shirt Stories: https://www.youtube.com/playlist?list=PLhixgUqwRTjwy6HCzLfwNzdrSrcrLOM4d Bogotter's Life Journey: https://www.youtube.com/playlist?list=PLMgOinWh2Y7GEkkDhFOQB1afVw6TNdCJc -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

xpZe9hm7I1A | 23 Dec 2020
In 2016 I gave my first real conference talks at various conferences. The first one was at at Confidence in Poland. My former colleague Abraham helped me a lot to actually do it. Abraham: https://twitter.com/7aSecurity Smart Sheriff at Confidence: https://www.youtube.com/watch?v=UDowdC2tIaU Confidence Conference: https://confidence-conference.org/ Full Shirt Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjwy6HCzLfwNzdrSrcrLOM4d -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

IWUSxyEiIU0 | 22 Dec 2020
Short video, I don't have much to say. Haxember 2019: https://www.youtube.com/playlist?list=PLhixgUqwRTjzTvVyL_8H-DJBf8VT3uiu2 Another career/journey story I enjoyed: https://www.youtube.com/playlist?list=PLMgOinWh2Y7GEkkDhFOQB1afVw6TNdCJc My Shirt Stories: https://www.youtube.com/playlist?list=PLhixgUqwRTjwy6HCzLfwNzdrSrcrLOM4d -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

vI59BvgtWKk | 21 Dec 2020
In 2016 I was invited to participate in the CitizenLab Summer Institute as part of my work on researching the security of an app called Smart Sheriff. Four part series and report about Smart Sheriff: https://citizenlab.ca/2015/09/digital-risks-south-korea-smart-sheriff/ Full Shirt Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjwy6HCzLfwNzdrSrcrLOM4d -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

As8R9rsXHmA | 20 Dec 2020
This is another berlinsides t-shirt, which I got around the time when I started LiveOverflow! Super Old Unlisted Videos from 2015: https://www.youtube.com/playlist?list=PLhixgUqwRTjxcNmC6mUdGuK9Tmdh_IUed Entire Shirt Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjwy6HCzLfwNzdrSrcrLOM4d -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/
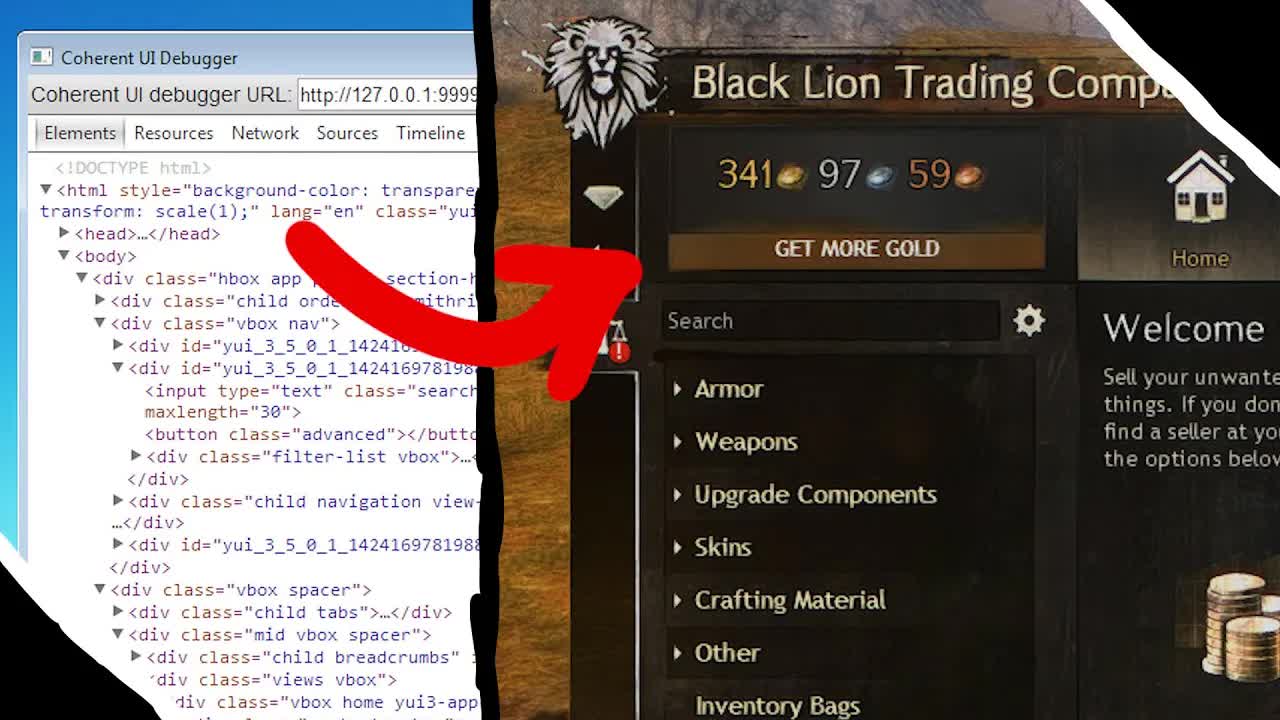
xRrB02gJXMY | 19 Dec 2020
Showing off some videos I have worked on before LiveOverflow existed! And also some of my GW2 research. Working with the Tradingpost API: https://youtu.be/de2g09oI8FQ Guild Wars 2 Gold Inflation Research: https://youtu.be/v9SUOtg7hL0 Guild Wars 2 Mystic Forge Conduit Market Manipulation: https://youtu.be/1svGcx4jjCg Full Playlist of all Shirt Videos: https://www.youtube.com/playlist?list=PLhixgUqwRTjwy6HCzLfwNzdrSrcrLOM4d -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

TNML7ZIgcwU | 18 Dec 2020
At the end of 2014 I started to participate in the Cyber Security Challenge Germany (CSCG). LiveOverflow didn't exist yet. I will also tell the story how the ALLES CTF team came to be. CSCG 2020 Introduction: https://www.youtube.com/watch?v=kLZdnvvQRKY Our non-profit: https://nfits.de/ CSCG: https://www.cscg.de/ -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

FFFtUUYmvr0 | 17 Dec 2020
Going to another demo scene party and winning 2nd place with my photo from an abandoned wood factory. I also share a project I worked on in 2014, but never finished. -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

u6TIbcKMc04 | 16 Dec 2020
After my 6 month break I have moved to Berlin and started my master's degree at the Technical University in Berlin. What Reaction to Packet Loss Reveals about a VPN - Anna Shubina & Sergey Bratus: https://www.youtube.com/watch?v=WJF8oNVZ7ew -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

4tvlaIiW3ok | 15 Dec 2020
Going to the Phenoelit eXchange Event. I don't have much to tell about this one, except that the t-shirt design was very interesting! Let's try to understand the references. PXE LangSec Teach-Shirt: http://www.phenoelit.org/stuff/The_PXE_LangSec_Teach-Shirt.pdf -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

6441Pgi-n-w | 14 Dec 2020
After my bachelor degree I took a break for one semester, before going to university for my master's. I had big plans for researching and learning more about security, but .... it wasn't as productive :P WoodenPotatoes: https://www.youtube.com/user/WoodenPotatoes/playlists -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

LWCppkiTXP8 | 13 Dec 2020
I first talk about the research of my bachelor thesis, and then I talk about my decision to take a break before going to university for a master degree. In that time I also joined Cure53 as a freelancer by accident. -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

DI7Bm9M1bDE | 12 Dec 2020
Following the white rabbit into the hacker conference berlinsides 2013. I'm also reaching the end of my bachelor's degree, and I have to start thinking about what to do afterwards. stacksmashing about ELF: https://www.youtube.com/watch?v=nC1U1LJQL8o Julian Bangert, Sergey Bratus -- ELF Eccentricities: https://www.youtube.com/watch?v=4LU6N6THh2U -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

gcfQK6awEEc | 11 Dec 2020
Attending my first Phenoelit eXchange Event (PXE). A successor of ph-neutral. Stacksmashing on YouTube: https://www.youtube.com/channel/UC3S8vxwRfqLBdIhgRlDRVzw Invitation: http://ph-neutral.org/PXE2.txt PXE2 Announcement: https://twitter.com/41414141/status/307556114726260736 -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

D5gDw2Wj4O8 | 10 Dec 2020
Going to the 29th Chaos Communication Congress in Hamburg. Talking about the impactful talks I saw Facedancer: https://www.youtube.com/watch?v=qZtkANvDxZA Tamagotchi talk: https://www.youtube.com/watch?v=c4PkcZScBV8 -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

8rahIJb4h5g | 09 Dec 2020
A friend from shackspace brought me to a Demoscene Party in Cologne Germany - Evoke 2012! I was blow away and became a fan. Evoke 2012: https://www.evoke.eu/2012/ Noiseplug Video: https://vimeo.com/47380710 dojoe Noiseplug: http://www.pouet.net/prod.php?which=59694 -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

1EofqDJN0SQ | 08 Dec 2020
Going to berlinsides again. I will also tell a few more personal things, gonna be an awkward video... CSS Keylogger Video: https://www.youtube.com/watch?v=oJ6t7AImTdE Scriptless Attacks: https://www.youtube.com/watch?v=m_U_6tgUFx0 Rebecca "bx" Shapiro and Sergey Bratus - Programming Weird Machines with ELF Metadata: https://www.youtube.com/watch?v=V5KsUm1KfZE -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

wffEBz47Xmw | 07 Dec 2020
In early 2012 I stumbled over the Stripe CTF, which introduced me into the world of hacking competitions and wargames. This was my real start into security. exploit-exercises.com is now exploit.education: http://exploit.education/ io smashthestack: https://io.netgarage.org/ W3Challs: https://w3challs.com/ Stripe CTF: https://stripe.com/blog/capture-the-flag -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

JtX9tZ70QU8 | 06 Dec 2020
We are still at the end of 2011. In parallel to the CCC there was another event I attended and it was called berlinsides. -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

zScf2x2hoHQ | 05 Dec 2020
At the end of 2011 I went to my first Chaos Communication Congress. It was really memorable and wasn't what I expected it to be. Packets in Packets: https://www.youtube.com/watch?v=euMHlV6MNqs The Science of Insecurity: https://www.youtube.com/watch?v=3kEfedtQVOY Geeks and Depression Panel: https://www.youtube.com/watch?v=QnfOOoTOrDE -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

_nb8bAbJHCA | 04 Dec 2020
At this point I was in university for about a year. And we totally overengineered a web engineering project by making a trailer, printing t-shirts and getting a domain. Full December Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjwy6HCzLfwNzdrSrcrLOM4d Wargame made in 2013 with the same name: gracker.org -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

FOZBzZab6Fc | 03 Dec 2020
In 2011 I joined the Stuttgart hackerspace "shack". This was my second living room and I learned a lot during that time. The environment was very inspirational and motivating. HACKERSPACES ARE AWESOME: https://www.youtube.com/watch?v=HJy-Y4nok3g Full December Project Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjwy6HCzLfwNzdrSrcrLOM4d -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

tyg5LU0tecE | 02 Dec 2020
In ca. 2009/10 I got my first Android smartphone, an HTC Desire. And I started to learn how to develop apps for it. During the same time I also got into Google Wave and learned to develop widgets. This t-shirt reminds me that even stuff I learned 10 years ago still help me today, and that it is all about accumulating knowledge and experience. Shirt Stories Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjwy6HCzLfwNzdrSrcrLOM4d -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

zAqFhQ0yxTE | 01 Dec 2020
I want to kick off this December/advent series with the oldest t-shirt I own. I started with PenSpinning as a teenager in ~2007 and eventually we ordered t-shirts. It taught me a lot of lessons when it comes to learning and practicing, and it was the first real online-community I found. A day in the life of a pen-tester: https://www.youtube.com/watch?v=2LOtBpA7W_M JaPen 1st: https://www.youtube.com/watch?v=c3ddIoziQ_U -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

thbZwi6WwIE | 26 Nov 2020
We are going to solve the Nintendo HireMe.cpp challenge with some "basic" math. I call it basic, because linear algebra is taught pretty early in school. But I know it is not so easy to figure out that it can be used here. Also the trick with GF2 is math that you would only learn at university. But if you would watch my videos, you would have know it from the software_update video writeup ;) Watch part 1 - Introduction: https://www.youtube.com/watch?v=6sHSDoJ5a1s software_update challenge writeup: https://www.youtube.com/watch?v=EOlddNofKxo HireMe.c: https://www.nerd.nintendo.com/files/HireMe SageMath and Jupyter Notebook: https://www.sagemath.org/ z3: https://github.com/Z3Prover/z3 00:00 - Introduction 00:26 - What Made It Click?! 01:13 - Alternative Mathematical Representation 02:04 - Recognizing Linear Algebra 03:00 - Matrices Math 04:15 - Using SageMath 04:40 - Gallois Field GF(2) 06:06 - Creating and Solving the System of Equations 08:23 - Tackling the XOR Bruteforce Part 09:40 - Start of Walkthrough: Inverting s-box 10:17 - inp_to_out() and Recursive solve_round() 11:10 - Generate Internal Input[] Candidates with z3 12:45 - Kicking off the Solving Algorithm 13:41 - Cliffhanger: SageMath + Jupyter Notebook 14:02 - Finding a Solution!!!!! 14:22 - Conclusion 15:22 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

6sHSDoJ5a1s | 19 Nov 2020
Difficult programming and reverse-engineering challenge by Nintendo European Research & Development (NERD). In this first part I have a first look at the challenge and try different stuff. In the next video we talk about the solution. PS: I'm not looking for a job. Just used a clickbait title based on the challenge name. HireMe.cpp: https://www.nerd.nintendo.com/files/HireMe Working at NERD: https://www.nerd.nintendo.com/jobs 00:00 - Introduction 01:14 - Quick Overview 02:31 - First Lazy Strategy - Chosen Plaintext Attack 05:03 - Looking Closer at the Code 07:29 - Next Lazy Attempt - Just Reverse It 08:56 - Thinking Deeper about the Algorithm 12:06 - Talking is NOT Understanding! 12:30 - Attacking XOR Chain 13:51 - Visual Analysis 16:06 - Giving up... for now... 16:30 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

DGuRI_SPZYg | 07 Nov 2020
Get a unique insight into how hacking really looks like. This is a live recording and commentary of the ALLES! CTF Team playing the Google CTF finals hackceler8. After we have placed 8th in the Google CTF 2020, we were invited to a special finals event, which was speed hacking against 3 other teams. Unfortunately we only got 2nd place in our group, but I'm still proud of what this team has built in a short amount of time. 00:00:00 - Introduction to hackceler8 00:02:30 - Tooling Overview 00:10:37 - Preparations Summary 00:11:16 - Phase 1: Bare/Stripped Map 00:30:17 - Map Overview 00:36:14 - Web/Software Engineering is Useful for Hacking! 00:44:38 - Phase 2: Getting Client and Server Sources 00:53:38 - Finding the Red Key 01:09:10 - Did you expect more hardcore hacking? 01:11:12 - First Proxy Issues 01:16:13 - Solving the Door Control Challenge 01:18:44 - Proxy Works Again! 01:37:50 - Phase 3: The Game is Live! 01:55:06 - Accept Broken Proxy and Start The Game 01:59:20 - pasten wins...... 02:06:40 - First Flag for ALLES! 02:27:50 - Seventh and Last Flag for ALLES! 02:30:09 - Match Completed! Pwny Racing: https://pwny.racing/ BITKs talking about their setup on Nahamsec https://www.twitch.tv/videos/789001869 -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

VVdmmN0su6E | 26 Oct 2020
Let's explore what a file format is, and provide a different view on it. We dive into polyglots, file format research and the impact on security. Funky File Formats Talk: https://www.youtube.com/watch?v=hdCs6bPM4is corkami/mitra tool: https://github.com/corkami/mitra Guessing vs. Not Knowing featuring Steganography: https://www.youtube.com/watch?v=L1RvK1443Yw -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

L1RvK1443Yw | 18 Oct 2020
I really hate it when I have to guess stuff. This applies to CTFs, but also to my real-world work in penetration testing. It is incredibly frustrating to bruteforce or guess something, that could just be read in the source code. I much rather focus on technical details, tricks and techniques. Try the XSS challenge: https://hacking.app/xss/xss_chall1.html#welcome Failed DOM Clobbering Research part 1/2: https://www.youtube.com/watch?v=dZXaQKEE3A8 Chaining Script Gadgets to Full XSS part 2/2: https://www.youtube.com/watch?v=UGtrpXk6QVU -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

UGtrpXk6QVU | 08 Oct 2020
In the second part we are building on top of what we have learned. We figure out how to craft something special out of a very limited script gadget. Eventually we can use it to leak the secret notes ID and notes content. Part 1: https://www.youtube.com/watch?v=dZXaQKEE3A8 Challenge: https://capturetheflag.withgoogle.com/challenges/web-littlethings Pasteurize: https://www.youtube.com/watch?v=Tw7ucd2lKBk 00:00 - Recap Part 1 00:20 - Start of the Attack Chain 00:54 - Control the Theme Callback 02:29 - Prior JSONP Capability Research 04:40 - innerHTML Breakthrough 06:13 - Content Security Policy Fail 07:19 - iframe CSP Bypass 08:31 - The Solution 10:09 - Chaining Three Gadgets 11:34 - Researching Cool XSS Techniques 12:00 - Solving the Challenge 13:25 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

dZXaQKEE3A8 | 28 Sep 2020
All The Little Things was a pretty hard web challenge from the Google CTF 2020. In this video we do some initial recon and research and try to find an angle to attack. Part 1/2. Challenge: https://capturetheflag.withgoogle.com/challenges/web-littlethings Pasteurize: https://www.youtube.com/watch?v=Tw7ucd2lKBk 00:00 - Intro 00:50 - Functionality Overview 01:29 - HTML Injection 02:25 - Making a Plan 02:50 - theme.js Discovering JSONP Endpoint 03:51 - user.js The User Class 04:23 - utils.js Start of Chain 04:44 - No Ideas... 05:07 - DOM Clobbering: window.load_debug 06:05 - Doing Security Research 07:25 - Anything else to clobber? 07:49 - Start from beginning, discover __debug__ 08:10 - The load_debug() function 09:20 - window.name is special 09:41 - Try it yourself! 10:00 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

9ecv6ILXrZo | 18 Sep 2020
Try chatting with tech support about getting a flag. There is a very easy XSS in the support chat, but the problem is, the XSS is on the wrong domain. So we can't easily grab the flag. Challenge: https://capturetheflag.withgoogle.com/challenges/web-typeselfsub Tech Support: https://typeselfsub.web.ctfcompetition.com/ -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- Don't spend money on courses

Tw7ucd2lKBk | 09 Sep 2020
Easy web challenge from the Google CTF. XSS a paste service. John Hammond: https://www.youtube.com/watch?v=voO6wu_58Ew Gynvael part 1: https://www.youtube.com/watch?v=0wUDA0oh8sQ Gynvael part 2: https://www.youtube.com/watch?v=OYP9hvy4MHQ Challenge: https://capturetheflag.withgoogle.com/challenges/web-pasteurize Pasteurize: https://pasteurize.web.ctfcompetition.com/ -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

bknybcgfjAk | 01 Sep 2020
It turns out, I have a favorite number over 1 million! Let me show you why 1094795585 is special to me and to many hackers. Binary Exploitation Course Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjxglIswKp9mpkfPNfHkzyeN exploit.education: https://exploit.education/protostar/ Example Buffer Overflow Challenge: https://www.youtube.com/watch?v=lE6ke7pqCNY #MegaFavNumbers Playlist: https://www.youtube.com/playlist?list=PLar4u0v66vIodqt3KSZPsYyuULD5meoAo 00:00 - #MegaFavNumbers Introduction 00:40 - Why do we like 1,000,000? 01:49 - Why is Hexadecimal so Cool? 04:00 - Relationship Between Binary and Hex 06:06 - ASCII Encoding 07:20 - Phrack Hacker History 09:00 - Example Buffer Overflow 11:08 - The Significance of 0x41414141 -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

3ac9HAsfV8c | 25 Aug 2020
Reverse engineering challenge from the Google CTF Finals 2019. Robin implemented a FPGA simulator in a shader to run it on a GPU. The players had to reverse engineer the software and figure out the algorithm implemented in hardware. Challenge Sources: https://github.com/google/google-ctf/tree/master/2019/finals/reversing-gpurtl Gynvael: https://www.youtube.com/user/GynvaelEN 00:00 - Introduction 01:35 - GPURTL Challenge Motivation 03:13 - Gynvael's Challenge Approach 04:40 - The Mysterious Image 08:55 - Challenge Files 10:45 - Interpreting the Graphic 11:21 - The Lua script source code 14:38 - The FPGA bitstream 16:56 - Shader code 23:50 - The gpurtl Rust binary 26:48 - Verilog Code 27:48 - Possible Solution Paths 32:44 - Verilog Synthesis 35:30 - Development Issues 38:55 - Solution by Team pasten "advertisement" because Google paid for flights and hotel. -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

T1lP1b89_cc | 21 Aug 2020
The last day from my trip to the Google CTF Finals 2019 in London. "advertisement" because Google paid for flight and hotel. Google CTF Finals Challenges: http://gctf-2019.appspot.com/ Challenge Sources (and solutions): https://github.com/google/google-ctf/tree/master/2019/finals -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

w54_tQUYwyc | 16 Aug 2020
Hardware challenge "Having a Blast" from the Google CTF Finals. It can be compared to the "Keep Talking and Nobody Explodes". The Challenge Trailer: https://www.youtube.com/watch?v=_8fBHnH4VNE John Hammond: https://www.youtube.com/channel/UCVeW9qkBjo3zosnqUbG7CFw Challenge Sources: https://github.com/google/google-ctf/tree/master/2019/finals/hardware-having-a-blast 00:00 - Intro 00:38 - Challenge video 03:41 - Challenge hints 05:31 - Before the first attempt 07:40 - First try 08:33 - Recap of the first attempt 14:00 - Interview: RedRocket 15:00 - Interview: LeavCat-PLUS 15:48 - Challenge discussions 17:03 - Second attempt! 21:05 - Did we win? 21:20 - Interview: Challenge Author 29:00 - Flag distribution to winning teams 30:02 - Fails... 31:14 - Eavesdropping on challenge conversation 36:59 - Challenge summary "advertisement" because Google paid for flights and hotel. -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

PBvthC7soS4 | 12 Aug 2020
A vlog about my experience at the Google CTF Finals 2019 in London. It was great to see so many talented hackers competing! Google CTF Finals Challenges: http://gctf-2019.appspot.com/ Challenge Sources (and solutions): https://github.com/google/google-ctf/tree/master/2019/finals -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

4quMk5Z5EN8 | 08 Aug 2020
In December 2019 I was invited by Google to come to London for the Google CTF finals. This Vlog is about my second day where I listened to some bug hunter talks and met students at init.G. Vlog Day 1: https://www.youtube.com/watch?v=QNZfdqTAvYM John Hammond: https://www.youtube.com/channel/UCVeW9qkBjo3zosnqUbG7CFw Gynvael: https://www.youtube.com/user/GynvaelEN The video is labeled with "advertisement" because Google paid for the flight and hotel. -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

aCexqB9qi70 | 31 Jul 2020
A very interesting Cross-site Scripting Issue in gDocs Spreadsheets. I get a chance to talk to the bug hunter Nick, as well as Google engineers to understand both sides. How did he find it? And why did this vulnerability exist in the first place? Nickolay: https://thisisqa.com/ The video is sponsored by Google's VRP: https://www.google.com/about/appsecurity/reward-program/ 00:00 - Introduction 00:53 - Following reproduction steps 02:13 - What is postMessage()? 03:04 - Script Gadget: the hlc() function 03:30 - Script Gadget: ui.type instantiation 04:22 - Vulnerability summary 05:12 - Nick's focus on gviz 06:47 - Script Gadget: chartType injection 08:09 - Script Gadget: drawFromUrl exploit technique 08:57 - chartType injection fix 10:13 - Code refactoring cause of XSS 11:12 - How to find ui.type option? 14:04 - What to do with ui.type Script Gadgets? 15:13 - Why does hlc() exist?! 15:40 - JSONP sandbox 17:16 - Nick's background story -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/

k4MnqaYZIY4 | 21 Jul 2020
This was a fun little project - hunting down an easter egg in the open source code of VLC. I made this video in 2018. @StereoBucket: https://twitter.com/StereoBucket/status/1005842783893155840 -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #EasterEgg #ReverseEngineering

BRfzYNBpIpg | 08 Jul 2020
To make a hackable MMO game, I had to think a lot about the unique game design. So we are going over challenges as well as level design and how the game evolved. 00:00 - Intro 00:37 - 1. Level Design 04:05 - 5. Player Character Design 05:14 - 3. Soft Release 06:00 - 4. Tower (Challenge) 07:10 - 5. Lava (Challenge) 08:32 - 6. Emoji (Challenge) 11:03 - 7. Reverse Engineerling IL2Cpp 13:04 - 8. Player Radar (Challenge) 16:36 - 9. Maze Runner (Challenge) 19:07 - 10. M4z3 Runn3r (Challenge) 20:45 - 11. Open Source 21:56 - 12. Conclusion 22:29 - Outro Part 1 - How To Learn Something New?: https://www.youtube.com/watch?v=LTlBElDPDDM Part 2 - Igniting Creativity: https://www.youtube.com/watch?v=f5LRrPPC09o Part 3 - Unity Multiplayer/MMO Game: https://www.youtube.com/watch?v=0RJQVkavFIA Part 4 - MMO Hacking Game Design: this video Play the game: http://maze.liveoverflow.com -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- ...

0RJQVkavFIA | 30 Jun 2020
My technical thoughts on building a MMO Game. I have no professional experience in this area, and try to come up with an architecture that is simple to implement but also scalable enough for my needs. 00:00 - Intro 01:00 - 1. Using a Networking Provider? 02:19 - 2. Language for Game Server 03:29 - 3. Server Architecture 08:01 - 4. UDP vs. TCP 09:50 - 7. The Network Protocol 10:25 - 8. Position Packet 11:48 - 8. Login Packet 14:11 - 10. UDP Reflection Attack 16:12 - 11. UDP Client in C# 20:59- 12. UDP Server in Python 23:48 - 14. Distributing Player Position 25:58 - 15. HTTP Server Component 26:49 - Conclusion 27:00 - Outro Part 1 - How To Learn Something New?: https://www.youtube.com/watch?v=LTlBElDPDDM Part 2 - Igniting Creativity: https://www.youtube.com/watch?v=f5LRrPPC09o Part 3 - Unity Multiplayer/MMO Game: this video Heatmap Animation: https://youtu.be/bdPgdBFzchs -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

f5LRrPPC09o | 24 Jun 2020
How to be creative and get ideas for making a (hacking) game? In the last video I talked about how I got started with gamdev in in Unity. This video I share the game design aspect and what I do to be creative. The first game I made has two hacking challenges: Fall Damage and Datamining 00:00 - Introduction 00:45 - 1. Making a Plan 02:18 - 2. Being Creative 03:23 - 3. Kickstart Creativity 04:31 - 4. Fall Damage 06:42 - 5. Flags in Offline Games 07:53 - 6. 3D Modeling 08:43 - 7. Alternative Story 10:03 - 9. Technical Issues 11:22 - 10. New Island 13:10 - 11. Making NPCs 15:13 - 12. The 2nd Flag 17:29 - 13. Play Testing 18:00 - 14. Out of Ideas 20:09 - 15. Finalizing "Follow The White Rabbit" 21:48 - Conclusion 22:26 - Outro Download the game for Windows here: https://earth.2020.cscg.de/tasks/Follow%20The%20White%20Rabbit%20-%20Cave Part 1 - How To Learn Something New?: https://www.youtube.com/watch?v=LTlBElDPDDM Part 2 - Igniting Creativity: this video Part 3 - Unity Multiplayer/MMO Game -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

LTlBElDPDDM | 17 Jun 2020
I made a game that is intended to be hacked! But I have never made a game before, so I had to learn game development first. In this devlog I talk about my journey into gamedev with Unity. Hope it helps if you want to learn something new. 00:00 - Introduction 01:18 - 1. The Motivation 03:08 - 2. My IT Background 05:54 - 3. What Game Engine? 07:50 - 4. Learning Resources 11:00 - 5. Game Assets 13:46 - 6. First Step: Getting Started! 17:57 - 7.1 Playing Around: Gaia 19:23 - 7.2 Playing Around: Character Controller 22:26 - 7.3 Playing Around: Cinemachine 23:13 - 7.4 Playing Around: Render Pipelines 24:27 - 8. First Test! 26:17 - Conclusion 26:39 - Outro Follow The White Rabbit: https://earth.2020.cscg.de/tasks/Follow%20The%20White%20Rabbit%20-%20Cave Maze: http://maze.liveoverflow.com/ Game Dev Guide: https://www.youtube.com/channel/UCR35rzd4LLomtQout93gi0w Gamefromscratch: https://www.youtube.com/channel/UCr-5TdGkKszdbboXXsFZJTQ Jason Weimann: https://www.youtube.com/channel/UCX_b3NNQN5bzExm-22-NVVg Brackeys: https://www.youtube.com/user/Brackeys Crest: https://github.com/crest-ocean/crest Synty Studios: https://www.syntystudios.com/ -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://instagram.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

L2C8rVO2lAg | 31 May 2020
Learn Hacking? A one-sided video why CTFs are awesome to learn hacking and various IT security skills. CTFs are TERRIBLE: https://www.youtube.com/watch?v=lxJpKUoX-6E CTF Guidelines: https://docs.google.com/document/d/1QBhColOjT8vVeyQxM1qNE-pczqeNSJiWOEiZQF2SSh8/preview# 00:00 - Introduction 00:22 - Motivation to Learn 00:44 - The Path is More Important Than the Goal 01:39 - Example 1: uploooadit Challenge 02:52 - Value for Beginners and Professionals 03:22 - Example 2: Magic Tunnel Challenge 06:02 - Why Rare/Weird Bugs are important! 07:00 - Example 3: flaglab / GitLab challenge 07:28 - Learning the Principles 08:20 - The Importance of Writeups 09:15 - It's Good to Fail Challenges 09:39 - What is a Great Challenge? 10:44 - The Role of BugBounty Writeups 11:11 - Made Up Challenges are Still Realistic 11:37 - Striving Towards 100% Vuln Coverage 12:30 - Crazy Vulnreabilities In Reality 13:03 - What are CTFs? 13:30 - The Community Aspect 13:58 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://www.instagram.com/liveoverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

lxJpKUoX-6E | 31 May 2020
Learn Hacking? Let's explore the one-sided arguments why CTFs are terrible to learn hacking and doing IT security work. CTFs are AWESOME: https://www.youtube.com/watch?v=L2C8rVO2lAg Discussion on Twitter: https://twitter.com/LiveOverflow/status/1265562734772584449 CTF Guidelines: https://docs.google.com/document/d/1QBhColOjT8vVeyQxM1qNE-pczqeNSJiWOEiZQF2SSh8/preview# 00:00 - Introduction and Example 1: Barcode 00:39 - Example 2: Flag Hidden in an Image 01:19 - Example 3: dah-dah-di-di-dah 01:40 - Guessing and Thinking Like the Author 01:55 - GCHQ CyberChef CTF Tool 02:35 - Example 4: Boot2Root / VM Based Challenges 03:11 - Useful Only For Absolute Beginners 03:33 - Always the Same Challenges 04:07 - Teaching a Wrong Mindset 04:55 - CTFs Provide Wrong Incentives 05:22 - Limited Topics Covered by CTFs 06:12 - Beyond the Technical Aspects - Mental Health 06:47 - Advanced CTF Challenges - Pwnables 08:10 - Unrealistic Challenges 08:23 - Designing CTF Challenges is Hard 08:50 - Playing CTFs as a Professional 09:04 - Outro -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Instagram: https://www.instagram.com/liveoverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

bxzrtU7VtPU | 11 May 2020
In this part two we investigate how encountering a glitch pokemon will cause the 6th item to multiply. For this we are using Ghidra and SameBoy to debug and reverse engineer the code. Part 1: https://www.youtube.com/watch?v=p8OBktd42GI Want to understand how to catch Mew? https://www.youtube.com/watch?v=U8fWTDUdWGA&list=PLniOzp3l9V82onKsktyyKlIenAAUj45Mk&index=6&t=0s Checkout the whole GameBoy hacking playlist with stacksmashing: https://www.youtube.com/playlist?list=PLniOzp3l9V82onKsktyyKlIenAAUj45Mk PwnAdventure Game Hacking Series: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG GhidraBoy: https://github.com/Gekkio/GhidraBoy SameBoy: https://github.com/LIJI32/SameBoy -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

p8OBktd42GI | 02 May 2020
We are using an emulator to research what triggers MissingNo and come up with a hypothetical story how one could have found and analyzed this glitch. GameBoy Hacking Playlist: https://www.youtube.com/watch?v=ix5yZm4fwFQ&list=PLniOzp3l9V82onKsktyyKlIenAAUj45Mk Checkout Stacksmashing's video about modifying GameBoy games: https://www.youtube.com/watch?v=dQLp5i8oS3Y&list=PLniOzp3l9V82onKsktyyKlIenAAUj45Mk&index=3 Coincidentally somebody else also just made a video about MissingNo, going into the details of the Sprite: https://www.youtube.com/watch?v=ZI50XUeN6QE -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

8Z1D64qfrxM | 24 Apr 2020
We finally managed to make a fly hack to zoom around the map and we learned a lot about Windows game hacking in the process. This is the last video in the PwnAdventure game hacking series. Full playlist watch here: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG Previous Episode: https://www.youtube.com/watch?v=Xd_egp8WeKE -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

VVbRe7wr3G4 | 15 Apr 2020
Reverse engineering the savegame data of Pokemon Red for the GameBoy. Let's learn something about the GameBoy hardware and how Cartridges are special. stacksmashing: https://www.youtube.com/channel/UC3S8vxwRfqLBdIhgRlDRVzw GBDev: https://gbdev.gg8.se/ Bulbapedia: https://bulbapedia.bulbagarden.net/wiki/Save_data_structure_in_Generation_I -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

BwoOB2QFXvw | 06 Apr 2020
An example why I love the internet. There are people still exploring the 1997 game Frogger! In this video we will look at an old compression algorithm to learn how a compression works in general. Kneesnap reverse engineered an old compression algorithm for his modding tool FrogLord. It can be used to unpack and repack game assets. Highway Frogs Forum: https://highwayfrogs.net/ Modding Tool: https://github.com/Kneesnap/FrogLord Investigating the Frogger Modding Community: https://www.youtube.com/watch?v=rQHroM7rY0A Out of Bounds Secrets | Frogger (PS1) - Boundary Break: https://www.youtube.com/watch?v=_2WAW59tG3E -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

f-FbcobQQb8 | 01 Apr 2020
As it is well-known, I invented security.txt. And I'm really proud about it. And I want to tell everybody. Check it out here: https://securitytxt.org/ SPOILERS AHEAD: obviously a joke, duh! - EdOverflow (https://twitter.com/edoverflow) invented security.txt and people confuse us all the time. EdOverflow vs. LiveOverflow. You get it. I hope nobody actually thought I was this self-absorbed as I acted in this video. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.
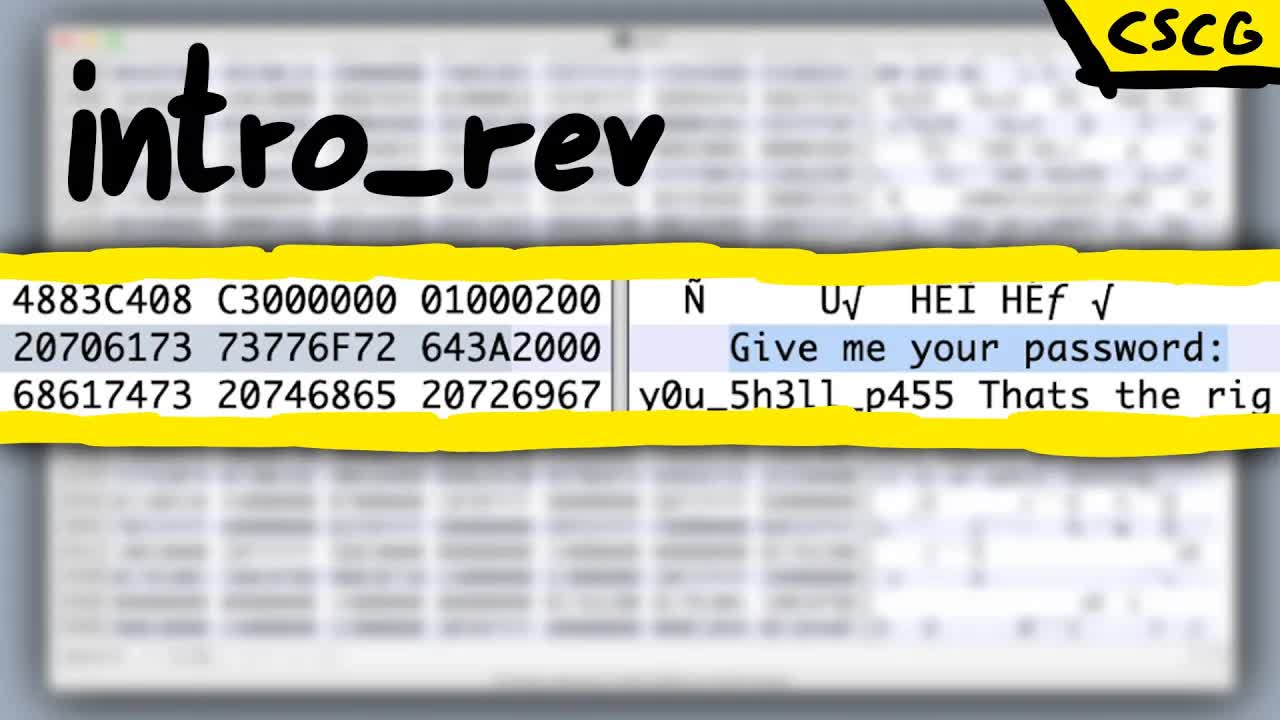
28JHPOUZvDw | 25 Mar 2020
Introduction video for the intro to reversing challenges of CSCG 2020: https://www.cscg.de/cscg/teilnehmen/ Challenge intro_rev/rev1: https://earth.2020.cscg.de/tasks/Intro%20to%20Reversing%201 Binary Exploitation playlist (contains videos about reversing basics and working with gdb): https://www.youtube.com/playlist?list=PLhixgUqwRTjxglIswKp9mpkfPNfHkzyeN Pwn Adventure 3 - contains some gdb and reversing videos: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

hhu7vhmuISY | 18 Mar 2020
Solving the part 1 of the intro pwnable challenges of our CTF. After this try part 2 and part 3 yourself! International players: https://earth.2020.cscg.de/ CSCG 2020 (german): https://www.cscg.de/cscg/teilnehmen/ Introduction to docker workflow: https://www.youtube.com/watch?v=cPGZMt4cJ0I Basic pwnable challenge: https://www.youtube.com/watch?v=OqTpc_ljPYk Some more resources: https://github.com/LiveOverflow/pwn_docker_example intro_pwn/pwn1: https://earth.2020.cscg.de/tasks/Intro%20to%20Pwning%201 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

J2icGMocQds | 11 Mar 2020
This video is sponsored by Google. In 2019, Google announced the GCP Prize. 100.000$ for the best bug bounty report for the Google Cloud Platform. Today we will have a look at the nominations! Blog: https://security.googleblog.com/2020/03/announcing-our-first-gcp-vrp-prize.html Nominations: [Obmi] The File uploading CSRF in Google Cloud Shell Editor: https://obmiblog.blogspot.com/2019/12/gcp-5k-file-uploading-csrf.html [Wouter] 4 Google Cloud Shell bugs explained: https://offensi.com/2019/12/16/4-google-cloud-shell-bugs-explained-introduction/ [Psi] CSWSH vulnerability in Google Cloud Shell’s code editor: https://xn--9xa.fun/i/yvpMj Free GCP tier: https://cloud.google.com/free/docs/gcp-free-tier Google Security Blog: https://security.googleblog.com/ GCP Price Blog Post: https://security.googleblog.com/2019/08/awarding-google-cloud-vulnerability.html Video with Wouter about Cloud Shell: https://www.youtube.com/watch?v=E-P9USG6kLs -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

kLZdnvvQRKY | 04 Mar 2020
We founded a new association to organise CTF competitions and more to support young it security talents. This years qualification round for the Cyber Security Challenge Germany is starting now. Teilnehmen (deutsch): https://www.cscg.de/cscg/teilnehmen/ International players: https://earth.2020.cscg.de Participate in other European Countries: https://ecsc.eu/2020-challenge Our new association "Nachwuchsförderung IT-Sicherheit": https://www.nfits.de -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.
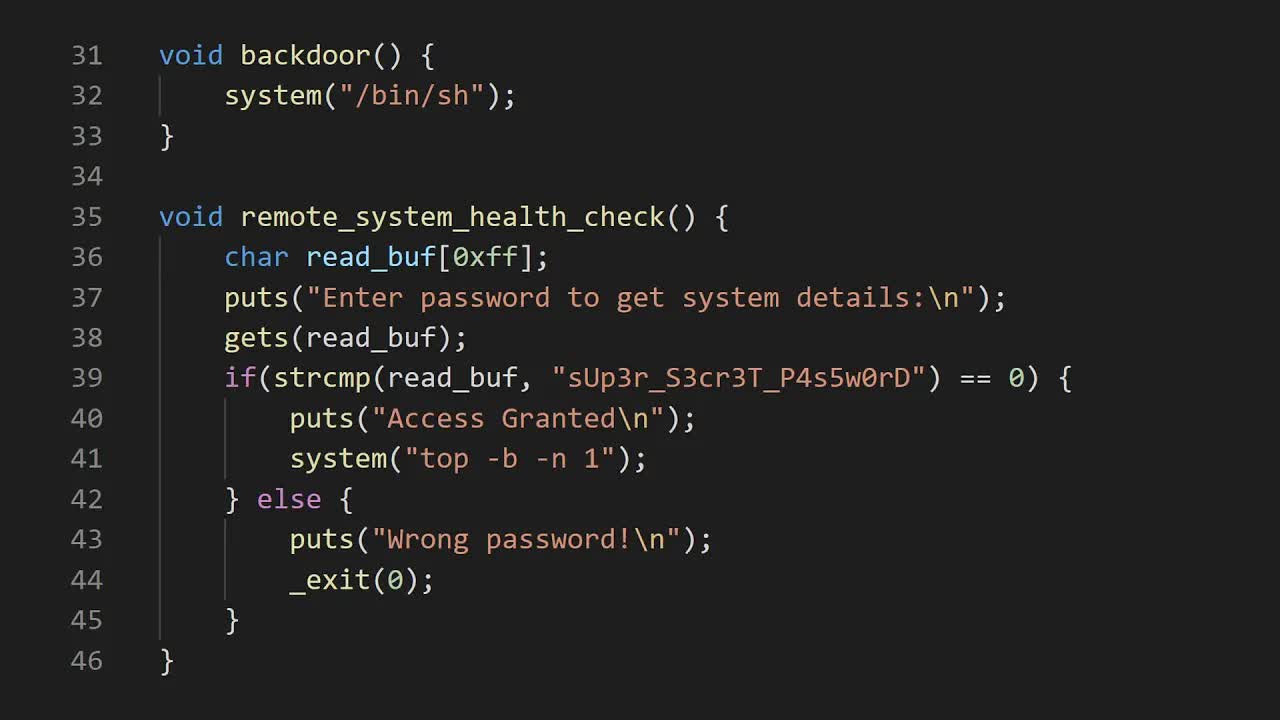
OqTpc_ljPYk | 29 Feb 2020
A very simple pwnable challenge to checkout the docker workflow. pwn_docker_example: https://github.com/LiveOverflow/pwn_docker_example -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

sHp0Q3rvamk | 26 Feb 2020
Let's play around with Docker a bit more. We learn about the nsenter command, how kernel code execution allows escaping from docker and we look at Linux Kernel source code of getpid(). Daniel Mitre's blog: https://medium.com/@flag_seeker/linux-container-from-scratch-339c3ba0411d bocker: https://github.com/p8952/bocker/ Elixir: https://elixir.bootlin.com/linux/latest/source/kernel/sys.c#L891 Denis Andzakovic: https://pulsesecurity.co.nz/articles/docker-rootkits -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

-YnMr1lj4Z8 | 21 Feb 2020
Let's figure out how Docker works! We will investigate docker by tracing the syscalls to find the Linux Kernel feature called Namespaces. We also learn about the different ones like process id, network or mount namespaces. docker → dockerd → containerd → runC → unshare syscall Part 1: https://www.youtube.com/watch?v=cPGZMt4cJ0I LWN Article: https://lwn.net/Articles/531114/ Docker Example: https://github.com/LiveOverflow/pwn_docker_example -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

cPGZMt4cJ0I | 14 Feb 2020
I'm using docker more often for CTFs, but it's also useful to host challenges. More CTFs share Dockerfiles to run it locally, so I figured it's time to give an introduction to docker. If you have some other tips or tricks about your workflow, please share it below! Example challenge and CTF container: https://github.com/LiveOverflow/pwn_docker_example DigitalOcean*: https://m.do.co/c/826f195e2288 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

kMesRjygnRM | 24 Dec 2019
This was a mistake. The full playlist is here: https://www.youtube.com/playlist?list=PLhixgUqwRTjzTvVyL_8H-DJBf8VT3uiu2 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.
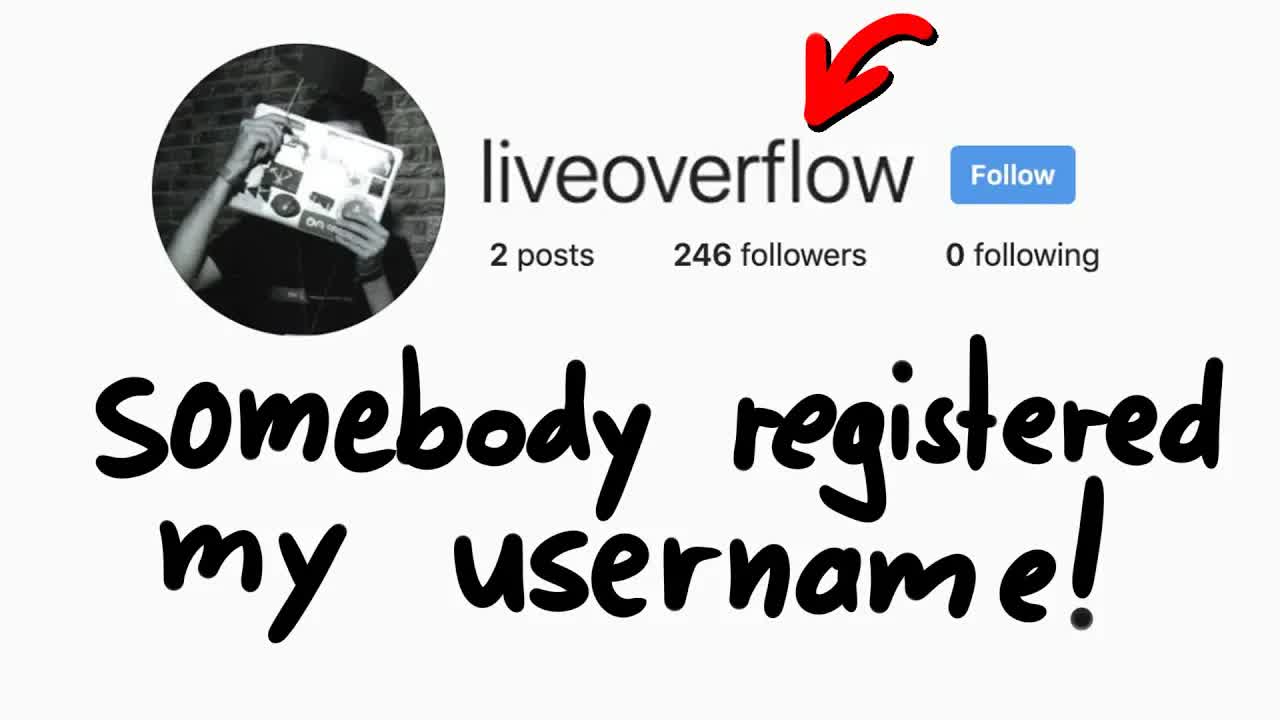
zXIR-23e91M | 23 Dec 2019
Somebody registered my name on Instagram. How did I get the account? I had to nuke the comments because of massive spam of fake hacking offers by bots. Don't fall for it. follow me: https://www.instagram.com/liveoverflow/ -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

PbipefyfkNY | 22 Dec 2019
My friend showed me how physics can be used to extract a signal from a fiber without having to destroy it. This kind of fiber tapping could be a threat for long-distance fiber networks. -=[ 🔴 Stuff I use ]=- → Microphone:* https://amzn.to/2LW6ldx → Graphics tablet:* https://amzn.to/2C8djYj → Camera#1 for streaming:* https://amzn.to/2SJ66VM → Lens for streaming:* https://amzn.to/2CdG31I → Connect Camera#1 to PC:* https://amzn.to/2VDRhWj → Camera#2 for electronics:* https://amzn.to/2LWxehv → Lens for macro shots:* https://amzn.to/2C5tXrw → Keyboard:* https://amzn.to/2LZgCFD → Headphones:* https://amzn.to/2M2KhxW -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

1hScemFvnzw | 21 Dec 2019
In the suidbash CTF challenge there was an inconspicuous line of code, but it was actually there to prevent a race condition. Let's talk about it this video! Source code: https://gist.github.com/LiveOverflow/69ebf4322c9eb2f6a7774204f82c9fe0 -=[ 🔴 Stuff I use ]=- → Microphone:* https://amzn.to/2LW6ldx → Graphics tablet:* https://amzn.to/2C8djYj → Camera#1 for streaming:* https://amzn.to/2SJ66VM → Lens for streaming:* https://amzn.to/2CdG31I → Connect Camera#1 to PC:* https://amzn.to/2VDRhWj → Camera#2 for electronics:* https://amzn.to/2LWxehv → Lens for macro shots:* https://amzn.to/2C5tXrw → Keyboard:* https://amzn.to/2LZgCFD → Headphones:* https://amzn.to/2M2KhxW -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

QNZfdqTAvYM | 20 Dec 2019
Actual first vlog! It's part 1 of traveling to London for the Google CTF. In this video I cover my arrival and the first day trip with bug hunters to Bletchley Park to learn more about the Enigma machine. -=[ 🔴 Stuff I use ]=- → Microphone:* https://amzn.to/2LW6ldx → Graphics tablet:* https://amzn.to/2C8djYj → Camera#1 for streaming:* https://amzn.to/2SJ66VM → Lens for streaming:* https://amzn.to/2CdG31I → Connect Camera#1 to PC:* https://amzn.to/2VDRhWj → Camera#2 for electronics:* https://amzn.to/2LWxehv → Lens for macro shots:* https://amzn.to/2C5tXrw → Keyboard:* https://amzn.to/2LZgCFD → Headphones:* https://amzn.to/2M2KhxW -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

FxNS-zSS7MQ | 19 Dec 2019
Another pitfall when developing exploits with python. And also including some general beginner advice about python. -=[ 🔴 Stuff I use ]=- → Microphone:* https://amzn.to/2LW6ldx → Graphics tablet:* https://amzn.to/2C8djYj → Camera#1 for streaming:* https://amzn.to/2SJ66VM → Lens for streaming:* https://amzn.to/2CdG31I → Connect Camera#1 to PC:* https://amzn.to/2VDRhWj → Camera#2 for electronics:* https://amzn.to/2LWxehv → Lens for macro shots:* https://amzn.to/2C5tXrw → Keyboard:* https://amzn.to/2LZgCFD → Headphones:* https://amzn.to/2M2KhxW -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

5g137gsB9Wk | 18 Dec 2019
In this video we look at a typical race condition involving file paths. We learn about the renameat syscall to exploit it and also how to fix it. Source code: https://gist.github.com/LiveOverflow/590edaf5cf3adeea31c73e303692dec0 -=[ 🔴 Stuff I use ]=- → Microphone:* https://amzn.to/2LW6ldx → Graphics tablet:* https://amzn.to/2C8djYj → Camera#1 for streaming:* https://amzn.to/2SJ66VM → Lens for streaming:* https://amzn.to/2CdG31I → Connect Camera#1 to PC:* https://amzn.to/2VDRhWj → Camera#2 for electronics:* https://amzn.to/2LWxehv → Lens for macro shots:* https://amzn.to/2C5tXrw → Keyboard:* https://amzn.to/2LZgCFD → Headphones:* https://amzn.to/2M2KhxW -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

oS2O75H57qU | 17 Dec 2019
Feel free to follow along! Just a simple buffer overflow walkthrough. sources and solution: https://gist.github.com/LiveOverflow/5fa36bec51968de696b11d3548b02148 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

Xvh8FkczNUc | 16 Dec 2019
In this video we see two more common pitfalls that you want to avoid when you get started with binary exploitation. -=[ 🔴 Stuff I use ]=- → Microphone:* https://amzn.to/2LW6ldx → Graphics tablet:* https://amzn.to/2C8djYj → Camera#1 for streaming:* https://amzn.to/2SJ66VM → Lens for streaming:* https://amzn.to/2CdG31I → Connect Camera#1 to PC:* https://amzn.to/2VDRhWj → Camera#2 for electronics:* https://amzn.to/2LWxehv → Lens for macro shots:* https://amzn.to/2C5tXrw → Keyboard:* https://amzn.to/2LZgCFD → Headphones:* https://amzn.to/2M2KhxW -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

3xIj8Xyx1TU | 15 Dec 2019
The website explainshell.com is a really neat tool that can make learning the basics easier. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

j70AA9arThc | 14 Dec 2019
This video contains its own Video ID. After I uploaded the video I found out it has been done before: https://www.youtube.com/watch?v=sLsVCNlWJTQ https://www.youtube.com/watch?v=YHuStFJR1_A YouTube API: https://developers.google.com/youtube/v3/docs/videos/insert -------------------------------------- Twitter: https://twitter.com/LiveOverflow Website: http://liveoverflow.com/ Subreddit: https://www.reddit.com/r/LiveOverflow/ Facebook: https://www.facebook.com/LiveOverflow/

LyNyf3UM9Yc | 13 Dec 2019
A long time ago I made a video about the basics of cracking, but never got around to make a video about actually patching the binary. So here I show you a few methods how to do it! -=[ 🔴 Stuff I use ]=- → Microphone:* https://amzn.to/2LW6ldx → Graphics tablet:* https://amzn.to/2C8djYj → Camera#1 for streaming:* https://amzn.to/2SJ66VM → Lens for streaming:* https://amzn.to/2CdG31I → Connect Camera#1 to PC:* https://amzn.to/2VDRhWj → Camera#2 for electronics:* https://amzn.to/2LWxehv → Lens for macro shots:* https://amzn.to/2C5tXrw → Keyboard:* https://amzn.to/2LZgCFD → Headphones:* https://amzn.to/2M2KhxW -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

juGNPLdjLH4 | 12 Dec 2019
If you want to hack the Kernel, are interested in jailbreaks or just want to understand computers better, Linux Device Drivers is a great book to get you started. I used to learn the basics and in this video I want to share what *clicked* for me. LDD Book: https://lwn.net/Kernel/LDD3/ LDD3 Example Code Updated: https://github.com/martinezjavier/ldd3 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

qNLMuls2BBA | 11 Dec 2019
I think it's good to get an insight into the pentesting industry, by looking at public reports. There is a great repository collecting some. You can see here how different they are, and what is similar. GitHub repository: https://github.com/juliocesarfort/public-pentesting-reports -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

YV3jewkUJ54 | 10 Dec 2019
Ned Williamson of Google Project Zero explains how he discovered the Sock Puppet vulnerability affecting the XNU Kernel in iOS and macOS. He also shows us what primitives the bug provides and how it can be exploited. This is only the first stage of a Jailbreak, but it's a very valuable kernel bug. Google Project Zero Blog: https://googleprojectzero.blogspot.com/2019/12/sockpuppet-walkthrough-of-kernel.html Ned on Twitter: https://twitter.com/NedWilliamson Ned Williamson - Modern Source Fuzzing (OffensiveCon19): https://www.youtube.com/watch?v=xzG0pLM4Q64 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

HJy-Y4nok3g | 09 Dec 2019
I spent a lot of time in a hackerspace during my university time. I loved that place! I learned so much there, the atmosphere is so nice and I made a lot of valuable connections there. Check if you have a hackerspace near you: http://hackerspaces.org/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

Lus7aNf2xDg | 08 Dec 2019
In this video I just want to explain how to approach CTFs for learning. It's not about solving challenges and not about winning. CTFtime: https://ctftime.org/ What is CTF? An introduction to security Capture The Flag competitions: https://www.youtube.com/watch?v=8ev9ZX9J45A -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

3IEAfyQqUKc | 07 Dec 2019
Being the two time Cyber Security Challenge Germany winner I get a lot of questions. Here I'm talking about what frustrates me and how to do it better. FYI: Before posting this video, I have sent it to the redditor and asked if it's okay to share. The person thought it's funny and we ended up having a several hour long 1:1 session to solve the challenge ;) win-win! How (not) to ask a technical question video: https://www.youtube.com/watch?v=53zkBvL4ZB4 The reddit thread: https://www.reddit.com/r/LiveOverflow/comments/e0le0d/buffer_overflow_on_linux_binary_statically_linked/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

pphfcaGnWSA | 06 Dec 2019
A typical error in gdb with setting breakpoints when dealing with binaries affected by ASLR is: "Cannot access memory at address 0x807". This can be quite frustrating at the beginning, especially if you don't know much about PIE yet. In this video I want to cover a few different ways how you can still debug them with gdb and Ghidra. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

TX18KQq67Tg | 05 Dec 2019
What operating system do hackers use for ethical hacking, pentesting, ...? Gynvael's Windows Setup: https://www.youtube.com/watch?v=OHGysGcRFFI Gynvael's English Channel: https://www.youtube.com/user/GynvaelEN Digital Ocean*: https://m.do.co/c/826f195e2288 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

CgGha_zLqlo | 04 Dec 2019
Some Linux binaries are statically linked and it's more difficult to work with it. In this video we learn about FLIRT function signatures and use a Ghidra plugin to apply them. This will help us reverse engineer the binary. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

N1US3c6CpSw | 03 Dec 2019
Stripped binaries miss the symbol information of functions and variables. Debugging such a binary is a little bit more tricky, but there is a simple method to find the main() function of the program. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

VCwiZ2dh17Q | 02 Dec 2019
Today I will share the secret underground forum where we chat and exchange information about hacking. Here you can learn new skills and listen to the best hackers in the world talk. You should signup too. Link to secret forum: https://twitter.com/ My account: https://twitter.com/LiveOverflow 1337List (currently not available): https://twitter.com/1337list -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

re4teYmSoXA | 01 Dec 2019
I often get questions about not working exploits. Sometimes the problem is the shellcode. In this video we look at different ways to debug the shellcode and find the issue. Haxember 2019 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzTvVyL_8H-DJBf8VT3uiu2 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

-wGtxJ8opa8 | 27 Nov 2019
An actual 0-day in /bin/bash due to a bug in the privilege dropping feature. It was discovered by Ian Pudney and turned into a CTF challenge for the Google CTF 2019 Finals. CVE-2019-18276 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow → Website: https://liveoverflow.com/ → Instagram: https://instagram.com/liveoverflow → Subreddit: https://www.reddit.com/r/LiveOverflow → Facebook: https://www.facebook.com/LiveOverflow -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

24oUDQ_6WDM | 02 Nov 2019
Just a test VLOG. I released it for Patrons and YouTube Members first, and then asked them if I should make it public. The majority said yes, so here it is. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

Xd_egp8WeKE | 30 Oct 2019
Another PwnAdventure episode. We are very close to a fly hack! But this time I got some help with creating a .dll for a DLL injection. And then we can use the pointer paths we have found last video, to read the player position from the Pwn Adventure 3 game process. 🌴 PwnAdventure Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG GuidedHacking: https://www.youtube.com/channel/UCCMi6F5Ac3kQDfffWXQGZDw Stephen Chapman: https://www.youtube.com/channel/UCqfqH-wq12WOm4QG4KiRisw Stackexchange: https://reverseengineering.stackexchange.com/questions/18144/need-help-with-reverse-engineering-camera-related-information-in-a-video-game/18178#18178 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

E-P9USG6kLs | 01 Oct 2019
Conversation with a bug bounty hunter about a vulnerability found in Google Cloud Shell. This video is sponsored by Google (Vulnerability Rewards Program) ↓ Check the links Google VRP: https://www.google.com/about/appsecurity/reward-program/ Cloud Shell PoC exploit (fixed): https://github.com/offensi/LiveOverflow-cloudshell-poc Cloud Shell docker "escape": https://github.com/offensi/LiveOverflow-cloudshell-stuff Theia IDE: https://theia-ide.org/ wtm: https://twitter.com/wtm_offensi -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

yAl_6qg6ZnA | 13 Sep 2019
We continue doing some Cheat Engine work to find the player's position and camera position. This will help us to implement a fly hack in a future episode. blog: https://liveoverflow.com/player-and-camera-position-for-fly-hack-pwn-adventure-3-2/ playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

elI6vZR6HGE | 20 Aug 2019
We continue our journey in Windows Game hacking with Pwn Adventure 3, by looking at Pointer Scans from Cheat Engine. And surprisingly the same techniques are being used by speedrunners to implement automatic time splitters. 🌴 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG Pwn Adventure 3: https://www.pwnadventure.com/ glurmo's speedrun: https://www.youtube.com/watch?v=_5DUdCYv0pU -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

Pst-4NwY2is | 04 Aug 2019
We are going to learn basic game hacking on Windows with Cheat Engine and Ghidra. Pwn Adventure 3 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG blog: https://liveoverflow.com/getting-started-with-windows-game-hacking-pwn-adventure-3/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

nI8Q1bqT8QU | 28 Jul 2019
Solving the Minetest Hardware Challenge from the Google CTF 2019 Qualifier. * Google CTF: https://capturetheflag.withgoogle.com * Solution Script: https://gist.github.com/LiveOverflow/1480ee7e1ffead942063c638d5b66804 * blog: https://liveoverflow.com/minetest/ -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

uY4FQNwS4ME | 21 Jul 2019
We are finally achieving arbitrary read/write and talk about the various possibilities we have now. blog: https://liveoverflow.com/preparing-for-stage-2-of-a-webkit-exploit-browser-0x07-2/ -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

3c6nC0wdU-Q | 14 Jul 2019
Part 7: In this video we use the stage 1 fakeobj() and addrof() primitives, to craft malicious objects that allow us to implement arbitrary memory read and write. saelo's phrack paper: http://www.phrack.org/papers/attacking_javascript_engines.html niklasb's exploit: https://github.com/niklasb/sploits/blob/master/safari/regexp-uxss.html -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BrowserExploitation

gBL6IzwIjuA | 07 Jul 2019
Simple buffer overflow speedrun challenge, exploited with a ROP chain generated by Ropper. And analyse the timeline. blog: https://liveoverflow.com/speedrun-hacking-buffer-overflow-speedrun-001-dc27-2/ -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

LIdZ2oPyB1Y | 04 Jul 2019
Bonus Video: https://www.youtube.com/watch?v=PJJKvupvU4Q -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

dhaLk-XO890 | 30 Jun 2019
Part 6: There are still many things I haven't explained yet. So in this video we go over the boxed vs. unboxed values, how to convert Integer addresses to Doubles and why our bug is a memory corruption. blog: https://liveoverflow.com/revisiting-javascriptcore-internals-boxed-vs-unboxed-browser-0x06/ test.js: https://gist.github.com/LiveOverflow/71bcf3f364c9719998bf159923310019 The Exploit:https://github.com/LinusHenze/WebKit-RegEx-Exploit Playlist: https://www.youtube.com/watch?v=5tEdSoZ3mmE&list=PLhixgUqwRTjwufDsT1ntgOY9yjZgg5H_t -=[ 🕴️Advertisement ]=- This video is supported by SSD Secure Disclosure: https://ssd-disclosure.com/ Offensive Security Conference TyphoonCon: https://typhooncon.com/ Challenge: https://typhooncon.com/typhooncon-challenge-2019/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

zjriIehgAec | 26 Jun 2019
The pretty paste solution! Livestream about going through the solution for the web challenge pastetastic. We learn about DOM clobbering, absuing Chrome's XSS auditor and how the same-origin applies to iframes. Twitch: https://twitch.tv/liveoverflow LiveOverflow2: https://www.youtube.com/channel/UCNNfzr9A5dEOscVEDyyzo-A Full Stream: https://www.youtube.com/watch?v=c4ewF9bhJuU -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

vwlG2l0ANuc | 23 Jun 2019
Part5: In this video we turn the bug used in addrof() to corrupt the memory of internal JavaScriptCore Objects which can help us to compromise the engine. The Exploit: https://github.com/LinusHenze/WebKit-RegEx-Exploit Saelo's exploit: https://github.com/saelo/cve-2018-4233/blob/master/pwn.js Saelo's phrack paper: http://www.phrack.org/papers/attacking_javascript_engines.html -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BrowserExploitation

3yLKcwGsiBk | 16 Jun 2019
Join me on Twitch: https://twitch.tv/liveoverflow LiveOverflow2: https://www.youtube.com/channel/UCNNfzr9A5dEOscVEDyyzo-A -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

IjyDsVOIx8Y | 16 Jun 2019
Part 4: We finally look at the actual exploit code. We start by understanding the addrof() primitive used to leak the address of a JavaScript object in memory. test.js: https://gist.github.com/LiveOverflow/ee5fb772334ec985094f77c91be60492 Crash investigation: https://webkit.org/blog/6411/javascriptcore-csi-a-crash-site-investigation-story/ The Exploit: https://github.com/LinusHenze/WebKit-RegEx-Exploit The Fix: https://github.com/WebKit/webkit/commit/7cf9d2911af9f255e0301ea16604c9fa4af340e2?diff=split#diff-fb5fbac6e9d7542468cfeed930e241c0L66 Saelo's exploit: https://github.com/saelo/cve-2018-4233/blob/master/pwn.js Playlist: https://www.youtube.com/watch?v=5tEdSoZ3mmE&list=PLhixgUqwRTjwufDsT1ntgOY9yjZgg5H_t -=[ 🕴️Advertisement ]=- This video is supported by SSD Secure Disclosure: https://ssd-disclosure.com/ Offensive Security Conference TyphoonCon: https://typhooncon.com/ -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #browserexploitation

45wMEIIPsPA | 09 Jun 2019
Part 3: Introducing the JavaScript interpreter, DFG JIT and FTL JIT from WebKit in this third part. To do that we use the debug version of JSC again and use environment variables to print useful debug output. Crash investigation: https://webkit.org/blog/6411/javascriptcore-csi-a-crash-site-investigation-story/ ZDI: https://www.thezdi.com/blog/2018/4/12/inverting-your-assumptions-a-guide-to-jit-comparisons Playlist: https://www.youtube.com/watch?v=5tEdSoZ3mmE&list=PLhixgUqwRTjwufDsT1ntgOY9yjZgg5H_t -=[ 🕴️Advertisement ]=- This video is supported by SSD Secure Disclosure: https://ssd-disclosure.com/ Offensive Security Conference TyphoonCon (10th - 14th June 2019): https://typhooncon.com/ -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

KVpHouVMTgY | 02 Jun 2019
Part 2: Let's have a look at how JavaScriptCore implements JavaScript Objects and values like integers and floats. We can use lldb to look into the memory. Phrack: http://phrack.org/papers/attacking_javascript_engines.html The Linus: https://twitter.com/linushenze The Exploit: https://github.com/LinusHenze/WebKit-RegEx-Exploit The Fix: https://bugs.webkit.org/show_bug.cgi?id=191731 -=[ 🕴️Advertisement ]=- This video is supported by SSD Secure Disclosure: https://ssd-disclosure.com/ Offensive Security Conference TyphoonCon (10th - 14th June 2019): https://typhooncon.com/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BrowserExploitation

yJewXMwj38s | 26 May 2019
Part 1: We are going to try out Linus's exploit and setup a vulnerable WebKit version including debug symbols. The Linus: https://twitter.com/linushenze The Exploit: https://github.com/LinusHenze/WebKit-RegEx-Exploit The Vulnerable Commit: 3af5ce129e6636350a887d01237a65c2fce77823 The Fix: https://bugs.webkit.org/show_bug.cgi?id=191731 saelo's german presentation: https://www.youtube.com/watch?v=1RLt7yscBZc -=[ 🕴️ Advertisement ]=- This video is supported by SSD Secure Disclosure: https://ssd-disclosure.com/ Offensive Security Conference TyphoonCon (10th - 14th June 2019): https://typhooncon.com/ -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BrowserExploitation

5tEdSoZ3mmE | 19 May 2019
The start of a new series. We will try to learn some basics about Browser Exploitation. blog: https://liveoverflow.com/getting-into-browser-exploitation-new-series-introduction-browser-0x00/ -=[ 🕴️Advertisement ]=- This video is supported by SSD Secure Disclosure: https://ssd-disclosure.com/ Offensive Security Conference TyphoonCon (10th - 14th June 2019): https://typhooncon.com/ -=[ 🗄️ References ]=- Linus's Exploit: https://github.com/LinusHenze/WebKit-RegEx-Exploit Niklas's Exploit: https://github.com/niklasb/sploits/blob/master/safari/regexp-uxss.html ZDI's Blog: https://www.zerodayinitiative.com/blog/2019/3/14/the-apple-bug-that-fell-near-the-webkit-tree Saelo's german class: https://www.youtube.com/watch?v=1RLt7yscBZc Saelo's Attacking JavaScript Engines: http://www.phrack.org/papers/attacking_javascript_engines.html ret2system's blog: http://blog.ret2.io/2018/06/05/pwn2own-2018-exploit-development/ -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BrowserExploitation

3MAqlEMITzw | 12 May 2019
Where does the term "script kiddie" come from? Who said it first? Let's do some hacker history research! blog: https://liveoverflow.com/the-origin-of-script-kiddie-hacker-etymology/ r00t crongrab: http://www.r00t.org/advisories/r00t.advisory.97.crongrab.html H2K2 (2002): "The Conscience of a Hacker" https://www.youtube.com/watch?v=0tEnnvZbYek YABBS hack: http://textfiles.com/messages/YABBS/hack Prack: http://www.phrack.org/ Textfiles: http://textfiles.com/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

YXnNO3TipvM | 05 May 2019
OALabs shows a walk-through of how to unpack a sample malware and explains some basics about packers. You can learn about using x64debug, IDA and PE-Bear. OALabs: https://www.youtube.com/channel/UC--DwaiMV-jtO-6EvmKOnqg -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #MalwareAnalysis

kLixcdwHrFM | 28 Apr 2019
A vlog with a recap about the last year, how LiveOverflow is now a business and generally what is going on behind the scenes. blog post: https://liveoverflow.com/business-money-300k-subs-and-whats-next/ -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

LrLJuyAdoAg | 21 Apr 2019
Video write-up about the Real World CTF challenge "flaglab" that involved exploiting a gitlab 1day. Actually two CVEs are combined to achieve full remote code execution: CVE-2018-19571 (SSRF) + CVE-2018-19585 (CRLF) = RCE flaglab - docker-compose: https://gist.github.com/LiveOverflow/8bf92dd86e5c481fb484af83c64e83b3#file-docker-compose-yml Release: https://about.gitlab.com/2018/11/28/security-release-gitlab-11-dot-5-dot-1-released/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #CVE

yq_P3dzGiK4 | 14 Apr 2019
We have a look at another interesting XSS vector due to weird Firefox parsing, and then explore how researchers find this stuff. Gareth's tweet: https://twitter.com/garethheyes/status/1112661895067156481 insertScript's vector: http://shazzer.co.uk/vector/lt-eating-char -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

gVrdE6g_fa8 | 07 Apr 2019
We will go over a few puzzle pieces and discuss XSS research... and we find evidence of a XSS conspiracy!!11!!!1! 😱 fuzzing: https://gist.github.com/LiveOverflow/dd3d09d17c8fc0460c7e9a337b501331 -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

Fr8K8p8YR5c | 01 Apr 2019
1. April 2018: https://www.youtube.com/watch?v=ujaBCDaPUm0 2017: https://www.youtube.com/watch?v=2LOtBpA7W_M -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #MakingOf #LiveStream

lG7U3fuNw3A | 31 Mar 2019
An actual XSS on google.com by Masato Kinugawa. It abuses a parsing differential between a JavaScript enabled and disabled context. The fix: https://github.com/google/closure-library/commit/c79ab48e8e962fee57e68739c00e16b9934c0ffa -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

zaQVNM3or7k | 24 Mar 2019
There are a lot of tutorials on ROP out there, so I try to explain the concept in a different way. Maybe that's a bad idea and a lot more confusing. But if you didn't understand it yet, or you already know ROP, then this could be interesting. What Hacker Research Taught Me: https://www.youtube.com/watch?v=Dd9UtHalRDs Science of Insecurity: https://www.youtube.com/watch?v=3kEfedtQVOY A Patch for Postel’s Robustness Principle: http://langsec.org/papers/postel-patch.pdf Exploit Programming From Buffer Overflows to “Weird Machines” and Theory of Computation: http://langsec.org/papers/Bratus.pdf -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

8Dcj19KGKWM | 17 Mar 2019
Let's introduce the concept of a weird machine in order to understand ROP differently. It's maybe a bad tutorial. What Hacker Research Taught Me: https://www.youtube.com/watch?v=Dd9UtHalRDs Science of Insecurity: https://www.youtube.com/watch?v=3kEfedtQVOY A Patch for Postel’s Robustness Principle: http://langsec.org/papers/postel-patch.pdf Exploit Programming From Buffer Overflows to “Weird Machines” and Theory of Computation: http://langsec.org/papers/Bratus.pdf -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BinaryExploitation

WP-EnGhIYEc | 10 Mar 2019
In this video we go over how smart contracts written in solidity are deployed, and how the Acoraida Monica contract was backdoored. Acoraida Monica - Real World CTF Part 1: https://www.youtube.com/watch?v=ozqOlUVKL1s Part 2: https://www.youtube.com/watch?v=RfL3FcnVbJg -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #SmartContract

qtoS3CG6ht0 | 06 Mar 2019
Get Ghidra: https://ghidra-sre.org/ Streamers: https://www.twitch.tv/syrillian https://www.twitch.tv/malwaretechblog https://www.youtube.com/channel/UCVeW9qkBjo3zosnqUbG7CFw (John Hammond) https://www.youtube.com/watch?v=Ml8bfFs_Tp8 gamozolabs -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #MakingOf #LiveStream

2H45HheGkKM | 03 Mar 2019
We finally figure out how to create a firmware update, but we run into an annoying check. But based on what we have learned so far, we can find a bypass - rediscovering the f00dbabe issue. research: https://wallet.fail DISCLAIMER: The security research shown here was done a while ago and since then the software and hardware was updated; These videos are not sponsored or endorsed by Ledger. -=[ 💻 Related Products ]=- → Ledger Nano S:* https://amzn.to/2VAhMvM → USB Hub with switches:* https://amzn.to/2SJuaYv → any STM32 Nucleo-64 development board:* https://amzn.to/2VDDE9J -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #HardwareSecurity #ReverseEngineering

5cvpGSSUZI0 | 24 Feb 2019
This is another challenge of the FLARE-On 2018 CTF. This challenge is about analysing the functionality of a Firefox malware, but I got really lucky :D -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #MalwareAnalysis #ReverseEngineering #CTF

866olNIzbrk | 17 Feb 2019
When is a vulnerability actually a vulnerability? I can't answer this question easily, and thus we look at a few examples in this video. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

LntSN7JsR_A | 11 Feb 2019
We are doing a live stream where we go over the GameDev challenge and announce the winners. challenge details: https://gynvael.coldwind.pl/?id=697 the games: http://gwgc2018.gynvael.tv/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #GameDevChallenge

TLWBeKicsa0 | 10 Feb 2019
We are looking at the protocol between the device and host PC. With the old source code it's pretty easy to find the loop that handles APDU messages. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #ReverseEngineering #HardwareSecurity

2SSZs7coCKQ | 05 Feb 2019
In this guest video 13cubed shows us some forensics work combining data from fls and volatility and then exploring the data with Timeline Explorer 13cubed: https://www.youtube.com/channel/UCy8ntxFEudOCRZYT1f7ya9Q Richard Davis: https://twitter.com/davisrichardg B -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #Forensics

yJbnsMKkRUs | 01 Feb 2019
Now that we know where the firmware starts, we want to find how button presses are handled and where it might handle the APDU commands. research: https://wallet.fail AVR Firmware: https://www.youtube.com/watch?v=hyoPAOTrUMc ZetaTwo: https://www.youtube.com/user/ZetaTwo DISCLAIMER: The security research shown here was done a while ago and since then the software and hardware was updated; These videos are not sponsored or endorsed by Ledger. -=[ 💻 Related Products ]=- → Ledger Nano S:* https://amzn.to/2VAhMvM → USB Hub with switches:* https://amzn.to/2SJuaYv → any STM32 Nucleo-64 development board:* https://amzn.to/2VDDE9J -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #ReverseEngineering #HardwareSecurity

V6ZySLopflk | 25 Jan 2019
We are using IDA to setup segments for the ARM hardware and then find the entry-point through static and dynamic analysis. GPIO: https://web.archive.org/web/20160613024918/http://hertaville.com/2012/07/28/stm32f0-gpio-tutorial-part-1/ research: https://wallet.fail DISCLAIMER: The security research shown here was done a while ago and since then the software and hardware was updated; These videos are not sponsored or endorsed by Ledger. -=[ 💻 Related Products ]=- → Ledger Nano S:* https://amzn.to/2VAhMvM → USB Hub with switches:* https://amzn.to/2SJuaYv → any STM32 Nucleo-64 development board:* https://amzn.to/2VDDE9J -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #ReverseEngineering #HardwareSecurity
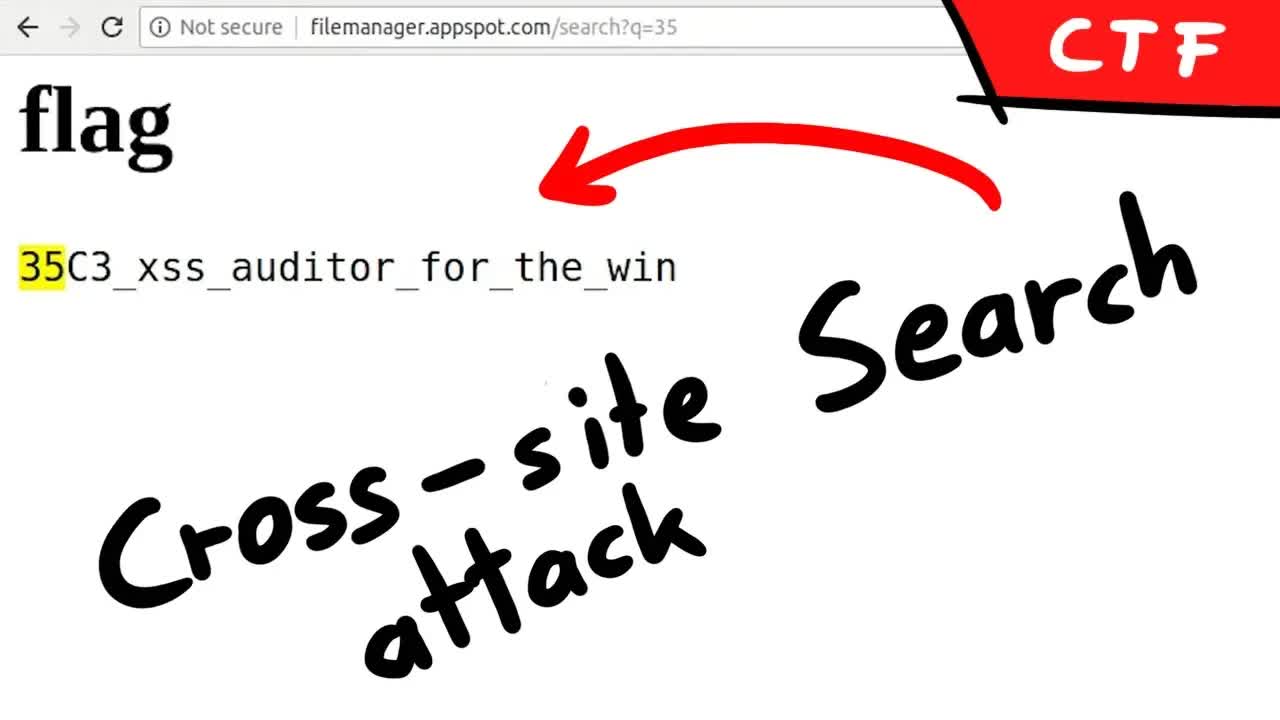
HcrQy0C-hEA | 21 Jan 2019
Intranet Portscanning: https://portswigger.net/blog/exposing-intranets-with-reliable-browser-based-port-scanning Making-of: https://www.youtube.com/watch?v=VI5OLNHf_Sc -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

VI5OLNHf_Sc | 21 Jan 2019
This is how long it takes to create a CTF video-writeup episode. I expect nobody to watch it :D but I hope to achieve two things: 1. If you ever thought about creating videos, here are is an actual practical look at how I do it 2. You see how long it takes to make videos on YouTube - plz be nice to your YT creators :3 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

EpA25bCHHtk | 18 Jan 2019
Using ARM SWD with a development board to debug the chip with GDB. research: https://wallet.fail DISCLAIMER: The security research shown here was done a while ago and since then the software and hardware was updated; These videos are not sponsored or endorsed by Ledger. -=[ 💻 Related Products ]=- → Ledger Nano S:* https://amzn.to/2VAhMvM → USB Hub with switches:* https://amzn.to/2SJuaYv → any STM32 Nucleo-64 development board:* https://amzn.to/2VDDE9J -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #HardwareSecurity #ReverseEngineering

KGmyDiLrqSo | 11 Jan 2019
We start the research by looking at the chips, documentations and manuals. research: https://wallet.fail DISCLAIMER: The security research shown here was done a while ago and since then the software and hardware was updated; These videos are not sponsored or endorsed by Ledger. ST: https://www.st.com/en/microcontrollers/stm32f042k6.html STM32F04 Datasheet: https://www.st.com/resource/en/datasheet/stm32f042k6.pdf -=[ 💻 Related Products ]=- → Ledger Nano S:* https://amzn.to/2VAhMvM → USB Hub with switches:* https://amzn.to/2SJuaYv → any STM32 Nucleo-64 development board:* https://amzn.to/2VDDE9J -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #HardwareSecurity

zXR96jprNcY | 07 Jan 2019
Would you kindly? Patreon: https://www.patreon.com/join/LiveOverflow YouTube Membership: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #LiveOverflow

MoGzPQhwW9s | 04 Jan 2019
Why should we write our private key on a paper if the hardware wallet is so perfect? research: https://wallet.fail DISCLAIMER: These videos are not sponsored by Ledger. The security research shown here was done a while ago and since then the software and hardware was updated. -=[ 💻 Related Products ]=- → Ledger Nano S:* https://amzn.to/2VAhMvM → USB Hub with switches:* https://amzn.to/2SJuaYv → any STM32 Nucleo-64 development board:* https://amzn.to/2VDDE9J → Trezor:* https://amzn.to/2FjJaZ7 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #EmbeddedHardware #SecurityResearch

M0D999KcyHo | 01 Jan 2019
Come and build an unrealistic hacker simulator for Gynvael's Winter GameDev Challenge 2018/19 Rules & FAQ & Constraints: https://gynvael.coldwind.pl/?lang=en&id=697 Gynvael's Channel: https://www.youtube.com/channel/UCCkVMojdBWS-JtH7TliWkVg -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #GameDevChallenge

nNBktKw9Is4 | 28 Dec 2018
It was found that the Ledger Nano S bootloader can be tricked into flashing and executing untrusted firmware. Research Site: https://wallet.fail/ Twitter: https://twitter.com/walletfail Thomas Roth: https://twitter.com/stacksmashing original wallet.fail talk: https://www.youtube.com/watch?v=Y1OBIGslgGM The bootloader is used to update the firmware of the 'non-secure' processor in the Ledger Nano S and has full control over the display, USB and the buttons. Time might tell how critical this issue actually is, a strong proof-of-concept still requires a lot of work and maybe the guys from wallet.fail will publish more in the future. Or join the security research and play around with it yourself! -=[ 💻 Related Products ]=- → Ledger Nano S:* https://amzn.to/2VAhMvM → USB Hub with switches:* https://amzn.to/2SJuaYv → any STM32 Nucleo-64 development board:* https://amzn.to/2VDDE9J → Trezor:* https://amzn.to/2FjJaZ7 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #HardwareSecurity #SecurityResearch

RfL3FcnVbJg | 25 Dec 2018
In part 2 we identify a backdoor and find the gadgets to do JOP in a ethereum smart contract. Challenge Files + Solution: https://gist.github.com/LiveOverflow/21c8a505ca176e5bb20bc94eb23acdf1 Remix: http://remix.ethereum.org EVM Opcodes: https://github.com/trailofbits/evm-opcodes Ethereum plugin for Binary Ninja: https://github.com/trailofbits/ethersplay -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #SmartContract

ozqOlUVKL1s | 21 Dec 2018
I thought I know ethereum smart contract security, but this challenge punched me in the face. This was crazy. In the first episode I introduce the challenge and talk about various ideas I had. part 2: https://www.youtube.com/watch?v=RfL3FcnVbJg Challenge Files + Solution: https://gist.github.com/LiveOverflow/21c8a505ca176e5bb20bc94eb23acdf1 Remix: http://remix.ethereum.org EVM Opcodes: https://github.com/trailofbits/evm-opcodes Ethereum plugin for Binary Ninja: https://github.com/trailofbits/ethersplay -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #SmartContract

2S_TXaGYD8E | 14 Dec 2018
Hacking Competition in China. Our team qualified for the Real World CTF finals in China organised by Chaitin Tech, which was a really awesome CTF. In this video I want to share my experience and thoughts about the event. Official Video: https://www.youtube.com/watch?v=cYVoJWNVngE Real World CTF: https://realworldctf.com/ -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CVE #CTF

0i7wOfyJsW8 | 07 Dec 2018
Calypso Chip: https://osmocom.org/projects/baseband/wiki/HardwareCalypso -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #MobileSecurity

L3PPWVPg2WI | 30 Nov 2018
A video about the discovery of the BootROM bug, based on the talk given by Andy "Glitching The Switch". We talk about how the Switch boots, how the hardware coould be attacked, how a vulnerability in the switch was found and what exactly it does. Glitching The Switch Talk: https://media.ccc.de/v/c4.openchaos.2018.06.glitching-the-switch Andy: https://twitter.com/G33KatWork -=[ 💻 Related Products ]=- → Nintendo Switch:* https://amzn.to/2SESPO0 → NVidia Jetson TX1:* https://amzn.to/2C6uw4m -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CVE #ReverseEngineering

DM1tPmxGY7Y | 23 Nov 2018
A recent paper about ProtonMail's E2EE makes us wonder if the technology simply doesn't allow us to implement such solutions. An Analysis of the ProtonMail Cryptographic Architecture - Nadim Kobeissi https://eprint.iacr.org/2018/1121 ProtonMail response: https://www.reddit.com/r/ProtonMail/comments/9yqxkh/an_analysis_of_the_protonmail_cryptographic/ea3g0hm/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #Cryptography

eQFbG6CwwdI | 16 Nov 2018
How to get good at XSS? There are a lot of charlatans out their overhyping by posting misleading content. It's infuriating because a lot of the actual research is less flashy and thus more hidden. Maybe I'm a bit too pessemistic in this video, but I think it's a concrete example we can use talk about it. XSS Introduction: https://www.youtube.com/watch?v=8GwVBpTgR2c&index=4&list=PLhixgUqwRTjx2BmNF5-GddyqZcizwLLGP uXSS in Safari: https://www.youtube.com/watch?v=0uejy9aCNbI Cross-Origin Stylesheets: https://www.youtube.com/watch?v=bMPAXsgWNAc Gareth Heyes: https://twitter.com/garethheyes -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. https://amzn.to/2SESPO0 switch jetson TX1 https://amzn.to/2C6uw4m

UeAKTjx_eKA | 09 Nov 2018
A reddit user finds raspberry pi zeros hidden behind trash cans, vending machines and other places in the college library. We reverse engineer them and determine if they are malicious. DirtyCOW video including "files" in Linux: https://www.youtube.com/watch?v=kEsshExn7aE -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #ReverseEngineering

x-TT3z8ouhQ | 02 Nov 2018
In this video we look at another FLARE-On 2018 challenge. This one is weird as we have to somehow automate the analysis of a big collection of binaries. We also learn something about embedded resources. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #ReverseEngineering #CTF

B41GbyB7H5U | 26 Oct 2018
This challenge was part of the FLARE-On 2018 CTF. In this video we reverse engineer a basic windows .exe to find out how to win the game. At first we tried to attack the weak crypto but failed. At the end it turns out I had a bug in my code :( Flare-On: https://www.flare-on.com/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #ReverseEngineering #CTF

0uejy9aCNbI | 19 Oct 2018
URLs are surprisingly hard to read. Chrome Bug: https://bugs.chromium.org/p/chromium/issues/detail?id=841105 Orange Tsai: https://twitter.com/orange_8361 A New Era of SSRF - Exploiting URL Parser in Trending Programming Languages! - CODE BLUE: https://www.youtube.com/watch?v=2MslLrPinm0 Slides: https://www.blackhat.com/docs/us-17/thursday/us-17-Tsai-A-New-Era-Of-SSRF-Exploiting-URL-Parser-In-Trending-Programming-Languages.pdf -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CVE #SecurityResearch

IuxBfHnP5S0 | 12 Oct 2018
Let's start with the GSM network. We can use the Nokia Network Monitor to learn about channels and frequencies. Nokia Network Monitor: https://en.wikipedia.org/wiki/Nokia_network_monitor Vadim Yanitskiy: https://twitter.com/axilirator Basestation Map: https://www.cellmapper.net/map -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #MobileSecurity

iJFnYBJJiuQ | 05 Oct 2018
In this video we use SIMtrace to intercept the communication between the phone and SIM card to understand how that works. This is part 1 in a series introducing mobile security. Vadim Yanitskiy: https://twitter.com/axilirator Osmocom: https://osmocom.org/ -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #MobileSecurity

bMPAXsgWNAc | 28 Sep 2018
In 2017 a cool bug was reported by a researcher, which lead me down a rabbit hole to a 2014 and even 2009 bug. This provides interesting insight into how web security research looks like. cgvwzq's Bug (2017): https://bugs.chromium.org/p/chromium/issues/detail?id=788936 filedescriptor's Bug (2014): https://bugs.chromium.org/p/chromium/issues/detail?id=419383 scarybeasts' Bug (2009): https://bugs.chromium.org/p/chromium/issues/detail?id=9877 GynvaelEN: https://www.youtube.com/user/GynvaelEN Efail Stream: https://www.youtube.com/watch?v=VC_ItSQaUx4 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #SecurityResearch

RXgp4cDbiq4 | 21 Sep 2018
Vlog about the Attack and Defense DEF CON 2018 CTF Finals in Las Vegas. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #DefCon #CTF

B8saYocsI-U | 14 Sep 2018
Vlog about my first time in Las Vegas to participate in the DEF CON CTF Finals. In this first part I just share my experience at the various conferences and events. And in the next part I will talk about the DEF CON CTF itself. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #DefCon #BlackHat

6htg9MGMOYE | 07 Sep 2018
Part 20: The End. Original Credits video: https://youtu.be/X3fubzKSMCE 🌴 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #PwnAdventure #GameHacking

2pqHsW3yNlA | 04 Sep 2018
Part 19: I implemented the KeyGen in JavaScript based on the algorithms we reversed from the assembler code. The used the dlc unlock code to solve the last challenge - Pirate's Treasure. Keygen: http://old.liveoverflow.com/poc/keygen.html 🌴 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #PwnAdventure

dcR1dkZJ7iU | 31 Aug 2018
Part 18: We are looking at how RSA is implemented in assembler for arbitrary large integers. Specifically modular exponentiation. 🌴 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #PwnAdventure #ReverseEngineering

WgRAYOXBVxs | 24 Aug 2018
Part 17: This video might be a bit more boring reversing, and I even failed to recognise the implemented algorithm. 🌴 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #PwnAdventure #ReverseEngineering
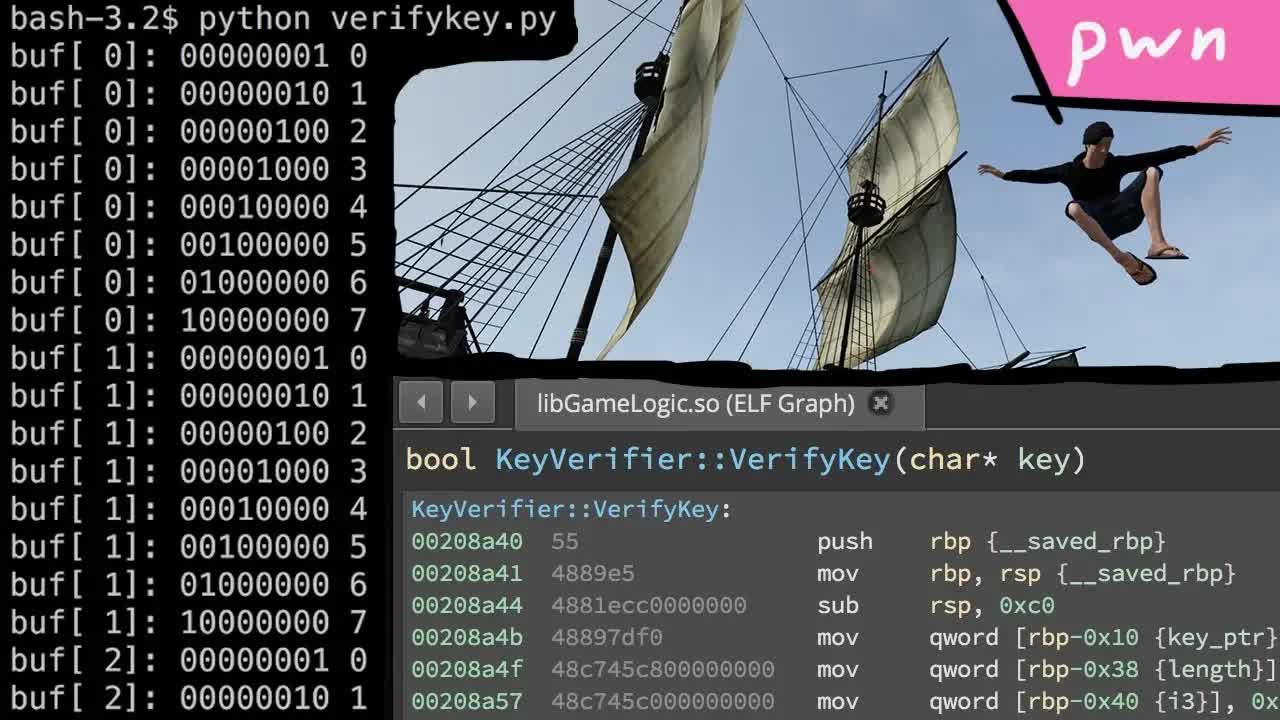
JDXU2shkNSE | 17 Aug 2018
Part 16: We reverse engineer more of the VerifyKey function and find a custom Base32 encoding. 🌴 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #PwnAdventure #ReverseEngineering

8ieAh19vrYc | 11 Aug 2018
Part 15: We start reversing VerifyKey for the "Pirate's Treasure" challenge. This will take us several videos. In this first part we look at the input validation. 🌴 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #PwnAdventure #ReverseEngineering

L8sH8VM2Bd0 | 03 Aug 2018
Part 14: Totally failed at building a neural network or using other machine learning algorithms and in the end just used bruteforce. Blocky's Revenge part 1: https://www.youtube.com/watch?v=PQPO5Z4lVTU 🌴 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG training_data: https://raw.githubusercontent.com/LiveOverflow/PwnAdventure3/master/tools/blocky/training_data to win these output bits have to be 0: [119,96,14,123,128,140,136,148,145,158,154,167,163,160,173] -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #PwnAdventure

PQPO5Z4lVTU | 27 Jul 2018
Part 13: We start looking into another challenge, Blocky's Revenge. I failed to reverse engineer this in the client, but had some success with the network packets. 🌴 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG training_data: https://raw.githubusercontent.com/LiveOverflow/PwnAdventure3/master/tools/blocky/training_data to win these output bits have to be 0: [119,96,14,123,128,140,136,148,145,158,154,167,163,160,173] -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #PwnAdventure

XrE-RfAYrzs | 20 Jul 2018
Part 12: Killing the boss Magmarok in the Fire & Ice Dungeon with an integer overflow. Bonus Video Part 12.2: https://www.youtube.com/watch?v=9NYleo0r4Eg 🌴 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #PwnAdventure #CTF

9NYleo0r4Eg | 20 Jul 2018
Part 12.2: Binary data can be interpreted in different ways. This is a bonus video along the integer overflow we exploit to provide a bit more context. Main Video: https://www.youtube.com/watch?v=XrE-RfAYrzs 🌴 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #PwnAdventure #CTF

_ePSezu33vw | 13 Jul 2018
Part 11: We reverse engineer more network packets and then also add functionality to inject packets. With that we build a remote autoloot for easy farming. 🌴 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG GitHub: https://github.com/LiveOverflow/PwnAdventure3/blob/master/tools/proxy/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #PwnAdventure

TG_FVzBijrk | 06 Jul 2018
Part 10: With our TCP Proxy we can now parse the packets and analyse the protocol. Parser on GitHub: https://github.com/LiveOverflow/PwnAdventure3/blob/master/tools/proxy/parser_part10.py 🌴 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #PwnAdventure #CTF

J2XS3m2Ctuc | 29 Jun 2018
I got some stuff very wrong, so I really felt like making a proper update video to explain it. main video: https://www.youtube.com/watch?v=8yWUaqEcXr4 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF

8yWUaqEcXr4 | 28 Jun 2018
Solving a crackme implemented in JavaScript that attempts to obfuscate the algorithm through some anti-debugging. Solution Script / HTML: https://gist.github.com/LiveOverflow/bbdffe3777ce0f008b452e0a789cef65 John Hammond: https://www.youtube.com/user/RootOfTheNull -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF

iApNzWZG-10 | 22 Jun 2018
Part 9: To analyse the game traffic, we are developing a simple proof of concept TCP network proxy. Then we can start to reverse engineer the protocol. GitHub: https://github.com/LiveOverflow/PwnAdventure3/tree/master/tools/proxy 🌴 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #PwnAdventure #NetworkSecurity #CTF

it5kqkE-KAo | 15 Jun 2018
Part 8: We are combining what we learned to find the hidden Golden Eggs. But the last egg has a little twist to it, so we had to reverse engineer a bit more. GitHub: https://github.com/LiveOverflow/PwnAdventure3 File LD_PRELOAD: https://github.com/LiveOverflow/PwnAdventure3/blob/master/tools/linux/part8_eggs.cpp 🌴 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #PwnAdventure #CTF #ReverseEngineering

Ry_yb5Oipq0 | 10 Jun 2018
What is going on with .zip files. What is this new critical vulnerability that seems to affect everything? ... old is new again. Resources: - ZipperDown: https://zipperdown.org/ - Zip Slip: https://snyk.io/research/zip-slip-vulnerability - Zip Specification: https://pkware.cachefly.net/webdocs/casestudies/APPNOTE.TXT - The Complete Guide to Hacking WWIV: http://phrack.org/issues/34/5.html#article - Go library Fix Bypass: https://github.com/mholt/archiver/pull/65#issuecomment-395988244 Gynvael: - Hacking Livestream #53: The ZIP file format https://www.youtube.com/watch?v=X7j2sisMKzk - Ten thousand security pitfalls: the ZIP file format http://gynvael.coldwind.pl/?id=682 - GynvaelEN Channel: https://www.youtube.com/GynvaelEN - Twitter: https://twitter.com/gynvael Ange Albertini / Corkami - Funky Fileformats Talk: https://www.youtube.com/watch?v=hdCs6bPM4is - Funky Fileformats Slides: https://events.ccc.de/congress/2014/Fahrplan/system/attachments/2562/original/Funky_File_Formats.pdf - Twitter: https://twitter.com/angealbertini / https://twitter.com/corkami -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CVE #SecurityResearch

E7e_-sqOo1M | 08 Jun 2018
Part 7: We use chat messages to implement teleport commands and try to get access to more chests. But it's not that easy and we have to implement hovering. GitHub Teleport: https://github.com/LiveOverflow/PwnAdventure3/blob/master/tools/linux/part7_teleport.cpp 🌴 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #PwnAdventure #CTF #ReverseEngineering

VzZi2AGAsOY | 01 Jun 2018
Part 6: We continue with our LD_PRELOAD method and implement flying. We also discover our first secret where we get our first flag! Challenge: Until the Cows Come Home 🌴 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG GitHub: https://github.com/LiveOverflow/PwnAdventure3 part6_flying.cpp: https://github.com/LiveOverflow/PwnAdventure3/blob/master/tools/linux/part6_flying.cpp -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #PwnAdventure

W7MC05_JN68 | 25 May 2018
Part 5: Finally our first hack! We use the LD_PRELOAD feature to overwrite functions of the dynamic library libGameLogic.so. This allows us to change a lot of behaviour in the client. GitHub: https://github.com/LiveOverflow/PwnAdventure3/tree/master/tools/linux/part5_walking_speed.cpp 🌴 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #PwnAdventure #CTF #ReverseEngineering

8wz2CM0483o | 18 May 2018
Part 4: We start reverse engineering! Luckily the game comes with not-stripped binaries which means all the class names are included. We can use the debug information to dump class definitions with gdb. This will be incredible useful when we create our first hack next video! libGameLogic.h: https://github.com/LiveOverflow/PwnAdventure3/blob/master/tools/linux/libGameLogic.h 🌴 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #PwnAdventure #ReverseEngineering

pzM4o6qxssk | 11 May 2018
Part 3: We start to get technical by gathering some information. This is a crucial step in order to get a better understanding about the game in order to hack it. find_unique.py: https://github.com/LiveOverflow/PwnAdventure3/blob/master/tools/find_unique.py 🌴 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #PwnAdventure #CTF #NetworkSecurity

VkXZXwQP5FM | 04 May 2018
Part 2: Before we can start with the hacks we have to setup a private server. I used this project to learn more about Docker myself and share my result so you can set it up easily. Setup Server Instructions: https://github.com/LiveOverflow/PwnAdventure3 DigitalOcean referral link: https://m.do.co/c/826f195e2288 🌴 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #PwnAdventure

RDZnlcnmPUA | 27 Apr 2018
Part 1: Pwn Adventure 3 is a game with CTF challenges - it was created to be hacked. This is the first part of a longer series where we will have a look at all challenges from the game and just have fun hacking it. Game Download: http://www.pwnadventure.com/ Server Setup: https://github.com/LiveOverflow/PwnAdventure3 🌴 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjzzBeFSHXrw9DnQtssdAwgG -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #PwnAdventure
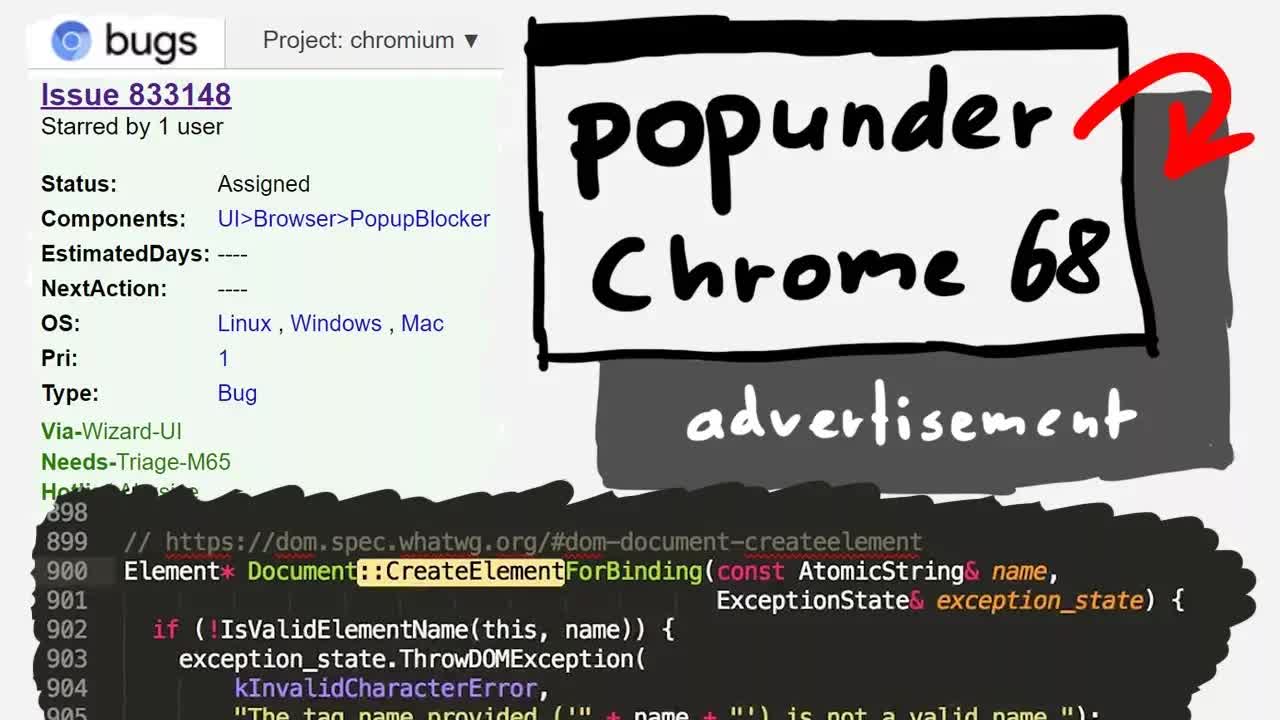
y6Uzinz3DRU | 20 Apr 2018
I wanted to compile a custom Chromium 68 build to totally ignore the obfuscated JavaScript. That was a cool experience, but in the end not necessary - the trick was super simple and works on Mac, Windows and Linux. Chromium Issue 833148: https://bugs.chromium.org/p/chromium/issues/detail?id=833148 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #ReverseEngineering

ZaOtY4i5w_U | 13 Apr 2018
A very basic concept of security code audits is the sources/sinks. Everybody develops an intuition for it, but I still wanted to talk about it, because it would have helped me when I started out. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

2TofunAI6fU | 06 Apr 2018
totally clickbait. but also not clickbait. I don't know where to start hacking, there is no guide to learn this stuff. But I hope you still have a plan now! How to learn hacking - https://www.youtube.com/watch?v=iKXd9zW1OuI The ultimate guide, everything you need to know - https://google.com Stuff that looks cool: crypto challenges - https://cryptopals.com/ wargames - https://overthewire.org other exploit challenges - http://pwnable.kr/ basics of exploitation (+ my playlists) - https://exploit-exercises.com/protostar/ math puzzles with programming - https://projecteuler.net break ethereum smart contracts - https://ethernaut.zeppelin.solutions/ Try something new: create an android app - https://developer.android.com/training/basics/firstapp/index.html create a website with python - http://flask.pocoo.org/ do some nice animations - https://processing.org/tutorials/ make some LEDs blink - https://www.arduino.cc/en/Guide/HomePage Other Channels: GynvaelEN - https://www.youtube.com/channel/UCCkVMojdBWS-JtH7TliWkVg MurmusCTF - https://www.youtube.com/channel/UCUB9vOGEUpw7IKJRoR4PK-A MalwareAnalysisForHedgehogs - https://www.youtube.com/channel/UCVFXrUwuWxNlm6UNZtBLJ-A hasherezade - https://www.youtube.com/channel/UCNWVswPNgn5kutPNa5sprkg IppSec - https://www.youtube.com/channel/UCa6eh7gCkpPo5XXUDfygQQA John Hammond - https://www.youtube.com/user/RootOfTheNull -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

ujaBCDaPUm0 | 31 Mar 2018
This is the best trick to get started with pen-testing! A day in the life of a pen-tester: https://www.youtube.com/watch?v=2LOtBpA7W_M -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

Jpaq0QkepgA | 30 Mar 2018
In order to understand complex systems quickly, you need to identify reoccurring patterns in order to focus on important parts. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

kMu1J8QdxE8 | 23 Mar 2018
Radamsa is a test case generator for robustness testing, a.k.a. a fuzzer. And it does it super well. Perfect for rapid prototyping. radamsa: https://github.com/aoh/radamsa -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

EOlddNofKxo | 16 Mar 2018
In this video we only focus on the mathematical solution for software_update from the 34c3 CTF. sage script: https://gist.github.com/LiveOverflow/104adacc8af7895a4c14cea4a5236ecc -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #Cryptography

Vgdhlh6evjI | 09 Mar 2018
This challenge from the 34C3 CTF implemented a software update in python. In part 1/2 we try to understand the code and think about possible attacks. software_update: https://archive.aachen.ccc.de/34c3ctf.ccc.ac/challenges/index.html What is CTF? https://www.youtube.com/watch?v=8ev9ZX9J45A Why you should play CTFs: https://www.youtube.com/watch?v=rfjV8XukxO8 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #Cryptography #CTF

lE6ke7pqCNY | 02 Mar 2018
Two years ago I failed to solve the readme challenge at the 32c3ctf. Since then I have learned a lot and I got another chance! readme 32c3ctf: https://www.youtube.com/watch?v=wLsckMfScOg readme_revenge: https://archive.aachen.ccc.de/34c3ctf.ccc.ac/challenges/index.html What is CTF? https://www.youtube.com/watch?v=8ev9ZX9J45A Why you should play CTFs: https://www.youtube.com/watch?v=rfjV8XukxO8 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #BinaryExploitation

oJ6t7AImTdE | 23 Feb 2018
This is "well known" research that resurfaces every other year. Let me tell you a story how I have heard about this in 2012 and putting it into perspective. Research "Scriptless Attacks – Stealing the Pie Without Touching the Sill" (2012): + Paper: https://www.nds.rub.de/media/emma/veroeffentlichungen/2012/08/16/scriptlessAttacks-ccs2012.pdf + Slides: https://www.slideshare.net/x00mario/stealing-the-pie + Talk recording: https://channel9.msdn.com/Events/Blue-Hat-Security-Briefings/BlueHat-Security-Briefings-Fall-2012-Sessions/BH1203 CSS Keylogger: https://github.com/maxchehab/CSS-Keylogging Stealing Data With CSS - Attack and Defense: https://www.mike-gualtieri.com/posts/stealing-data-with-css-attack-and-defense Twitter: + https://twitter.com/0x6D6172696F + https://twitter.com/sirdarckcat + https://twitter.com/garethheyes + https://twitter.com/thornmaker + https://twitter.com/mlgualtieri -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #SecurityResearch

AMMOErxtahk | 16 Feb 2018
This is what my brain tells me a lot. But sometimes we just need a break. And it's OK to take a break - however long it has to be. And in this video I'm sharing how I try to deal with these negative thoughts and lack of motivation. -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

aRDGI7UVSuI | 10 Feb 2018
In this part I'm thinking about the effects of bots on MMORPGs and then look at the collected data. The Data: https://imgur.com/a/X8Syu Part 1: https://www.youtube.com/watch?v=irhcfHBkfe0 Play Guild Wars 2: https://www.guildwars2.com/register -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.
irhcfHBkfe0 | 09 Feb 2018
A friend told me that a GW2 trading bot implemented a dumb API. We are going to find and use it to track the bot. Play Guild Wars 2: https://account.arena.net/register Fiddler: https://www.telerik.com/fiddler .NET Reflector: https://www.red-gate.com/products/dotnet-development/reflector/ HxD: https://mh-nexus.de/en/hxd/ IDA Free: https://www.hex-rays.com/products/ida/support/download_freeware.shtml Windows VM: https://developer.microsoft.com/en-us/microsoft-edge/tools/vms/ -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #ReverseEngineering
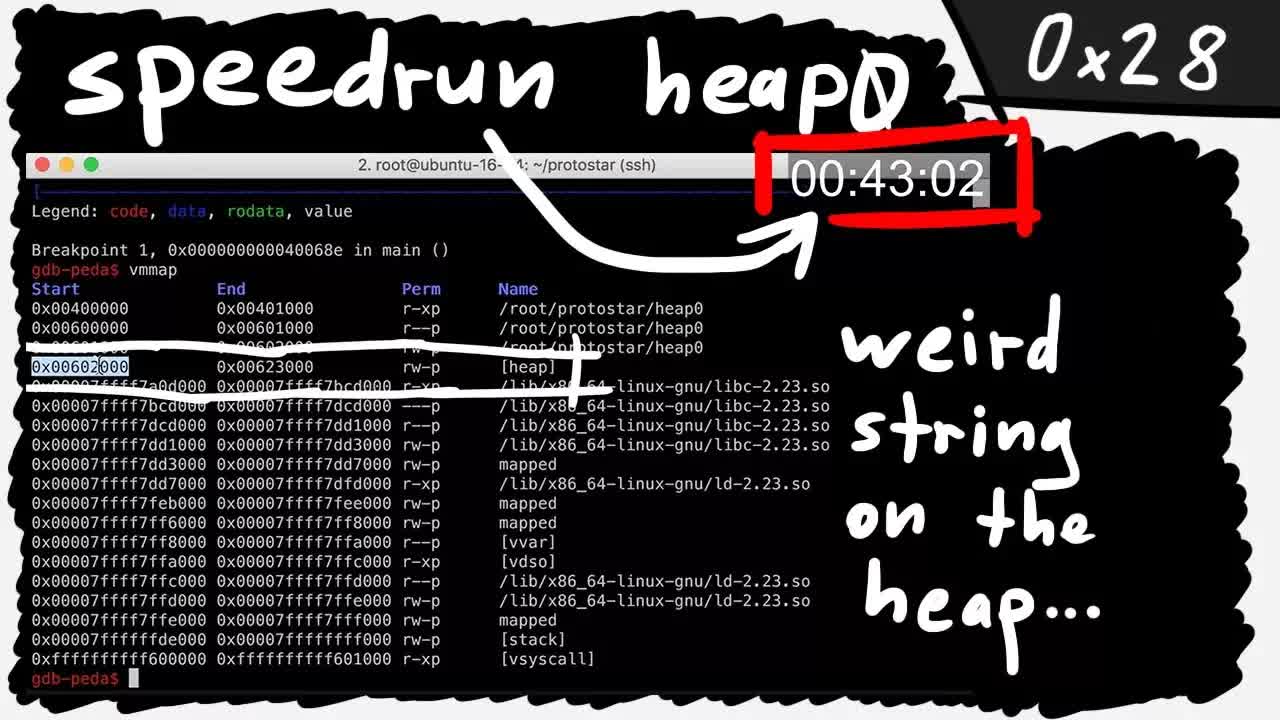
fJMnH0kCAak | 02 Feb 2018
The heap0 example is not affected by DEP or ASLR on Ubuntu 16.04, so it's super easy. But we use the opportunity to investigate another weird string that we found on the heap. heap0: http://liveoverflow.com/binary_hacking/protostar/heap0.html -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BinaryExploitation

MpeaSNERwQA | 26 Jan 2018
This short php code contains a critical vulnerability. In this video I will explain in detail what I think while analysing it. Original source of challenge: https://www.securify.nl/en/blog/SFY20180101/spot-the-bug-challenge-2018-warm-up.html Link to tweet: https://twitter.com/xxByte/status/951499972582703104 -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CodeAudit #WebSecurity

gKHaKoPJN08 | 19 Jan 2018
An interview with BadgeWizard showing off the TROOPERS 17 Badge with a Nokia 3310. https://www.troopers.de/ https://twitter.com/BadgeWizard -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

hyoPAOTrUMc | 12 Jan 2018
Part 1 of reverse engineering another AVR firmware. Zeta Two shows us how to get started with reversing the code for the ATmega328P (AVR) chip. This was a challenge from the rhme2 competition. In this video we identify some I/O functions and the main() function. rhme2: https://rhme.riscure.com/2/challenges Zeta Two: https://twitter.com/zetatwo -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #ReverseEngineering #CTF #EmbeddedHardware
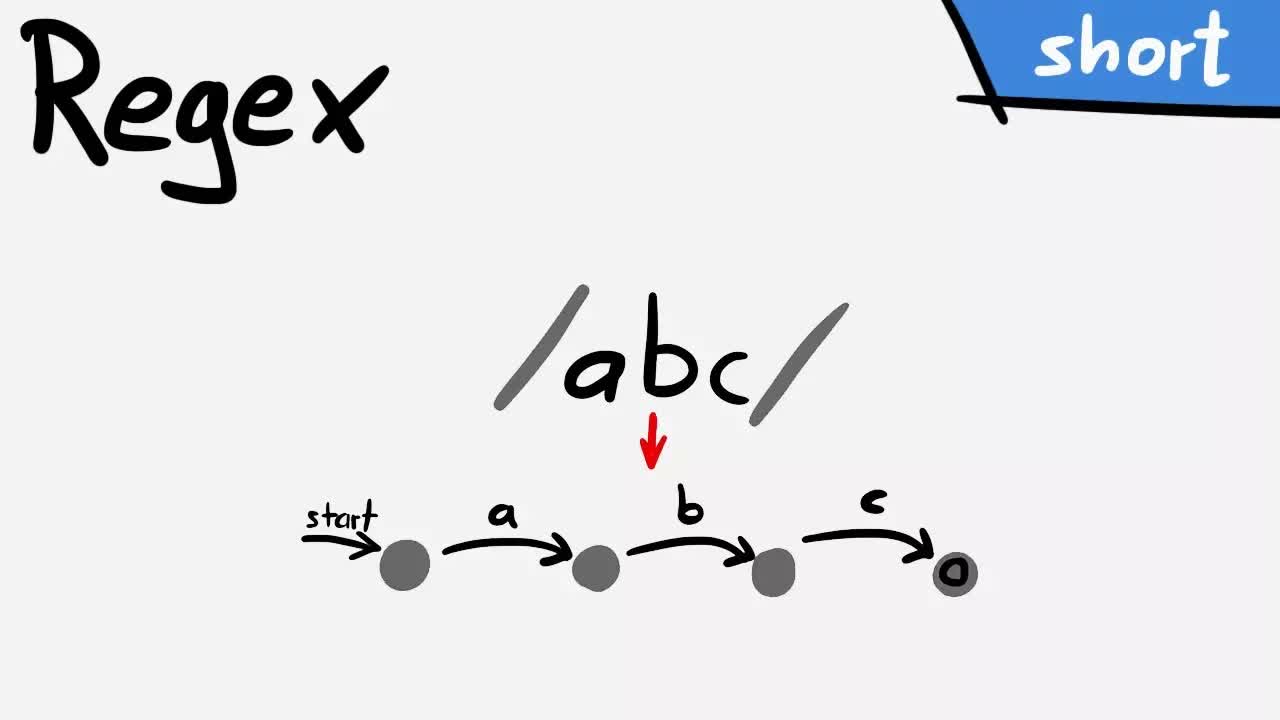
hprXxJHQVfQ | 05 Jan 2018
A short introduction to regular expressions and how you can visualise them. It's very helpful when auditing input validation. Debuggex: https://www.debuggex.com Solving Pokemon Blue With a Single Regex? https://www.youtube.com/watch?v=Q2g9d29UIzk -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

zoyK33-IcD4 | 29 Dec 2017
We only had a phone and solved challenges with online tools before the teams did it. Solved with Online OCR and WebArchive Troopers Students: https://www.troopers.de/students/ Troopers: https://www.troopers.de/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF

Xml4Gx3huag | 22 Dec 2017
People leak stuff on github all the time. ssh private keys, national ID scans, ... Maybe we can find some Bitcoin private keys and get rich!? Google BigQuery: https://cloud.google.com/bigquery/ GitHub BigQuery Dataset: https://cloud.google.com/bigquery/public-data/github -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #SecurityResearch

_lO_rwaK_pY | 15 Dec 2017
In this video we build an exploit for format4 on a modern Ubuntu. This means that we have to adapt it to 64bit. format4: http://liveoverflow.com/binary_hacking/protostar/format4.html previous episode: https://www.youtube.com/watch?v=t1LH9D5cuK4 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BinaryExploitation #FormatString

PNuAzR_ZCbo | 08 Dec 2017
Is lack of certificate pinning a severe vulnerability? Is this just fearmongering done for fame? Or is it a valid security issue? In this video I lay out my opinion about it and I'm looking for your input. link to reddit thread: https://www.reddit.com/r/LiveOverflow/comments/7ijj3g/some_thoughts_on_mobile_app_security_is_it_fud/ https://media.ccc.de/v/33c3-7969-shut_up_and_take_my_money https://www1.cs.fau.de/content/n26 https://www1.cs.fau.de/nomorp http://www.sueddeutsche.de/digital/exklusiv-online-banking-apps-sind-anfaellig-fuer-hacker-1.3762624 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #SecurityResearch #MobileSecurity

Kc6_PpdbcCw | 01 Dec 2017
This level turns out to be fairly easy when compiled on a modern Ubuntu. Finally :D format2: https://exploit-exercises.com/protostar/format2/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BinaryExploitation #FormatString

FJwlOUfvRKg | 27 Nov 2017
Survey: https://goo.gl/forms/zNV4Cr8EjeLJIGgq1 -------------------------------------- Twitter: https://twitter.com/LiveOverflow Website: http://liveoverflow.com/ Subreddit: https://www.reddit.com/r/LiveOverflow/ Facebook: https://www.facebook.com/LiveOverflow/

AahpiYxKR2c | 24 Nov 2017
Last week I thought this level couldn't be exploited. It turns out there is a way! wcbowling's comment: https://www.reddit.com/r/LiveOverflow/comments/7dmrx8/playing_around_with_a_format_string_vulnerability/dq02kos/ asciinema: https://asciinema.org/a/148133 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BinaryExploitation #FormatString

CyazDp-Kkr0 | 17 Nov 2017
This is about format0 from https://exploit-exercises.com/protostar/ compiled on a modern Ubuntu system. format0: http://liveoverflow.com/binary_hacking/protostar/format0.html DigitalOcean referral*: https://m.do.co/c/826f195e2288 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BinaryExploitation #FormatString

hRei9xXRAGE | 10 Nov 2017
Paul shows us another exploit for FFmpeg. The vulnerability is located in the RTMP protocol. While working with the binary format of the protocol requires a lot of work, the exploit itself is very easy. Vulnerable Version: https://github.com/FFmpeg/FFmpeg/tree/d903b4e3ad4a81b3dd79f12c2f3b9cb16e511173 Paul on Twitter: https://twitter.com/__paulch LiveOverflow Podcast: http://liveoverflow.libsyn.com/ Original Email: http://www.openwall.com/lists/oss-security/2017/02/02/1 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #SecurityResearch #BinaryExploitation #HeapOverflow #CVE

Lpt7WIqXOgM | 04 Nov 2017
Deeper look at CVE-2016-10190. A Heap overflow caused by a negative HTTP chunksize. Vulnerable Version: https://github.com/FFmpeg/FFmpeg/tree/d903b4e3ad4a81b3dd79f12c2f3b9cb16e511173 Paul on Twitter: https://twitter.com/__paulch LiveOverflow Podcast: http://liveoverflow.libsyn.com/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #SecurityResearch #HeapOverflow #CVE #BinaryExploitation

drPyKgt1MMg | 27 Oct 2017
This is the first part of exploiting ffmpeg. A huge thank you to Paul Cher for the excellent work on recording the process and sharing his research. I merely edited it together. Vulnerable Version: https://github.com/FFmpeg/FFmpeg/tree/d903b4e3ad4a81b3dd79f12c2f3b9cb16e511173 Paul on Twitter: https://twitter.com/__paulch LiveOverflow Podcast: http://liveoverflow.libsyn.com/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CVE #HeapOverflow #BinaryExploitation

rfjV8XukxO8 | 20 Oct 2017
Abstract: For many of us hacking means creativity - if you have ever witnessed a complex heap memory corruption exploit, you realise how close this is to art. But when we look at how IT security is taught, we often see uncreative memorisation of dangerous functions or generally a checklist approach. Nobody can understand or know everything in IT Security and isolation of topics only leads to interesting attack ideas being lost at the topic boundaries. Like in math we rather like to develop an intuition and understanding of underlying concepts that help us to adapt to any system we want to hack. Especially because the IT world is changing extremely fast and staying up-to-date is necessary. I believe, for anybody who is interested in IT security, as well as developers who should write secure code, it’s important to train hacking creatively. CTF (Capture The Flag) challenges are kind of like math puzzles for hackers - sometimes they are about exploiting basic issues and sometimes they are very esoteric. But they always require creative thinking. Security trainings, academic education and books will get you far enough to deliver good work, but I believe playing CTFs can make the difference between good or excellent work. With this talk I want to motivate you to play CTFs and showcase various example challenge solutions, to show you stuff you hopefully haven't seen before and get you inspired to find more interesting vulnerabilities. Fsec Conference: https://fsec.foi.hr Recording and Editing by: https://twitter.com/Ministraitor -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF

fOgJswt7nAc | 17 Oct 2017
KRACK: https://www.krackattacks.com Read the paper! https://papers.mathyvanhoef.com/ccs2017.pdf Some interesting discussion about the formal protocol verification: https://blog.cryptographyengineering.com/2017/10/16/falling-through-the-kracks/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #SecurityResearch #WifiHacking

TpdDq56KH1I | 13 Oct 2017
Recently I attended fsec 2017 in croatia. And there was a cool CTF challenge I solved during the conference that I wanted to share. script: https://gist.github.com/LiveOverflow/11bde6352f52be33864f1fd657e7cde1 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF

7KS3XHP35QY | 06 Oct 2017
Solving the AES whitebox crypto challenge without even touching crypto or AES. The tools: https://github.com/SideChannelMarvels Challenge: https://github.com/Riscure/Rhme-2017/tree/master/prequalifications/White%20Box%20Unboxing -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

eecKZIOiRCc | 29 Sep 2017
Exploring some of the notes and thoughts I had analyzing the whitebox crypto challenge. Challenge: https://github.com/Riscure/Rhme-2017/tree/master/prequalifications/White%20Box%20Unboxing -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.
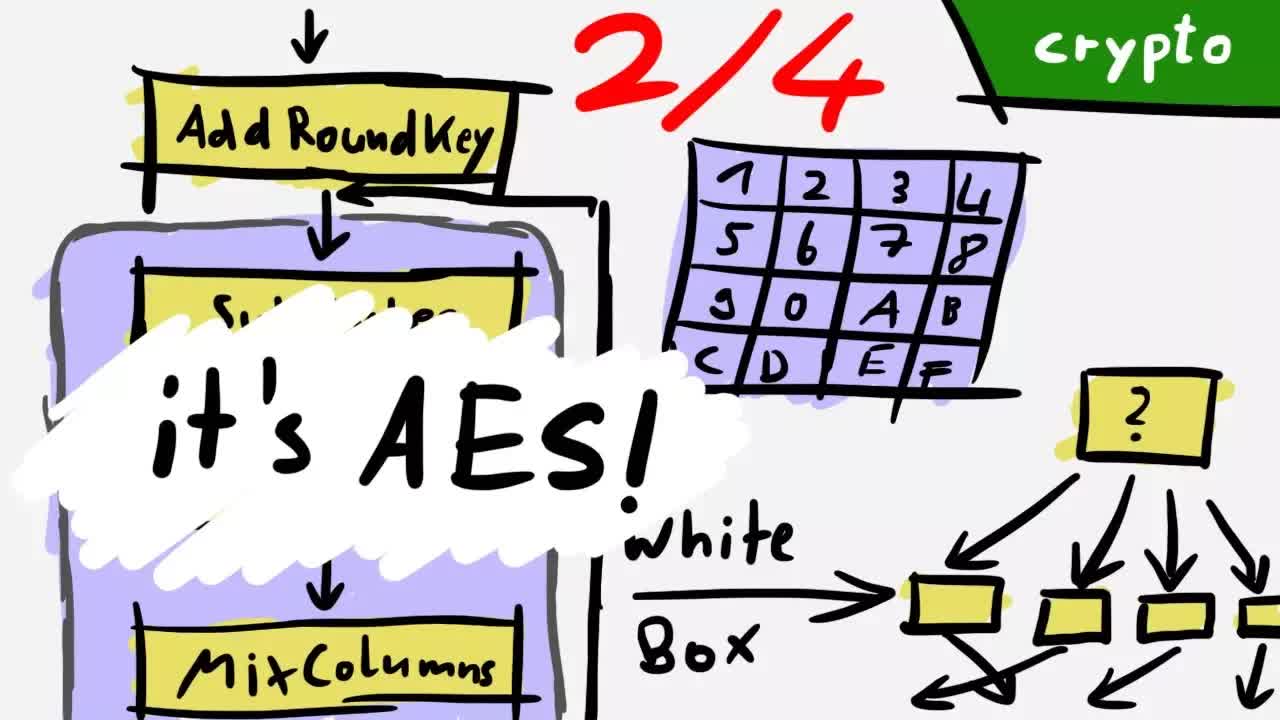
k2MPmbchvaM | 22 Sep 2017
Long story short, we reverse more and more of the binary and with some hints we realize, it's AES afterall. Challenge: https://github.com/Riscure/Rhme-2017/tree/master/prequalifications/White%20Box%20Unboxing -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

84Pp9CBjgd8 | 15 Sep 2017
We start to reverse engineer a crypto binary with Hopper. Challenge: https://github.com/Riscure/Rhme-2017/tree/master/prequalifications/White%20Box%20Unboxing -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.
VcFQeimLH1c | 10 Sep 2017
I hate PopUnder. There is a new one for Chrome 63 on Windows. Let's reverse it to report it to Google. PopUnder Chrome 59: https://www.youtube.com/watch?v=8UqHCrGdxOM PopUnder Chrome 60: https://www.youtube.com/watch?v=PPzRcZLNCPY Music by: ozzed.net -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #ReverseEngineering

0exSe-PAhns | 08 Sep 2017
part 1/2: https://www.youtube.com/watch?v=sJPhsE_XeKI part 2/2: https://www.youtube.com/watch?v=ANIoQXAoyr0 references: https://sourceware.org/glibc/wiki/MallocInternals https://heap-exploitation.dhavalkapil.com/diving_into_glibc_heap/bins_chunks.html -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BinaryExploitation #UseAfterFree

ANIoQXAoyr0 | 08 Sep 2017
Part 2 of solving the exploitation challenge from RHme3. In the last video we found the bug and now we create the exploit. part 1: https://www.youtube.com/watch?v=sJPhsE_XeKI -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BinaryExploitation #UseAfterFree

sJPhsE_XeKI | 01 Sep 2017
Exploitation challenge from the RHme3 qualification round. We use ltrace to understand what the binary does and then use gdbinit to create custom logging. https://github.com/Riscure/Rhme-2017 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BinaryExploitation

11X1c82BzJ4 | 29 Aug 2017
Deadline: probably 10. September 2017 (check my Twitter for announcements) Giveaway amount: 5 Boards Good chances have: + hardware experience (Arduinos, Protocols, ...) + analysing why you failed in the Qualification + create an excellent writeup including what you first missunderstood or where you got stuck (bonus points for awesome videos) + surprise me. I don't know myself what I want + Public posts/videos for others to learn from is always welcome [email protected] -------------------------------------- Twitter: https://twitter.com/LiveOverflow Website: http://liveoverflow.com/ Subreddit: https://www.reddit.com/r/LiveOverflow/ Facebook: https://www.facebook.com/LiveOverflow/
ylfyezRhA5s | 25 Aug 2017
Clickbait title. Just a bit of brain food. Games, licenses and many other things depend on a good time source. But where does the time come from and should you trust it? -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

qRmQAZqVNxA | 20 Aug 2017
Just a quick friendly reminder. The registration closes on August 28 at 12:00 CET. RHme3: https://rhme.riscure.com/3/news rhme2 Playlist: https://www.youtube.com/playlist?list=PLhixgUqwRTjwNaT40TqIIagv3b4_bfB7M -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

qtFA-TLGd3o | 18 Aug 2017
A video from behind-the-scenes, showing what goes into making a LiveOverflow episode. Making-of in 2016: https://www.youtube.com/watch?v=sm_cgvnzJ5M -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

PPzRcZLNCPY | 11 Aug 2017
Reversing obfuscated JavaScript of a pop-under technique for Google Chrome version 60 on Windows. Chrome 60 Mac: https://bugs.chromium.org/p/chromium/issues/detail?id=752630 Chrome 60 Windows: https://bugs.chromium.org/p/chromium/issues/detail?id=752824 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #ReverseEngineering

8UqHCrGdxOM | 04 Aug 2017
In this video we figure out how to do a popunder in Chrome version 59, by using a trick. Hopefully Chrome fixes this, because I resent this kind of advertisement. PoC: https://liveoverflow.com/poc/popunder.html -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #ReverseEngineering

WWJTsKaJT_g | 28 Jul 2017
One night I ordered food and I accidentally injected a Burger into the order. The delivery guy confused a comment as another item on the order list and made it. Even though no price was attached to it. -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

KGzHcqJV-QM | 21 Jul 2017
Bruteforcing stack canary, stack guard, stack cookie with a C program. brute_cookie.c: https://github.com/LiveOverflow/liveoverflow_youtube/blob/master/0x21_0x23_modern_stack0/brute_cookie.c DigitalOcean (referral):* https://m.do.co/c/826f195e2288 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BinaryEXploitation #BufferOverflow

MMm0I2Dj51A | 14 Jul 2017
In part 2 we have a closer look at stack0 on a modern system. We are trying to plan an exploit that works in case we can guess the stack cookie. We have to be a bit creative here. stack0: https://liveoverflow.com/binary_hacking/protostar/stack0.html -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BinaryExploitation #BufferOverflow

4HxUmbOcN6Y | 07 Jul 2017
We have a look at stack level 0 from exploit-exercises.com/Protostar and compile it on a current Ubuntu, to see if it's still exploitable. stack0: https://liveoverflow.com/binary_hacking/protostar/stack0.html digitalocean referral:* https://m.do.co/c/826f195e2288 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BinaryExploitation #BufferOverflow

za_9hrq-ZuA | 30 Jun 2017
This was considered a hard challenge. After finding and analysing the source code we found a GQL injection. Unfortuantely there is a system in place that will ban you for too many requests. So we use a modified binary search algorithm to finish in time. gql.py: https://gist.github.com/LiveOverflow/16f0e4ff0ca9b0b993c25e14759de731 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #WebSecurity #CTF

0TPXvpaiYWc | 23 Jun 2017
At first I was not able to solve the mindreader challenge and then I got spoiled. I have a critical look at my approach and figured out two major mistakes I made. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #WebSecurity

6Pf3pY3GxBM | 16 Jun 2017
We perform a fault injection on an arduino board to break out of a endless loop. We drop the power for a very short amount of time so the microprocessor calculates something wrong. Skip to 0:56 if you don't want to see my cringy acting. The full verilog code: https://gist.github.com/LiveOverflow/cad0e905691ab5a8a2474d483a604d67 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #HardwareSecurity

RGknqvbhFCY | 09 Jun 2017
Generating random numbers on computers is not easy. And while the intended solution was really hard, the challenge had a problem with the random number generation, which allowed me to solve it. Clarification from Andres Moreno (riscure) on the challenge: "The "official" challenge solution involved reading the tiny Mersenne twister (tinyMT) paper, writing some equations, and using a solver. The tinyMT is tricky to initialize. Giving a proper seed is not enough. You need to provide initial state matrices with certain properties (there is a generator for this). The challenge used improper initialized matrices (zeros) that reduced the PRNG period. During tests, we found that ~12hr were needed to solve the challenge (solver time only), but we did not test the amount of entropy reduction by improper state initialization. Fortunately, the problem was not in the PRNG." -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #Cryptography

nKR44fDM_uc | 06 Jun 2017
Paul Cher and his friend Emil Lerner fuzzed FFmpeg and found several new vulnerabilities. In this podcast I'm talking with Paul about the research, how they decided to look at FFmpeg and how they fuzzed it. Podcast RSS: https://liveoverflow.libsyn.com/rss Episode: https://liveoverflow.libsyn.com/fuzzing-ffmpeg-paul-cher iTunes: https://itunes.apple.com/us/podcast/liveoverflow/id1244474599 Music by: Ozzed -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

FktI4qSjzaE | 02 Jun 2017
Terrible DPA explanation and sharing my experience solving the side channel analysis challenge "piece of scake" from the rhme2 CTF. A real DPA tutorial by Colin O'Flynn: https://www.youtube.com/watch?v=OlX-p4AGhWs The ChipWhisperer AES tutorial: http://www.newae.com/sidechannel/cwdocs/tutorial.html ChipWhsiperer: http://newae.com/tools/chipwhisperer/ The DPA paper: https://www.rambus.com/introduction-to-differential-power-analysis-and-related-attacks/ rhme2 challenge files: https://github.com/Riscure/Rhme-2016 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #HardwareSecurity

bFfyROX7V0s | 26 May 2017
Preparing an arduino nano board to perform a power analysis side channel attack and explaining how that can be used to break RSA. Also proof I can't count. RSA video: https://www.youtube.com/watch?v=sYCzu04ftaY rhme2 by riscure: http://rhme.riscure.com/home Oscilloscope: Rigol DS2072A Soldering Station: Weller WD1 -=[ 💻 Related Products ]=- → Soldering station:* https://amzn.to/2SII4du → Oscilloscope:* https://amzn.to/2SMsDAY → Cheaper Oscilloscope:* https://amzn.to/2RCzCyX -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

-UcCMjQab4w | 19 May 2017
We are going to recover a ECDSA private key from bad signatures. Same issue the Playstation 3 had that allowed it to be hacked. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #Cryptography

KhyudJNNeow | 12 May 2017
Whack the mole was a fun little challenge that was not so much about security, but to figure out how the game works, and then play it and win. Files for the challenge: https://github.com/Riscure/Rhme-2016 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #HardwareSecurity

SstD1O4_kwc | 05 May 2017
We overflow a buffer and slowly figure out that we can control memory addresses to leak other data. The challenge files: https://github.com/Riscure/Rhme-2016 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BufferOverflow #CTF

53zkBvL4ZB4 | 02 May 2017
I try to answer every question I get. Unfortunately a lot of them are extremely low effort and waste my time. I love to help, but please put some work into your question. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

fRgNtGXDMlY | 28 Apr 2017
Solving the casino challenge of rhme2 abusing a format string vulnerability. challenge sources: https://github.com/Riscure/Rhme-2016 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #FormatString

sYCzu04ftaY | 21 Apr 2017
Using the greatest common divisor (GCD) to factorize the public modulo into the secret primes, so we can forge a RSA signature. Source for the rhme2 challenges: https://github.com/Riscure/Rhme-2016 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #Cryptography

01EX0mjya5A | 14 Apr 2017
Solving "Photo Manager" from the riscure embedded hardware CTF by bypass a buffer overflow mitigation through bruteforcing a stack cookie. The challenges for your own arduino: https://github.com/Riscure/Rhme-2016 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF

RcBnhbOqDps | 07 Apr 2017
A video collaboration with Electronics Idiot to show how an electronic lock could be implemented and how it can be attacked. Electronics Idiot channel: https://www.youtube.com/channel/UCbczzZetyWR3-Uj5o-YYFMg How to build this lock: https://www.youtube.com/watch?v=7HeT4wvgz7w Sourcecode for the lock and the bruteforce code: https://gist.github.com/LiveOverflow/038875bd10e79356f4c4ed67c2efb2d5 https://github.com/ElectronicsIdiot/ArduinoLock -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #HardwareSecurity

2LOtBpA7W_M | 31 Mar 2017
This is a typical day as a pen-tester. As a professional pen-tester I wanted to share how this work really looks like and what kind of skills are required. In memory of bonkura ❤️ (1st April) Pen tester. Get it? -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

zk3JdMOQPc8 | 24 Mar 2017
We are using radare2 together with avr-gdb and simavr to reverse engineer the challenge "Jumpy" which implemets a password checking algorithm. (?s)lds r24[a-Z, 0-9;\.$^]+\n[a-Z, 0-9;\.$^│]+\n[a-Z, 0-9;\.$^│]+\n[a-Z, 0-9;\.$^│]+lds r24 Challenge files: https://github.com/Riscure/Rhme-2016 The .gdbinit from this video: https://github.com/cyrus-and/gdb-dashboard -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #ReverseEngineering #CTF

D0VKuZuuvW8 | 17 Mar 2017
We are looking at the datasheet of the ATmega328p and learn about harvard architecture and how serial communication on an assembler level looks like. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #HardwareSecurity #ReverseEngineering

xkdPjbaLngE | 12 Mar 2017
Using the webkit bug CVE-2016-4657 to start hacking the Nintedno Switch. I have taken the first part from qwerty's iOS 9.3 jailbreak and adapt it to the Nintendo Switch. We craft a Uint32Array to get a arbitrary read/write primitive. Demo at 16:19 The basic PoC: https://github.com/LiveOverflow/lo_nintendoswitch/blob/master/poc1.html Phrack article: phrack.org/papers/attacking_javascript_engines.html -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #SecurityResearch #BrowserExploitation #CVE

6QQ4kgDWQ9w | 10 Mar 2017
The first challenge I solved for the embedded hardware CTF by riscure. It implements a Secure Filesystem which prevents you from readeing files without knowing the correct token for a file. Load the challenge on your own board: https://github.com/Riscure/Rhme-2016 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #Cryptography

TM-cuV9Nd1E | 05 Mar 2017
Explaining what serial is, debugging it with a Saleae Logic Analyzer and figuring out how to talk to the board. Files for the challenges: https://github.com/Riscure/Rhme-2016 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #HardwareSecurity

FI4serDzE4w | 03 Mar 2017
Challenge files: https://github.com/Riscure/Rhme-2016 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

akCce7vSSfw | 25 Feb 2017
Just some thoughts on binary exploitation. Not sure if it makes sense :D join the discussion: https://www.reddit.com/r/LiveOverflow/comments/5w400v/developing_an_intuition_for_binary_exploitation/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

YbFwKQGJPhw | 17 Feb 2017
Showing off some examples and different ways this device can be hacked. Including a "backdoor". @dissect0r: https://twitter.com/dissect0r/status/822073775822950401 -=[ 💻 Related Products ]=- → Strontium Mobile Wifi Cloud:* https://amzn.to/2H3aYUg → i.onik WIFI Cloud Hub:* https://amzn.to/2CcI5PA -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #SecurityResearch

dbVvypaN8_k | 14 Feb 2017
Go watch Gynvael's amazing hacking livestreams: https://www.youtube.com/watch?v=ZSlJVK8DBiY Gynvael: https://www.youtube.com/GynvaelEN -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

FxE2ITDWsNE | 10 Feb 2017
Exploring a cheap embedded device and writing an exploit for it. Showing off how easy some devices can be hacked. Thanks Ligius! http://hackcorrelation.blogspot.de/ -=[ 💻 Related Products ]=- → Strontium Mobile Wifi Cloud:* https://amzn.to/2H3aYUg → i.onik WIFI Cloud Hub:* https://amzn.to/2CcI5PA -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #SecurityResearch

6D1LnMj0Yt0 | 03 Feb 2017
This challange was an amazing team effort. There were multiple steps necessary for the solution and different people contributed. The final big challenge was a bash eval injection, but without using any letters or numbers. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF

zWgS6fTw4Ts | 27 Jan 2017
Solving the babyfengshui challenge from the 33c3 CTF live on stream. exploit code: https://gist.github.com/LiveOverflow/e1f47aac7c196f8892c9383144febbe4 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #HeapOverflow #BinaryExploitation

PKbxK2JH23Y | 20 Jan 2017
Easy solution of list0r web challenge from the 33c3ctf thanks to unintended bugs in the challenge. Join the discussion: https://www.reddit.com/r/LiveOverflow/comments/5p5yci/php_include_and_bypass_ssrf_protection_with_two/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #WebSecurity

XuzuFUGuQv0 | 13 Jan 2017
Solving Eat Sleep Pwn Repeat (ESPR - 150 pwn) challenge from the 33c3ctf. Dumping the binary through a format string vulnerability, leaking libc addresses in the global offset table, finding the matching libc and overwriting printf@got with system() to get RCE. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #FormatString #BinaryExploitation

iKXd9zW1OuI | 06 Jan 2017
A more philosophical video about what it means to learn about hacking and exploitation. Using the Rubber Ducky as a scapegoat to make a point against learning tools vs. principals. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.
Lj2YRCXCBv8 | 30 Dec 2016
Had a little bit of fun using dirtycow local root exploit on a server from pwnerrank.com. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #CVE

xCEJfTfhtQc | 27 Dec 2016
Short overview on what kind of content you can find here. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

u_U6F2Kkbb0 | 23 Dec 2016
Soldering the arduino board, installing drivers for OSX and flash challenges with avrdude. The CTF will run until the end of February, the other videos will come after that. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

MBz5C9Wa6KM | 16 Dec 2016
Solving final1 from exploit.education with a format string vulnerability because of syslog(). final1: https://exploit.education/protostar/final-one/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BinaryExploitation #FormatString

HAN8Qun26cQ | 13 Dec 2016
Writing an exploit in python to solve final0 from exploit.education protostar. final0: https://exploit.education/protostar/final-zero/ exploit: https://gist.github.com/LiveOverflow/98b3586b6f8c3b744f8509326199339b -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BinaryExploitation #BufferOverflow

_shKdU7mGxs | 09 Dec 2016
Exploring exploit-exercises protostar final0 level, triggering a buffer overflow and analysing core dumps generated by a segfault signal. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

26zpUDFw5JM | 06 Dec 2016
Thank you all for your support! -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

d6BU8DWxb3c | 02 Dec 2016
Solving network level 1 with socket programming in python. protostar/net1: https://exploit.education/protostar/net-one/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #NetworkSecurity

0EHo0HsTKJw | 29 Nov 2016
Before we continue with the network challenges, let's first introduce the TCP protocol properly. Using netcat and wireshark to understand it. HTTP Protocol episode: https://www.youtube.com/watch?v=C_gZb-rNcVQ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #NetworkSecurity
2CL-AAcgyuo | 25 Nov 2016
We will learn how to daemonize a process and see how a server handles connections net0: https://exploit.education/protostar/net-zero/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #NetworkSecurity

sMla6_4Z-CQ | 22 Nov 2016
Last video from the BRUCON CTF 2016. Covering "Breaking the crypto", "Log Analysis BSQLi" and "Crypto". Topics covered: hash length extension attack, hashpump, blind sql injection, webserver access.log Filippo: https://twitter.com/FiloSottile cryptography.training: https://github.com/cryptography-training -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #Cryptography #WebSecurity

sm_cgvnzJ5M | 18 Nov 2016
A video from behind-the-scenes, showing what goes into making a LiveOverflow episode. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

HWhzH--89UQ | 15 Nov 2016
An introduction on how to abuse Heap metadata to redirect program execution. dlmalloc unlink() heap exploit to redirect code execution. heap3: https://exploit.education/protostar/heap-three/ Once upon a free() - phrack: http://phrack.org/issues/57/9.html -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BinaryExploitation #HeapOverflow

3EB4g4_6ZjI | 11 Nov 2016
Failed challenge that exposed real security issues with an anonymous mail service, and solving "Lockpicking" and "Restricted Access" from the BruCON CTF 2016. DualCore - All the Things: https://www.youtube.com/watch?v=FoUWHfh733Y -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF

bqaZBeZ4zf0 | 08 Nov 2016
BruCON CTF video write-up: Not all packets, Reverse Beer, Virtual Lockpick -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF

gL45bjQvZSU | 04 Nov 2016
An introduction on how to abuse Heap metadata to redirect program execution. heap3: https://exploit.education/protostar/heap-three/ Once upon a free() - phrack: http://phrack.org/issues/57/9.html -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BinaryExploitation #HeapOverflow

Yfsmc0b8o78 | 01 Nov 2016
Reading from the famous paper "The Confused Deputy" by Norm Hardy and make a connection to modern web vulnerabilities like XSS and CSRF. The Confused Deputy: https://www.cis.upenn.edu/~KeyKOS/ConfusedDeputy.html -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #WebSecurity #SecurityResearch

ZHghwsTRyzQ | 28 Oct 2016
Solving heap2 from exploit.education to learn about heap use-after-free (UAF) exploits heap2: https://exploit.education/protostar/heap-two/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BinaryExploitation #UseAfterFree

8ev9ZX9J45A | 25 Oct 2016
CTFs are one of the best ways to get into hacking. They require a lot of work and dedication, but are highly rewarding and teach you a lot. Here is a quick introduction on how to get started with CTFs. CTFtime: https://ctftime.org/ -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF

kEsshExn7aE | 21 Oct 2016
Video walkthrough the dirtyc0w privilege escalation exploit. Exploiting a Kernel race-condition. site: http://dirtycow.ninja/ Patch: https://git.kernel.org/cgit/linux/kernel/git/torvalds/linux.git/commit/?id=19be0eaffa3ac7d8eb6784ad9bdbc7d67ed8e619 Page Table Entry: https://www.kernel.org/doc/gorman/html/understand/understand006.html Madvise code: https://github.com/torvalds/linux/blob/5924bbecd0267d87c24110cbe2041b5075173a25/mm/madvise.c#L452 GUP code: https://github.com/torvalds/linux/blob/master/mm/gup.c -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CVE #SecurityResearch

qMEJ11jhlAc | 18 Oct 2016
State of the channel and updates Oct. 2016 Riscure embedded hardware CTF: http://rhme.riscure.com/index.php Cyberspace Camp: https://www.youtube.com/channel/UCCm0tSE3YMifM93QjqsWRJA Micah: https://www.youtube.com/channel/UCaEgw3321ct_PE4PJvdhXEQ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

JFIGpRh76XY | 14 Oct 2016
The current AngularJS version is still vulnerable to this bypass. We just had to modify the latest fixed bypass to break the incomplete fix in 1.5.7 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #WebSecurity #SecurityResearch

6cYZJLcC6Eo | 11 Oct 2016
Commented walkthrough of the security CTF Internetwache 2016. Exploitation challenges. Get DigitalOcean (referral):* https://m.do.co/c/826f195e2288 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BinaryExploitation

y69uIxU0eI8 | 06 Oct 2016
In part 1 we reverse engineered the algorithm, now we implement a radare2 script in python to recover the flag and defeat the encrypted code. The code zwiebel.py: https://gist.github.com/LiveOverflow/3bd87ba4ffc48bda07d82eb4223911fa -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #ReverseEngineering #Radare2 #CTF

LOrSbtNXBtg | 04 Oct 2016
Part 1 is about understanding the algorithm with binary.ninja and gdb. Zwiebel is a reversing CTF challenge with encrypted self-modifying code. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #ReverseEngineering

TfJrU95q1J4 | 30 Sep 2016
We are solving heap1 from exploit-exercises.com by exploiting a heap overflow. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BinaryExploitation #HeapOverflow

HPDBOhiKaD8 | 27 Sep 2016
Introducing the heap by looking at what malloc() does. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

KaEj_qZgiKY | 23 Sep 2016
What is cross site request forgery and what does it have to do wwith the same-origin policy. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #WebSecurity

Hium4FVAR5A | 19 Sep 2016
Walkthrough of the sandbox bypass for version 1.4.7 by Gareth Heyes that leads to XSS in AngularJS. mario heiderich @0x6d6172696f (https://cure53.de/) gareth heyes @garethheyes XSS without HTML: Client-Side Template Injection with AngularJS http://blog.portswigger.net/2016/01/xss-without-html-client-side-template.html An Abusive Relationship with AngularJS https://vimeo.com/165951806 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #WebSecurity

6pGEVDderN4 | 16 Sep 2016
Testing the old bypass from version 1.0.8 on a new version 1.4.7 where it's fixed, to prepare for a different bypass. mario heiderich @0x6d6172696f (https://cure53.de/) gareth heyes @garethheyes XSS without HTML: Client-Side Template Injection with AngularJS http://blog.portswigger.net/2016/01/x... An Abusive Relationship with AngularJS https://vimeo.com/165951806 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #WebSecurity

8GwVBpTgR2c | 13 Sep 2016
Showing off some cross site scripting techniques and looking at the chrome XSS Auditor -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #WebSecurity

H3rtbWQAMZ8 | 09 Sep 2016
Using the Saleae Logic Pro 8 digital analyzer to reverse engineer the packets from my air conditioner remote. NECAnalyzer code and captured trace: https://github.com/LiveOverflow/NECAnalyzer Saleae Logic Pro 8: https://www.saleae.com/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #HardwareSecurity

DkL3jaI1cj0 | 06 Sep 2016
Bypassing the AngularJS Sandbox for version 1.0.8 to get XSS. mario heiderich @0x6d6172696f (https://cure53.de/) gareth heyes @garethheyes XSS without HTML: Client-Side Template Injection with AngularJS http://blog.portswigger.net/2016/01/xss-without-html-client-side-template.html An Abusive Relationship with AngularJS https://vimeo.com/165951806 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #WebSecurity

67Yc8_Bszlk | 02 Sep 2016
Introduction to AngularJS {{expressions}}. Next videos will be about bypassing AngularJS expressions in v1.0.8 to gain XSS Try it out yourself: http://liveoverflow.com/angularjs/ mario heiderich @0x6d6172696f (https://cure53.de/) gareth heyes @garethheyes XSS without HTML: Client-Side Template Injection with AngularJS http://blog.portswigger.net/2016/01/xss-without-html-client-side-template.html An Abusive Relationship with AngularJS https://vimeo.com/165951806 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #WebSecurity

Q2mGcbkX550 | 30 Aug 2016
We learn about simple php web apps and why it's so common that php applications have XSS issues. It's all about shitty tutorials. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #WebSecurity

jTEkUay_YMU | 26 Aug 2016
Capturing the packets from my air conditioner remote to reverse engineer the protocol. Longer and way better reverse engineering video by EEVblog: https://www.youtube.com/watch?v=BUvFGTxZBG8 Jupyter Notebook: https://jupyter.org/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #HardwareSecurity

C_gZb-rNcVQ | 23 Aug 2016
We perform a HTTP GET Requesy by hand and learn how a webserver works. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #WebSecurity

jmgsgjPn1vs | 19 Aug 2016
Before we get into security stuff we have to talk a little bit about the basics of web development. A very fast introduction to HTML, CSS and JavaScript. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #WebSecurity

t1LH9D5cuK4 | 16 Aug 2016
In this episode we combine the last two videos. Format String + overwriting an entry of the Global Offset Table to solve format4 from exploit.education format4: https://exploit.education/protostar/format-four/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BinaryExploitation #FormatString
kUk5pw4w0h4 | 19 Apr 2016
In this video we will introduce how shared libraries like libc are used by C programs. Specifically we will look at the Global Offset Table and the Procedure Linkage Table. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

0WvrSfcdq1I | 09 Apr 2016
Solving format1 from exploit-exercises.com with a simple Format String vulnerability, exploited with %n. stack layout: https://www.win.tue.nl/~aeb/linux/hh/stack-layout.html format1: https://exploit.education/protostar/format-one/ CTF format string exploit: https://gist.github.com/LiveOverflow/937b659c9a37be099ddd -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BinaryExploitation #FormatString

bAlF22mIYNk | 28 Mar 2016
Commented walkthrough of the security CTF Internetwache 2016. Crypto challenges. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #Cryptography

X_PbKmZfeVo | 16 Mar 2016
Commented walkthrough of the security CTF Internetwache 2016. Web Hacking challenges. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #WebSecurity #CTF

PISoSH8KGVI | 10 Mar 2016
Part 1: reverse engineering the functionality of the cookbook binary with IDA Part 2: Leaking heap address and libc base address Part 3: Arbitrary write - House of Force exploit: https://gist.github.com/LiveOverflow/dadc75ec76a4638ab9ea -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #BinaryExploitation #HeapOverflow

dnHuZLySS6g | 09 Mar 2016
Part 1: reverse engineering the functionality of the cookbook binary with IDA Part 2: Leaking heap address and libc base address Part 3: Arbitrary write - House of Force exploit: https://gist.github.com/LiveOverflow/dadc75ec76a4638ab9ea -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #BinaryExploitation #HeapOverflow

f1wp6wza8ZI | 07 Mar 2016
Part 1: reverse engineering the functionality of the cookbook binary with IDA Part 2: Leaking heap address and libc base address Part 3: Arbitrary write - House of Force exploit: https://gist.github.com/LiveOverflow/dadc75ec76a4638ab9ea -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #ReverseEngineering #CTF

Nmoi9UoiuBM | 24 Feb 2016
First 4 levels of: http://pwnable.kr/play.php fd, collisions, bof, flag -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #BinaryExploitation

vXWHmucgZW0 | 16 Feb 2016
Learning how to reverse engineering programs written in C -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #ReverseEngineering

m17mV24TgwY | 10 Feb 2016
Solving stack6 from exploit-exercises.com with the re2libc technique. stack6: https://exploit.education/protostar/stack-six/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #StackOverflow #BinaryExploitation

HSlhY4Uy8SA | 03 Feb 2016
We write our first real exploit to get root access. Solving stack5 from exploit-exercises.com with a simple Buffer Overflow and shellcode. Run into some problems (illegal instruction): https://www.reddit.com/r/LiveOverflow/comments/54o705/found_what_i_think_is_a_slight_problem_in_the/ Stack Level 5: https://exploit.education/protostar/stack-five/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BufferOverflow #BinaryExploitation #Shellcode

8QzOC8HfOqU | 03 Feb 2016
This video shows you how to take over control of a program with a buffer overflow stack3: https://exploit.education/protostar/stack-three/ stack4: https://exploit.education/protostar/stack-four/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BufferOverflow #BinaryExploitation

T03idxny9jE | 29 Jan 2016
We will write our first Buffer Overflow for the stack0 level of exploit-exercises.com. stack0: https://exploit.education/protostar/stack-zero/ Intel Reference: intel.de/content/dam/www/public/us/en/documents/manuals/64-ia-32-architectures-software-developer-instruction-set-reference-manual-325383.pdf -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BinaryExploitation #BufferOverflow

LlSI6ErrbDI | 27 Jan 2016
Video writeup from the EFF-CTF 2016 that was running during Enigma Conference Join the discussion: https://www.reddit.com/r/LiveOverflow/comments/430csu/effctf_2016_level_04_enigma_conference/ EFF-CTF: https://eff-ctf.org Enigma Conf: https://enigma.usenix.org

Y-4WHf0of6Y | 25 Jan 2016
This video introduces https://exploit.education, how to connect to the VM with ssh and explains what setuid binaries are. Phrack: http://phrack.org/issues/49/14.html Intel Reference: http://www.intel.de/content/dam/www/public/us/en/documents/manuals/64-ia-32-architectures-software-developer-instruction-set-reference-manual-325383.pdf Putty: http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #BinaryExploitation

mT1V7IL2FHY | 22 Jan 2016
Why hexadecimal is cool and how we can convert between number systems Base 12 - Numberphile: https://www.youtube.com/watch?v=U6xJfP7-HCc -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

fLS99zJDHOc | 15 Jan 2016
We will have a look at what syscalls are and what it has to do with the kernel mode an user mode. We do this by exploring a kernel function and trace it down to the assembler level. join the discussion: https://www.reddit.com/r/LiveOverflow/comments/415sxb/0x09_syscalls_kernel_vs_user_mode_and_linux/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

OZvc-c1OLnM | 12 Jan 2016
Can programs be uncrackable? Let's try to find some anti-debugging tricks. https://www.sentinelone.com/blog/breaking-and-evading/ http://blog.ioactive.com/2012/12/striking-back-gdb-and-ida-debuggers.html?m=1 PoC||GTFO Journal # 0x00 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

qS4VWL5R_OM | 08 Jan 2016
InfoSec clickbait title by BuzzSec! Key validation with Algorithm and creating a Keygen - Part 1/2 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #ReverseEngineering
3NTXFUxcKPc | 05 Jan 2016
Exploring and comparing some common tools and techniques for reversing binaries. https://github.com/radare/radare2 -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #Radare2 #ReverseEngineering

wDosab_Y4Hs | 04 Jan 2016
Solving 'teufel' - pwnable 200 from the 32c3ctf. I didn't solve it during the CTF but worked through several writeups and doing some more research. Now that I understood it I recorded solving the challenge and recorded commentary for it. Join the discussion: https://www.reddit.com/r/LiveOverflow/comments/3ze92e/32c3ctf_teufel_pwnable_200_video_writeup/ Credits: https://github.com/ctfs/write-ups-2015/tree/master/32c3-ctf-2015/pwn/teufel-200 Vagrant: https://www.vagrantup.com/ CTF VM: https://github.com/thebarbershopper/ctf-vagrant-64 Hopper: http://www.hopperapp.com/ ROPGadget: https://github.com/JonathanSalwan/ROPgadget -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #BinaryExploitation #ROP #BufferOverflow

wLsckMfScOg | 31 Dec 2015
Solving the readme pwnable 200 from the 32c3 ctf. I didn't solve it during the CTF but worked through several writeups and doing some more research. Now that I understood it I recorded solving the challenge again and recorded a commentary for it. CORRECTION: I explained the stack canary with the `fs` register wrong. The `fs` register has an address and the stack canary is stored at offset +0x28 from that address. Stack Layout for an ELF program: https://www.win.tue.nl/~aeb/linux/hh/stack-layout.html Credits: https://github.com/ctfs/write-ups-2015/tree/master/32c3-ctf-2015/pwn/readme-200 Vagrant: https://www.vagrantup.com/ CTF VM: https://github.com/thebarbershopper/ctf-vagrant-64 BinaryNinja: https://binary.ninja -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF #BufferOverflow #BinaryExploitation

VroEiMOJPm8 | 29 Dec 2015
A very simple reversing challenge for Linux GitHub: https://github.com/LiveOverflow/liveoverflow_youtube/tree/master/0x05_simple_crackme_intro_assembler http://crackmes.de http://www.hopperapp.com/ https://www.hex-rays.com/products/ida/ https://github.com/radare/radare2 -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #ReverseEngineering

6jSKldt7Eqs | 24 Dec 2015
How a CPU works. An introduction to reading assembler instructions. https://microcorruption.com/ -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #ReverseEngineering

rDU35RjLctc | 22 Dec 2015
Recording from streaming live overthewire.org Vortex level 0x01 - 0x03 Also thanks to https://binary.ninja/ for beta access! -- Watch live at http://www.twitch.tv/liveoverflow -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #CTF

ajy1PHWYeyQ | 21 Dec 2015
Just a super quick introduction into python programming. codecademy Python course: https://www.codecademy.com/learn/python -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #Programming

JGoUaCmMNpE | 17 Dec 2015
A fast introduction into programming with C. -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm. #Programming

iyAyN3GFM7A | 14 Dec 2015
A little bit of background why I created this channel and what you can expect. -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.

navuBR4aJSs | 14 Dec 2015
Installing Ubuntu Linux in a VM and introduction to the command-line. Ubuntu: http://www.ubuntu.com/download/desktop VMWare Player: https://www.vmware.com/products/player VirtualBox: https://www.virtualbox.org/ Everything is a file: https://en.wikipedia.org/wiki/Everything_is_a_file dotfiles: https://plus.google.com/+RobPikeTheHuman/posts/R58WgWwN9jp -=[ 🔴 Stuff I use ]=- → Microphone:* https://geni.us/ntg3b → Graphics tablet:* https://geni.us/wacom-intuos → Camera#1 for streaming:* https://geni.us/sony-camera → Lens for streaming:* https://geni.us/sony-lense → Connect Camera#1 to PC:* https://geni.us/cam-link → Keyboard:* https://geni.us/mech-keyboard → Old Microphone:* https://geni.us/mic-at2020usb US Store Front:* https://www.amazon.com/shop/liveoverflow -=[ ❤️ Support ]=- → per Video: https://www.patreon.com/join/liveoverflow → per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join -=[ 🐕 Social ]=- → Twitter: https://twitter.com/LiveOverflow/ → Website: https://liveoverflow.com/ → Subreddit: https://www.reddit.com/r/LiveOverflow/ → Facebook: https://www.facebook.com/LiveOverflow/ -=[ 📄 P.S. ]=- All links with "*" are affiliate links. LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.



